cymulate Exposure Validation Platform
AI-powered security validation focused on action
Optimize cyber defenses and prove the state of cyber resilience, minus friction with the power of unified validation.
Exposure validation that filters out the noise, so you can focus on the exploitable.
Validate Controls
Find and fix your gaps
Validate Threats
Know your risk
Validate Response
Battle test your SOC
The Cymulate Difference
Cymulate combines the best of automated security validation with a focus on threat exposure to continuously test and optimize your security. Integrate Cymulate into your exposure management program to focus on the exploitable.
Complete validation
Single platform to test controls, threats and attack paths.
Simple automation
Advanced testing for any blue or red teamer to run and customize.
Powerful AI assist
Shrink time to value and remove human bias in testing/scope.
Remediation
Actionable results and automated control updates.
drowning in vulnerabilities and potential threat Exposure?
Validation provides the filter of what’s exploitable.
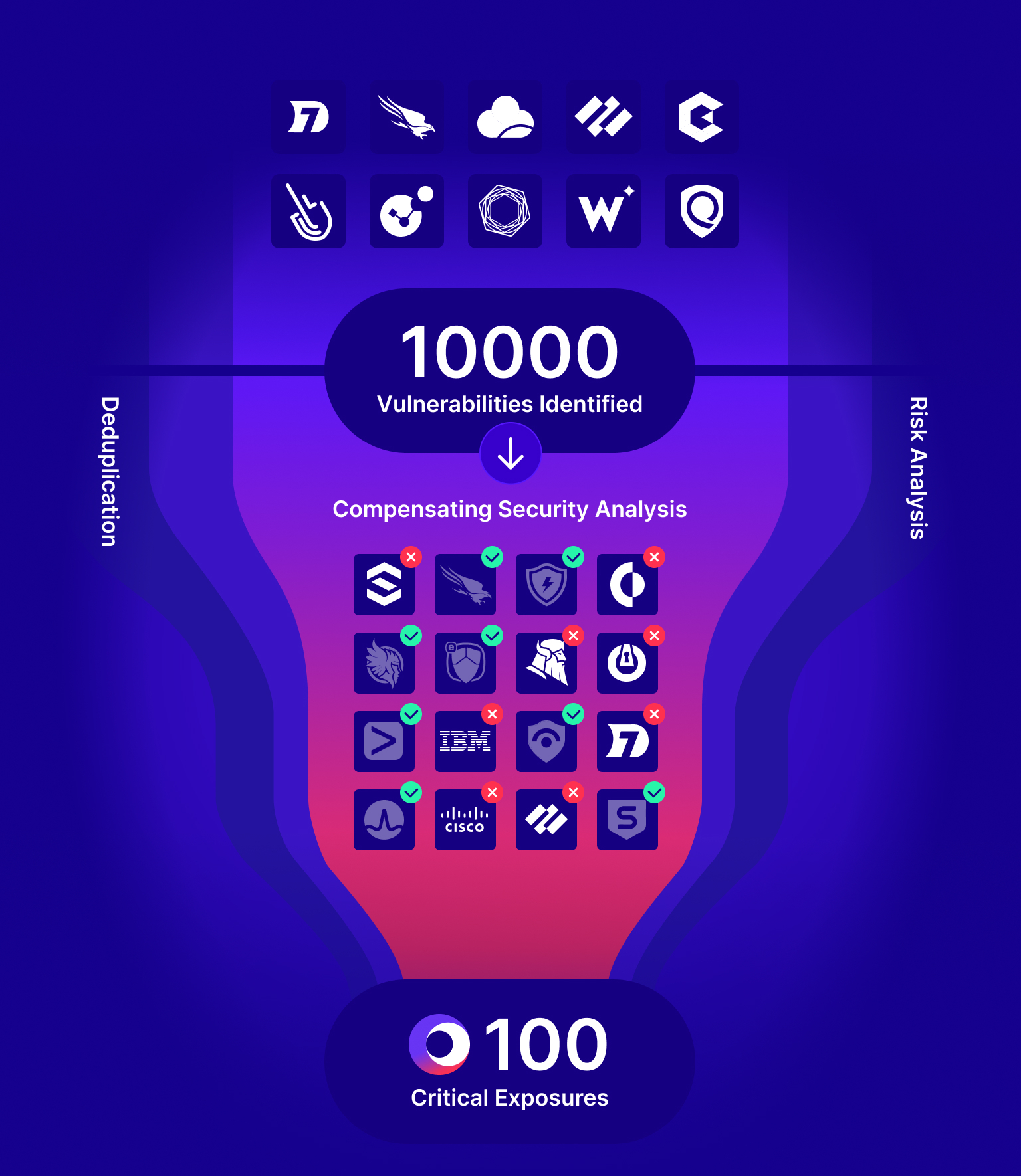
Cymulate Exposure Validation Platform
VALIDATE
Results & Outcomes
81%
Improvement in risk score in 4 months
global transportation
168
Exploits prevented from 1 policy change
healthcare company
60%
Increase in team efficiency
FINANCE COMPANY
Backed by the Industry
Frost Radar
Cymulate Named Market Leader for Automated Security Validation by Frost & Sullivan
Learn More
Customer’s Choice
2024 Gartner® Peer Insights™ Voice of the Customer for Breach and Attack Simulation
Learn More
What our customers say about us
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
Technology Integrations
GET A PERSONALIZED DEMO
Ready to see Cymulate in action?
“With Cymulate, we can present quantifiable data to the board and show a direct correlation between investments and the reduction in risk.“
– Avinash Dharmadhikari, CISO, Persistent
Featured Resources

Exposure Management
Learn about the essential technologies, workflows and metrics to drive exposure management.
2024 State of Exposure Management
This report highlights the accelerated adoption of exposure management to redefine SecOps.

LV= Takes a Data-Driven Approach
Cymulate provides LV= near real-time data to prove it is secure and validate strategic decisions.