Solutions

Challenge
Email security controls that prevent ransomware, worms, trojans and other email borne attacks by launching thousands of crafted email attacks with malicious attachments and links.

Assess
Email security and policy enforcement, including allowed file types and true file detection.

Optimize
Email security controls that block or remove malicious links and attachments including Email G/W, Content Disarm and Reconstruction (CDR), Sandboxing and other email security technologies.
Benefits
Validate the effectiveness of
your email security controls against
threat evolutions and stop attacks in
the pre-exploitation stage.
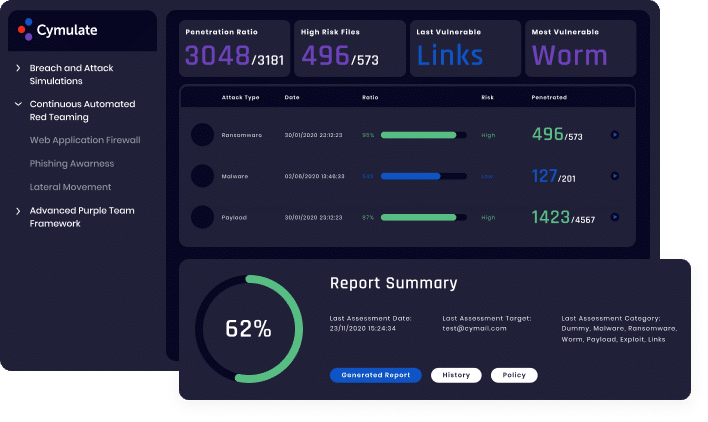
- Track email-security effectiveness over time and prevent security drift
- Find, prioritize, and fix security gaps against an exhaustive and continuously updated library of attacks
- Fine tune email security policies to block non-essential and abuseable file types
- Benchmark your email security performance against industry peers
- Safe to run in production
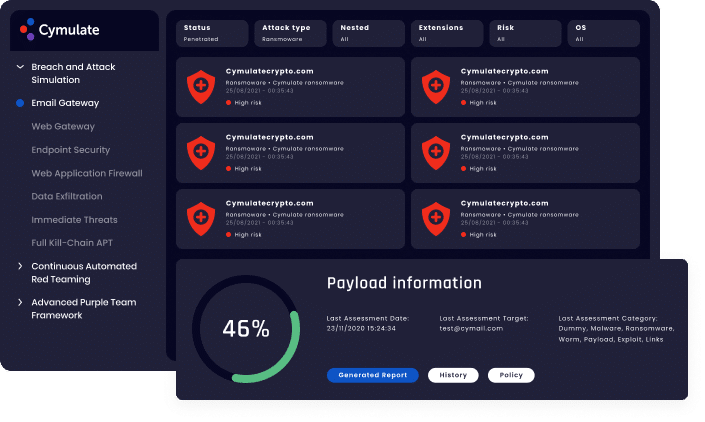
Email Gateway Vector
For example, a recurring DHL themed phishing template used during the holiday season spreads different malicious payloads such as Tesla, Panda, Ursnif etc. One recent example of this method used a DHL themed shipment invoice sent by email, notifying its victims that there is a new shipment waiting for them. Victims that click on the link or open attachments download a dropper that links to the attacker’s C&C server downloading malware to the victim’s endpoint, thus compromising it, and in some cases even compromising the whole organization.
Organizations utilize different security controls, such as Secure Email Gateways (SEGs), Sandbox, and Content Disarm and Reconstruction (CDR) solutions to protect their employees’ mailboxes. However, their incorrect configuration or implementation can lead to the false assumption that an organization is safe.
Cymulate’s Email Gateway vector evaluates your organization’s email security and potential exposure to malicious payloads and links sent by email.
Learn More
More Attack Vectors and Modules

Web Gateway
Validate your defenses against malicious inbound and outbound web browsing and command and control.

Web App Firewall
Validate your defenses against web application attacks, including OWASP top ten.
Endpoint Security
Validate detection and prevention of endpoint ATT&CK TTPs including ransomware, worms, and more.

Lateral Movement
From an initial foothold propagate within the network to find critical assets.

Data Exfiltration
Validate that sensitive and critical data cannot be exfiltrated from the organization.

Immediate Threats
Validate your defenses against the latest cyber-attacks found in the wild, updated daily.

Full Kill-Chain APT
Validate your defenses against APT attack scenarios e.g., Fin8, APT38, Lazarus and custom scenarios.