Case Study
April 11th, 2024
Rapid Cybersecurity Transformation: A Multinational’s Success with Cymulate
Case Study Discover the success story of a leading IT…
Case Study
March 28th, 2024
RBI Validates and Optimizes SIEM Detection with Cymulate
Case Study In the face of escalating cyber threats, Raiffeisen…

Case Study
March 10th, 2024
Banco PAN Optimizes Security Controls and Validates Group Policy Objects with Cymulate
Case Study Banco PAN aims for cybersecurity excellence beyond mere…

Report
March 6th, 2024
2024 State of Exposure Management & Security Validation
Cymulate Research The 2024 State of Exposure Management & Security…

Case Study
February 28th, 2024
Cymulate Empowers Globeleq with In-house Security & Threat Validation
Case Study Globeleq, an independent power company which owns, operates,…

Solution Brief
February 28th, 2024
Exposure Management
Solution Brief Security experts are starting to understand that traditional…

Webinar
February 28th, 2024
Cloud Detection Engineering: Adopting an Assumed Breach Mindset
Webinar Today’s cloud security recognizes that breaches are inevitable. You…

Report
February 26th, 2024
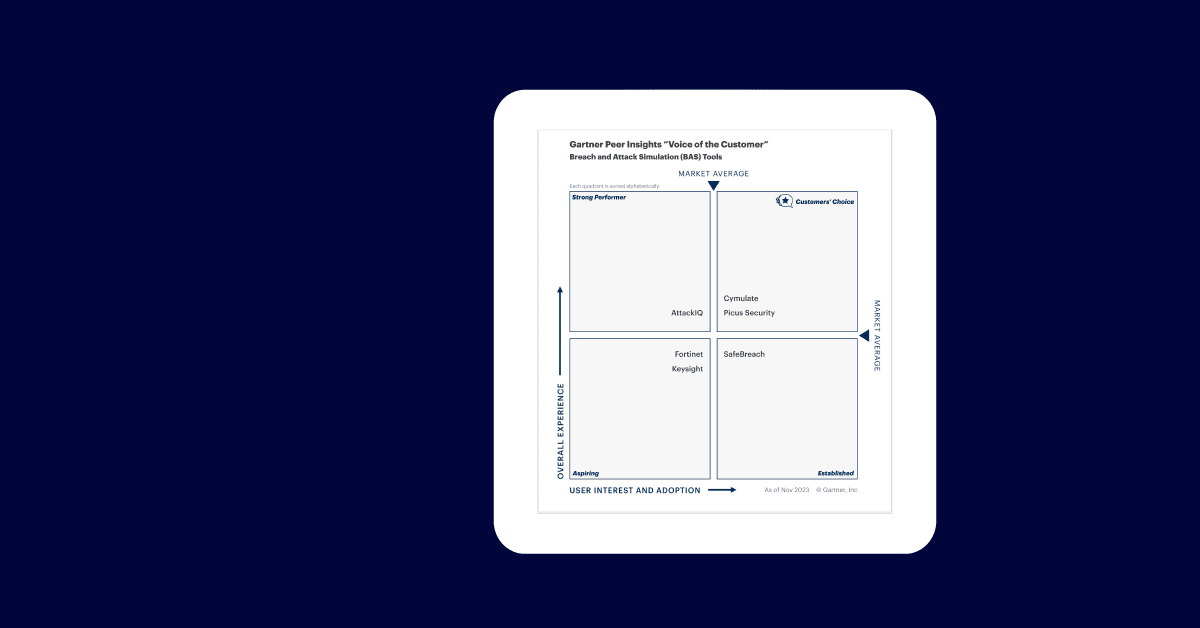
Cymulate Named a Customer’s Choice by Gartner® Peer Insights™ 2024 VOC for BAS Tools
Report In a noisy industry landscape, there is always one…

eBook
February 20th, 2024
Threat Exposure Management – A TAG Senior Analyst eBook
eBook Compared to the reactive nature of typical vulnerability handling,…

Solution Brief
February 15th, 2024
Cloud Detection Engineering
Solution Brief As more organizations rely on Cloud computing, the…