Automated Testing to Validate Attack Paths for Repeatable & Scalable Assessments
Simulate an attacker that has gained an initial foothold and moves
laterally in search of any additional assets that can be compromised
Validate security controls and response against real-world cyber
attacks to stress test defenses and identify gaps
Create and run internal phishing campaigns to measure employee
resilience against phishing attacks
Benefits of Continuous Automated Red Teaming

Automated Testing
Scheduled & automated assessments for testing on demand & reducing repetitive, labor-intensive manual tasks

Customization
The ability to create, modify & run chained or atomic attack campaigns

Continuous Validation
Repeat assessments to validate mitigations & identify drift

Reduced Risk
Clear steps to remediate, close gaps & reduce exposure
Capabilities
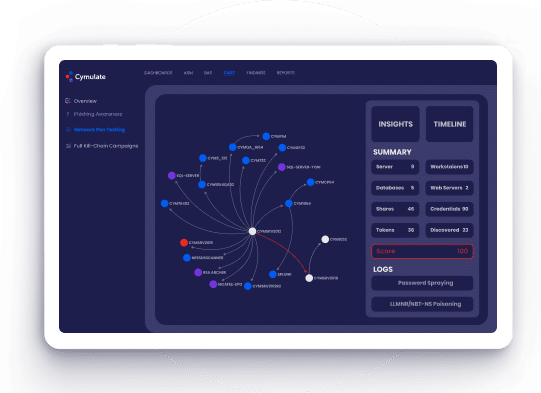
Network Pen Testing
- Safely apply threat tactics and techniques to uncover
infrastructure misconfigurations and security weaknesses - Validate attack paths against security controls
- Segregate network-level defenses from endpoint-level
defenses for a more accurate analysis of both layers of controls - Identify changes in IT infrastructure and network
misconfigurations that provide new avenues for lateral
movement
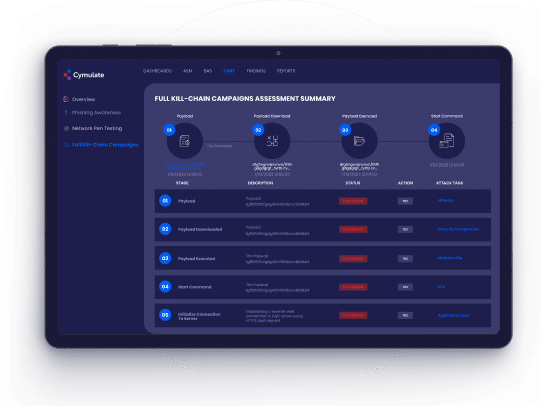
Full Kill-Chain Assessments
- Automate security testing with real-world cyber attacks
with attack delivery, exploitation, and post-exploitation - Target users via email with production-safe payloads that
include code execution and evasion techniques that
simulate ransomware, trojans, worms, lateral movement,
and more - Control each step of the attack and each technique to
ensure safety
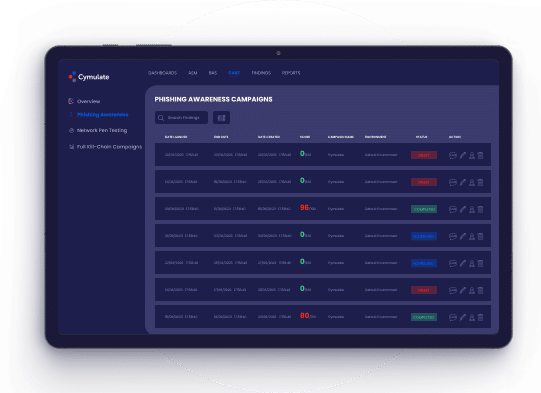
Phishing Awareness
- Measure employee resilience against phishing attacks with
actual phishing and malicious span (malspam) attack
methods - Record employee interactions with mock phishing
emails - Identify employees who need additional phishing awareness
training and highlights users who are not following proper
policies and procedures
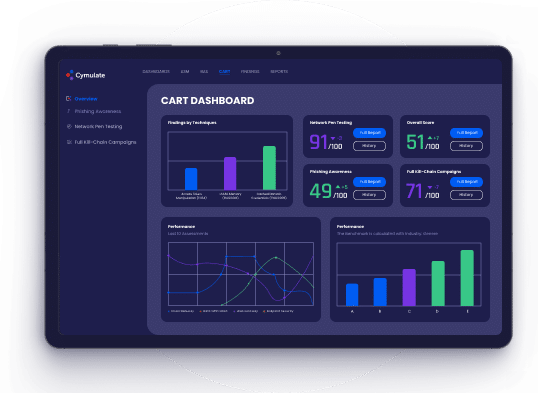
Actionable Reporting
- Share findings and measure security posture with
technical and executive reports - Create custom dashboards and reporting
- Map reporting to MITRE ATT&CK® and other
frameworks
Cymulate Continuous Automated Red Teaming
Scalable
Scalable
Automated testing to reduce repetitive, labor-intensive manual tasks and increase productivity
Extensive
Extensive
Network pen testing, phishing awareness, and full kill-chain campaigns
Comprehensive
Comprehensive
Supports automated testing for vulnerability validation, what-if scenarios, targeted, and custom testing
Easy
Easy
Deploys with ease, customizable, and runs ongoing non-disruptive assessments
Environments

