2024 was a year that saw some of the biggest and most damaging data breaches in recent history, according to TechCrunch. The worst data breaches of 2024 surpassed one billion stolen records. With data like that, cybersecurity leaders must reevaluate how they do their budgets going into 2025 and beyond.
Between the rapid expansion of digital transformation, new daily regulations and the significant increase in sophisticated cyber attacks, budgets now need to accommodate for everything and anything at any given time.
The Increasing Need for an Effective Cybersecurity Budget Strategy
Setting an effective and prepared cybersecurity budget starts with a holistic and comprehensive outlook on your organization’s overall cybersecurity strategy. All industries are vulnerable to an attack of any kind, with some more targeted than others, like healthcare, finance and government. An example of this is the Kaiser Permanente data breach that occurred in April 2024 that impacted 13.4 million of their current and former members and patients’ information being compromised.1
A data breach or cyber attack can have severe financial and reputational consequences for an organization now, making cybersecurity spending an essential and strategic investment and spend, no longer just a cost center. Financial impacts can include loss of immediate revenue and clients due to an attack and any regulatory fines applied by not meeting the consistently tightening data protection and cybersecurity practices like the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA).
Choosing the Right Cybersecurity Budget in 2025
Every organization will face their own unique risks based on the industry, size and digital infrastructure. One-size-fits-all approach no longer applies to cybersecurity budgeting in 2025. Factors to consider include the following:
- Company size: Larger enterprises may require broader, more substantial investments due to their broader attack surface, more endpoints, diverse IT environments (e.g., multi-cloud, hybrid) and larger workforce. They may also need enterprise-level security solutions such as Security Information and Event Management (SIEM), threat intelligence and dedicated security operations centers (SOCs).
Smaller to medium-sized businesses (SMBs) may need to be more strategic about their spending based on priority and critical needs. The focus should be on addressing immediate threats and risks as well as scalable SIEM solutions and cost-effective managed security services (MSSPs) or cloud security tools. - Industry-specific needs: Each industry will be driven by the nature of its own data and regulatory landscape. It is critical to customize your funding needs to meet the distinctive needs of your industry. Healthcare for example, is a prime target for cybercriminals due to the sensitive nature of patient data and vast amount of financial and regulatory damage one ransomware incident could cause. Following the Health Insurance Portability and Accountability Act (HIPAA) closely and allocating appropriate funding to meet compliance requirements can save your organization from making front-page news.
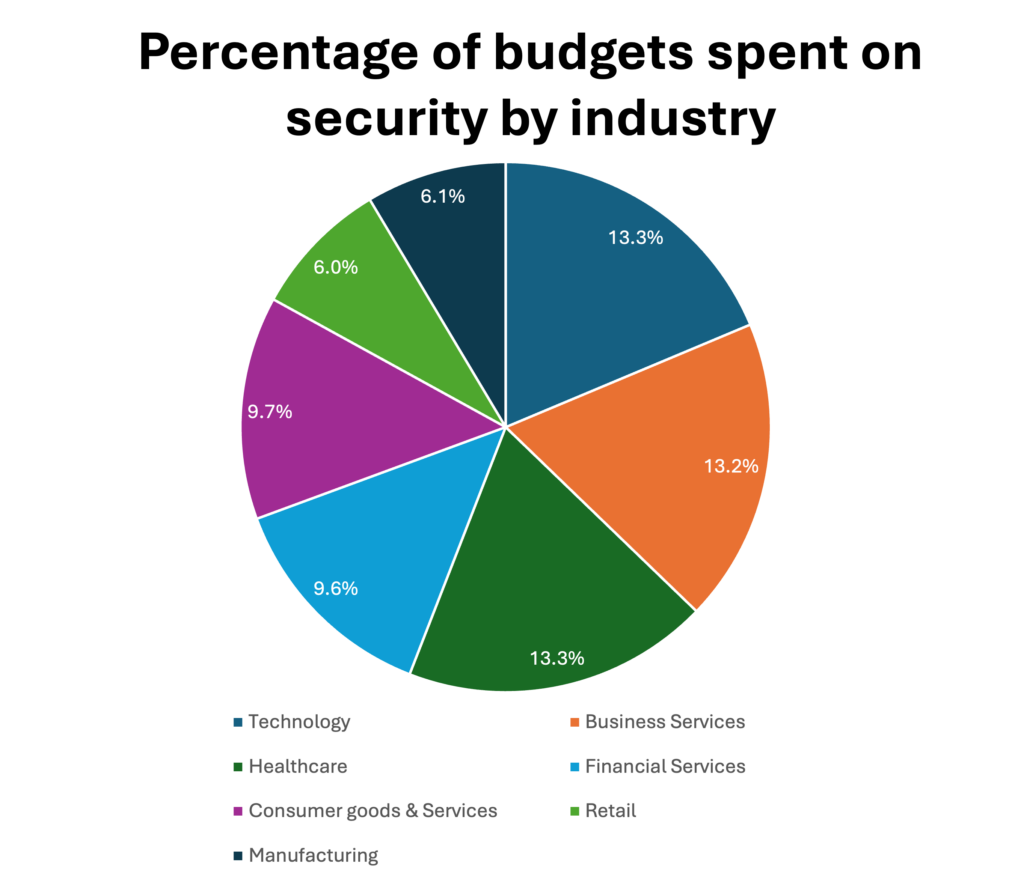
- Risk profile: Assessing a company’s risk profile is one of the most significant determinants of how much you should invest in cybersecurity. Some businesses face higher levels of risk than others due to their structure, industry, size, geographical location and technological infrastructure.
