Cymulate Attack Path Discovery
Run attack simulations to discover lateral movement, remediate misconfigurations and improve threat resilience.
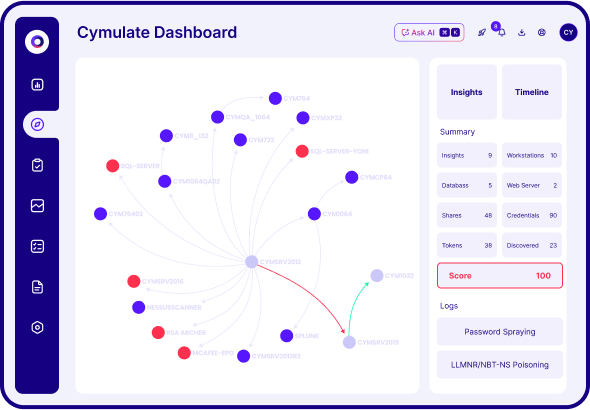
Map Attack Paths to Identify Exposure to Lateral Movement
Automate offensive testing and prove how an attacker can reach critical assets.
Map Attack Paths
Visualize all potential lateral movement attack paths.
Test Privilege Escalation
Visualize all potential lateral movement attack paths.
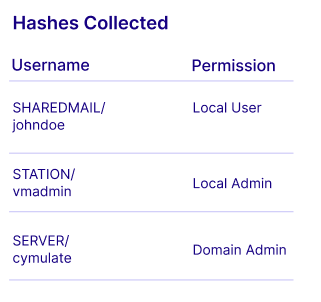
Target Crown Jewels
Assess how attackers can exploit exposures to reach critical data.
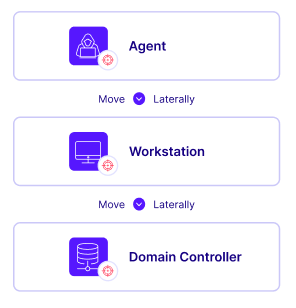
Attack Path Discovery Benefits
Cymulate Attack Path Discovery automates offensive testing to identify threat exposures related to privilege escalation and lateral movement exposures. Cymulate maps potential adversary advancement paths, validates network segmentation and access control policies and delivers actionable mitigation guidance to improve threat resilience.
Offensive testing made easy with automation
Validate segmentation
Reveal hidden exposures
Prioritize mitigations
What our customers say about us
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable before an attack occurs.
GET A PERSONALIZED DEMO
Want to make sure you are preventing lateral movement?
“Through validation, Cymulate helps us understand which vulnerabilities can be exploited in our organization. This helps us focus our limited resources so we can be proactive and remediate before a threat becomes an actual problem”.
– CISO, Law Enforcement