On-premises
- Physical and Virtual
- Desktops and Servers
- People, Process, and Technology

Cloud
- Instances, Serverless*, Containers* *When used with BAS
- Intra- and Inter-Connected Networks

Hybrid
- VPN Connectivity
- Shared Services
- Cloud Storage

Windows
- Desktop
- Servers
- Virtual

Linux
- RedHat
- Debian
- Forked Distribution

MacOS
- Intel
- Apple Silicon
- 10.13 and higher
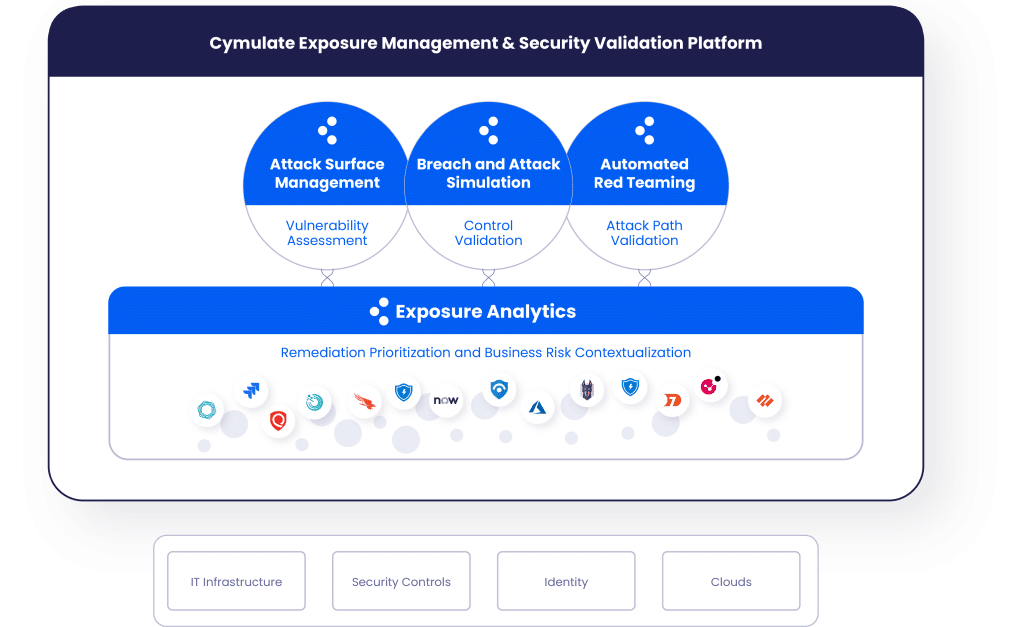
The Cymulate Exposure Management & Security Validation Platform
Cymulate Continuous Automated Red Teaming is available both as a standalone SaaS offering and as an
integrated offering within the Cymulate Exposure Management and Security Validation Platform.
Backed by the Industry
Cymulate Recognized as Top Innovation Leader
F&S recognized in their Frost RadarTM Global BAS, 2022 report
Related Resources
Continuous Automated Red Teaming FAQs
CART adds automation and continuous testing to traditional red team exercises to validate entire attack paths from infiltration to actions on objectives. This proactive approach to security testing involves regularly automating and simulating real-world attacks on an organization’s systems and applications. The simulations attempt to breach an organization by autonomously deploying attack techniques that penetrate and gain an initial foothold within the network.
Cymulate CART is cloud-based and can be accessed through a web browser, only needing one agent per environment, eliminating the necessity for any on-premises installation. Cymulate CART simulates attacks that can propagate within the network in search of critical information or assets, providing for network penetration testing. Cymulate CART can test any technique on any stage of the kill-chain independently.
BAS and CART are two different approaches to security testing. BAS tests the effectiveness of security controls against known attack vectors, while CART focuses on if and how an adversary can breach an organization’s defenses by identifying and addressing vulnerabilities. BAS testing is typically limited to specific areas of the network or specific applications, and CART testing covers the entire attack surface of an organization’s systems and applications. Organizations that combine these two approaches can gain a more comprehensive view of their security posture.
Cymulate CART provides reusable templates for baselining and ongoing testing, as well as land-and-pivot lateral movement, for more accurate and detailed results. Security teams can also create customized attacks, from infiltration to actions on objectives. Additionally, the phishing assessment capability provides all the resources to create an internal phishing campaign and measure employee resilience against phishing attacks. With Cymulate CART, security teams can test more environments, more often, without increasing their staff.
Traditional penetration testing services typically involve a one-time assessment of an organization’s security posture. Cymulate CART provides ongoing, continuous, and automated assessments that validate entire attack paths from infiltration to actions on objectives. This allows businesses to identify and remediate vulnerabilities in real-time rather than waiting for an annual or bi-annual assessment.
With Cymulate CART, red teams utilize automation and highly customizable simulations to increase their operational efficiency and optimize their adversarial activities in a production-safe environment. Cymulate CART also provides blue teams a framework to improve adversarial skills on the job, increase collaboration, and improve time to mitigation. In the face of budget cuts and the shortage of security professionals, Cymulate CART enables security teams to maximize their impact.