- Higher-risk businesses include remote work, the Internet of Things (IoT) or cloud. This is because companies with large remote workforces or rely heavily on IoT devices, such as manufacturing or transportation face increased exposure vulnerabilities. Security measures like network segmentation, endpoint detection and response (EDR) and cloud security posture management (CSPM) solutions become necessities.
- Lower-risk businesses that have fewer connected devices or might work with less sensitive data may not face as many direct cyber risks but will always need basic protections. For those companies and industries, prioritizing cost-effective solutions like firewalls, antivirus software and continuous employee training may suffice.
- Compliance requirements: Most industries must comply with complex regulatory and compliance requirements. Although these standards are intended to ensure that companies take not only appropriate actions to protect data and maintain integrity, but that they take any necessary steps quickly in the event of failing to meet a guideline. Failing to meet compliance standards can lead to severe financial penalties, legal costs and reputational damage.
- Common frameworks that companies must budget for in 2025 include:
- ISO 27001 – a global standard that sets out the requirements for an Information Security Management System (ISMS).
- NIST – National Institute of Standards and Technology provides a set of best practices and guidelines for securing critical infrastructure focusing on identifying, protecting, detecting, responding to and recovering from cyber threats.
- PCI DSS – Any business that handles payment card data will need to comply with this framework and the cost will vary depending on organization size.
- Common frameworks that companies must budget for in 2025 include:
Cybersecurity Budget Breakdown – How Much Should You Spend?
Cybersecurity has become an integral part of every organization’s risk management strategy, but the question remains: How much should companies spend on cybersecurity? The answer will vary greatly depending on the factors covered above, however setting some benchmarks against industry standards is a good place to start.
Organizational size
- Small (Fewer than 100 employees): Small organizations typically allocate between 4% to 10% of their IT budget to cybersecurity. An example could be if a business had an IT budget of $100,000, they would allocate $4,000-$10,000 on cybersecurity annually.
- Medium (100-1,000 employees): Medium-sized businesses typically allocate 8% to 15% of their IT budget. For example, if a business’s IT budget was $500,000, their annual cybersecurity spend would be $40,000-$75,000.
- Large (1,000+ employees): Large organizations usually dedicate 10% to 20% of their IT budget to cybersecurity. For a large enterprise with an IT budget of $10 million, it would translate to an annual cybersecurity spend of $1 million to $2 million.
Technology
Technology investments are the keystone of every cybersecurity strategy, providing the tools needed to detect, block, respond to and monitor cyber threats. Key tools like firewalls, web application firewalls (WAFs), endpoint detection and response (EDR) solutions and cloud security tools should all be on your priority list of investments.
Artificial Intelligence (AI) and machine learning (ML) are becoming core integrations in cybersecurity strategies and solutions to help organizations detect and respond to threats faster than ever before.
- Small businesses may allocate 15-30% of their cybersecurity budget to technology.
- Medium-sized businesses typically allocate 30-50% of their cybersecurity budget on technology.
- Large enterprises may invest 40-60% in cybersecurity technology.
