Immediate Threats Solution Overview
Every day, new threat activity is identified and tracked throughout the cybersecurity community. Each new activitymay have a different priority, impact different systems, and be compensated against in multiple ways.
The Cymulate Research team actively monitors and collaborates with the industry to prepare and test for emergent threats. With over 120,000 active test scenarios, the Cymulate Platform is continuously updated so that organizations can quickly and safely test security controls against new and emergent threats. Technical and business reporting summarize whether security controls have identified indicators of threat and have acted as expected.
Immediate Threats Challenges
Every day, emerging threats bring unanswered questions
Threat Assessment Check
Threat Assessment Check
Is our infrastructure exposed to this new threat?
Impact Analysis
Impact Analysis
What would be the impact of an attack using this new exploit, technique, etc.?
Threat Readiness
Threat Readiness
Are the detection and response solutions capable of identifying and stopping the new threat?
Immediate Remediation
Immediate Remediation
What needs to be done immediately to protect networks/applications
/systems?
Resource Allocation
Resource Allocation
What resources must be diverted to address the emergent threat?
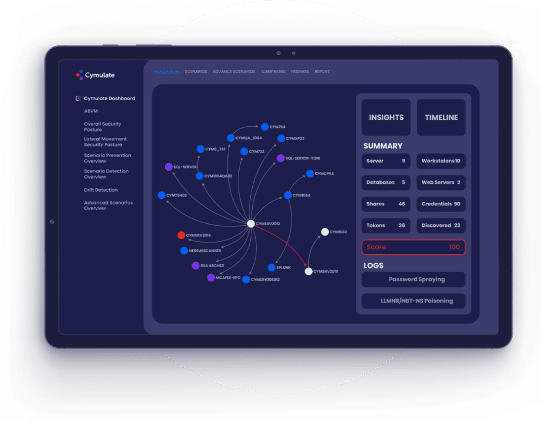
Cymulate Immediate
Threat Intelligence
The Cymulate Threat Research Group provides daily simulations
of new threats, making them immediately available for customers
to test safely. Immediate Threats Intelligence highlights where
defenses are strong, and where gaps against emergent threats
exist which require remediation.
Fully automated and schedulable, Cymulate Immediate Threat
Intelligence allows customers to select immediate threats
individually, by type, or globally, and run the assessment with
a click and to automatically run simulations each time a new
emergent threat is updated in the system.
Automated report generation provides customizable reports
for executive and technical levels, customizable for use by
all stakeholders.
With the information provided, remediation teams can focus
their efforts on fixing issues without investing time in research
or allocating resources where defenses are already adequate
and capable of repelling the threat.
Immediate Threat Analysis with Cymulate
The Benefits of Cymulate Immediate Threat Testing
Up-To-Date
Update with new threat activity regularly – typically daily – to allow for testing against emergent activity

Comprehensive
Simulations assess email gateways, endpoint defenses, and Internet defenses and controls

Safe
Designed from start to finish to be used in production environments without incurring risk to business operations or endangering assets

Learn More About Cymulate
Immediate Threat Testing
Overview of how Cymulate tests and prepares organizations
for emergent threats.
Backed By the Industry
Frequently, our CISO or senior members come to security operations asking if we are at risk from a new threat or APT group in the news? Cymulate enables us to answer quickly and confidently.
Karl Ward, Lead security operations
analyst, Quilter






“Cymulate has been helping me to evaluate my security posture against behavior based as well zero day threats.”
– IT Security & Risk Management Associate
“Technical capabilities provided are outstanding, customer service is highly responsive and product mgmt. is flexible in supporting us with our requests.”
– Security Operations Analyst
“The Cymulate BAS is delivering excellent outcomes, contributing significantly to enhancing my security effectiveness.”
– IT Security & Risk Management Associate
“My experience with the platform was exceptional. It delivers on its promises with easy navigation, effective mitigation steps, and top-notch after sales support.”
– Chief Risk Manager
“Always willing to help offering training sessions and encourage use of the product’s additional available features.”
– Senior Software Engineer
“I believe that Cymulate brings a vision of risks, vulnerabilities and actions that we are unable to pay attention to in our work day.”
– Security Operations Specialist
“The range and breadth of attack scenarios, potential targets and how well each tool integrates is really excellent.”
– Penetration Tester
“We had an excellent experience with Cymulate, from product deployment to while using the platform.”
– Senior Cybersecurity Engineer
“Awesome customer Support and techniques used by Cymulate to identify security gaps.”
– IT Security & Risk Management