
April 17th, 2024
The Move from Vulnerability to Exposure Management

April 9th, 2024
Threat Exposure Management: Implementation Of Best Practices

April 2nd, 2024
Navigating the Rising Tide of Data Exfiltration

March 26th, 2024
Threat Exposure Management: A Shift in Strategy

March 19th, 2024
What Goes Around Comes Around: How to Protect Yourself Against Evolving Threats

March 12th, 2024
Cymulate Research Highlights the Path to Proactive Security

March 6th, 2024
Threat Exposure Management: Continuous Monitoring and On-Going Assessment

February 29th, 2024
Introduction to Threat Exposure Management and its Outcomes
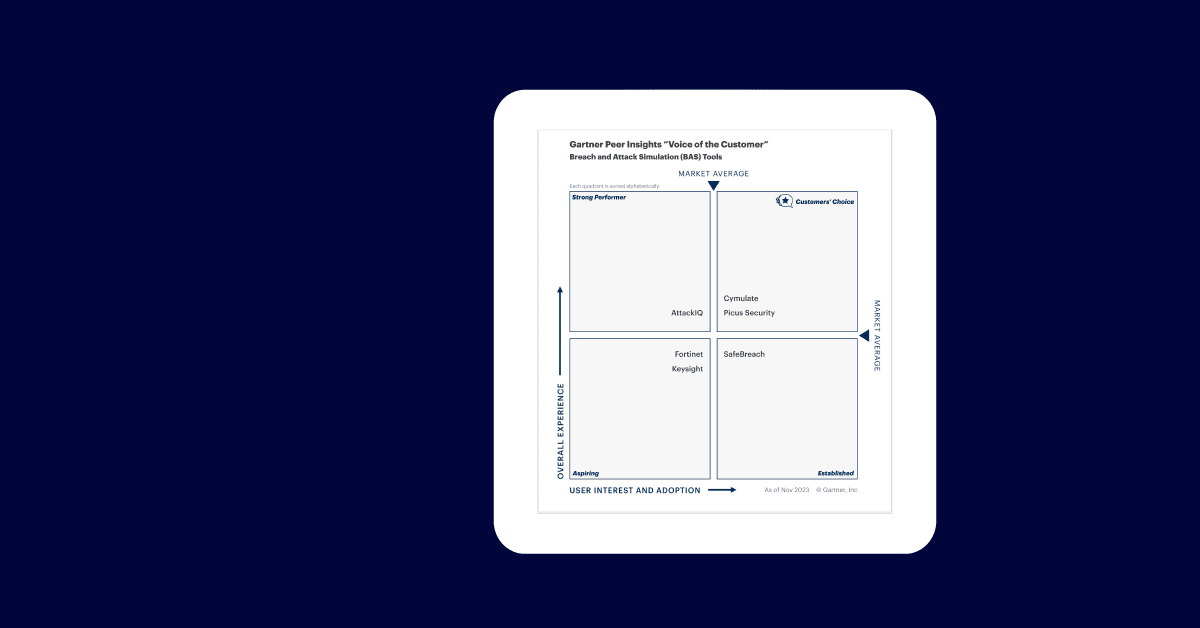
February 26th, 2024
Cymulate Named a Customers’ Choice by Gartner® Peer Insights™ 2024 VOC

February 22nd, 2024









