Case Study
April 11th, 2024
Rapid Cybersecurity Transformation: A Multinational’s Success with Cymulate
Case Study Discover the success story of a leading IT…
Case Study
March 28th, 2024
RBI Validates and Optimizes SIEM Detection with Cymulate
Case Study In the face of escalating cyber threats, Raiffeisen…

Case Study
March 10th, 2024
Banco PAN Optimizes Security Controls and Validates Group Policy Objects with Cymulate
Case Study Banco PAN aims for cybersecurity excellence beyond mere…

Report
March 6th, 2024
2024 State of Exposure Management & Security Validation
Cymulate Research The 2024 State of Exposure Management & Security…

Case Study
February 28th, 2024
Cymulate Empowers Globeleq with In-house Security & Threat Validation
Case Study Globeleq, an independent power company which owns, operates,…

Solution Brief
February 28th, 2024
Exposure Management
Solution Brief Security experts are starting to understand that traditional…

Webinar
February 28th, 2024
Cloud Detection Engineering: Adopting an Assumed Breach Mindset
Webinar Today’s cloud security recognizes that breaches are inevitable. You…

Report
February 26th, 2024
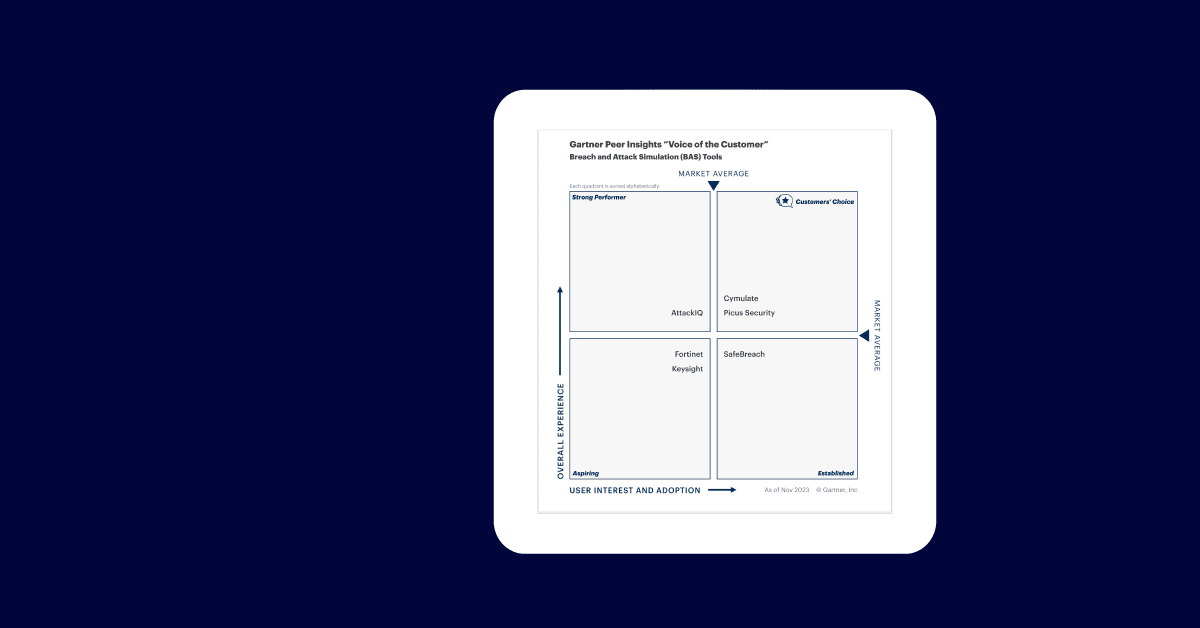
Cymulate Named a Customer’s Choice by Gartner® Peer Insights™ 2024 VOC for BAS Tools
Report In a noisy industry landscape, there is always one…

eBook
February 20th, 2024
Threat Exposure Management – A TAG Senior Analyst eBook
eBook Compared to the reactive nature of typical vulnerability handling,…

Solution Brief
February 15th, 2024
Cloud Detection Engineering
Solution Brief As more organizations rely on Cloud computing, the…

eBook
January 30th, 2024
A Practical Guide
to Exposure Management
eBook The question, “How exposed are our assets right now,”…

Case Study
January 18th, 2024
LV= Takes a Data-Driven Approach to Cybersecurity with Cymulate
Case Study LV=, a financial services company, had the necessary…
Report
January 9th, 2024
Native Cloud Defense Mechanisms Vs. Kubernetes Attacks
Report While revolutionizing the world of DevOps, the advent of…

Video
December 24th, 2023
TAG Infosphere Interview with Cymulate CSO Andrew Barnett
Video Cymulate CSO Andrew Barnett sat down with TAG…

Webinar
December 21st, 2023
December Threat Research Lab Update – Top Threats
Webinar This month Mike and Dan take on recent cyberthreats…

Whitepaper
December 3rd, 2023
Continuous Threat Exposure Management (CTEM): From Theory to Implementation
Whitepaper Translate cyber risk into language that leadership can use…
Webinar
November 26th, 2023
Red Teaming – Automate What You Can
Webinar Traditional red-teams have evolved to keep up with changes…

Webinar
November 26th, 2023
How to Prove You Have a Resilient Security Program
Webinar Every year, organizations spend millions on cybersecurity. But many…

Webinar
November 10th, 2023
November Threat Research Lab Update – Everything Old is New Again
Webinar November’s Threat Research Lab Update explores well-understood attack tactics…

Report
November 7th, 2023
Tag Cyber Report: Revolutionizing Cyber Defense – An Integrated Approach with Cymulate MITRE Frameworks
Report This joint technical report from TAG Cyber and Cymulate…