Personnel
Skilled professionals have made talent acquisition and retention a major challenge and component of cybersecurity budgets, especially when a skills gap remains a critical issue.
- Small businesses could spend approximately 10-20% of their cyber budges on personnel, including external resources and consultants.
- Medium businesses could allocate 20-40% of their budgets to hiring internal skilled cyber professionals and training.
- Large enterprises make significant investments in their security teams, often dedicating 30-50% of their budgets to salaries, training and management.
Managed Security Service Providers (MSSPs)
MSSPs are especially helpful and popular among small and medium-sized businesses (SMBs) that might not have the internal resources to maintain in-house security operations. MSSPs offer a wide variety of services, including 24/7 customer service, monitoring, incident response and threat intelligence, all without the cost of carrying specialists in each of those areas.
- Small businesses may spend 20-40% of their cybersecurity budget on MSSPs.
- Medium-sized businesses typically allocate 10-30% to MSSPs, especially for continuous monitoring and incident response.
- Large enterprises could allocate 5-15% to MSSPs – this is much lower due to the inhouse capacity.
Continuous validation and threat simulation
Cyber attacks are growing more complex and costly making ongoing validation and testing an essential part of a strategic defense. Defenses include red team exercises simulating real-world attacks to test an organization’s security posture, exactly like what Cymulate offers. Threat simulation of ransomware and data breaches are another way for an organization to quickly understand how they can detect and respond.
- Small businesses typically spend 5-10% of their budget on testing and validation tools.
- Medium-sized businesses could allocate 10-15% for regular penetration testing, red team exercises and security validation.
- Large enterprises often allocate 10-20% of their cybersecurity budgets to testing, including continuous simulation and threat validation.
Maximizing Your Cybersecurity ROI
When structured correctly, cybersecurity can be seen as much more than an expensive necessity. It can and should be seen as a worthwhile and needed investment in order to protect your organization from the constantly evolving daily threats of attacks in all forms. Simulating attacks in real-time and the ability to validate them is no longer a futuristic goal but a technological advance available now with Cymulate. Additional key areas of investment include:
- Automation: Many cybersecurity tasks are repetitive and rely on manual participation, which introduces delays, mistakes and inefficiencies. Automation increases response time to incidents, improves threat detection and reduces operational and resource costs. Vulnerability alerts and patch management should be considered for automation.
- Validation: To ensure your security controls are protecting your assets as intended, validation is a must. Platforms like Cymulate that offers a real-life cyberattack simulation can assess your environment’s readiness against potential threats. Regular testing of your security stack helps identify vulnerabilities before they become exploited by real-world attacks.
- Incident response (IR): It is no longer a matter of if, but when regarding when an organization of any size could find themselves in a cyberattack. Focusing on reducing recovery time and cost, communication, mitigating financial impact and reputational damage are all crucial areas of incident response. A dedicated IR platform, automated detection, incident tracking and post-analysis will be integral players.
- Leverage open-source tools: High-quality, open-source tools are available at no cost or at a significantly lower price than proprietary software. These tools often require more customization and maintenance, however, are highly effective in vulnerability scanning, intrusion detection and network monitoring. Examples of these tools are: Snort or Suricata, OSSEC, OpenVAS and Wireshark.
- Regularly assess and retire underperforming tools: In such a fast-paced industry, tools quickly evolve and become redundant. Doing sporadic evaluations of the effectiveness of your security tools checks for performance indicators like ease of use, performance, accuracy and cost comparisons. If a tool no longer meets your organization’s needs, look to consolidate or replace it with a more advanced solution.
Key Takeaways
Organizations are facing increasingly sophisticated cyber threats; the importance of a well-structured and optimized cybersecurity budget can’t be overstated. In 2025, cybersecurity is not just about spending more money but about spending it wisely.
Prioritizing investments in risk management, talent acquisition, the right technology, and compliance will allow organizations to build a resilient security posture that aligns with their business objectives and risk profile.
By carefully evaluating these factors and aligning your cybersecurity budget with your company’s unique needs and risks, you’ll be better positioned to protect your organization against evolving cyber threats and achieve long-term security and compliance goals.
To learn more about how Cymulate can help your organizational leaders prepare their strategic budgets for 2025 with the most modern technological validation tools, contact us today for a demo.
Resources:











