Breach and Attack Simulation (BAS)
Test and optimize your cyber security defenses using real-world attack simulations.
Don’t speculate. Simulate.
Validate security control effectiveness and test your defenses against the latest threat activity to optimize security before an attack occurs.
Validate Controls
Find gaps and weaknesses in security controls and policies.
Validate Threats
Identify exposures to immediate threats that emerge daily.
Simulate Attacks
Simulate full kill-chain attacks from advanced threat actors.
Breach and Attack Simulation Benefits
Breach and attack simulations automate real-world attack scenarios to assess your security posture and identify weaknesses in security controls, validate defenses against active threats and run live-data exercises to test your security operations response.
TEST LIKE AN ATTACKER.
Schedule a call with one of our experts.
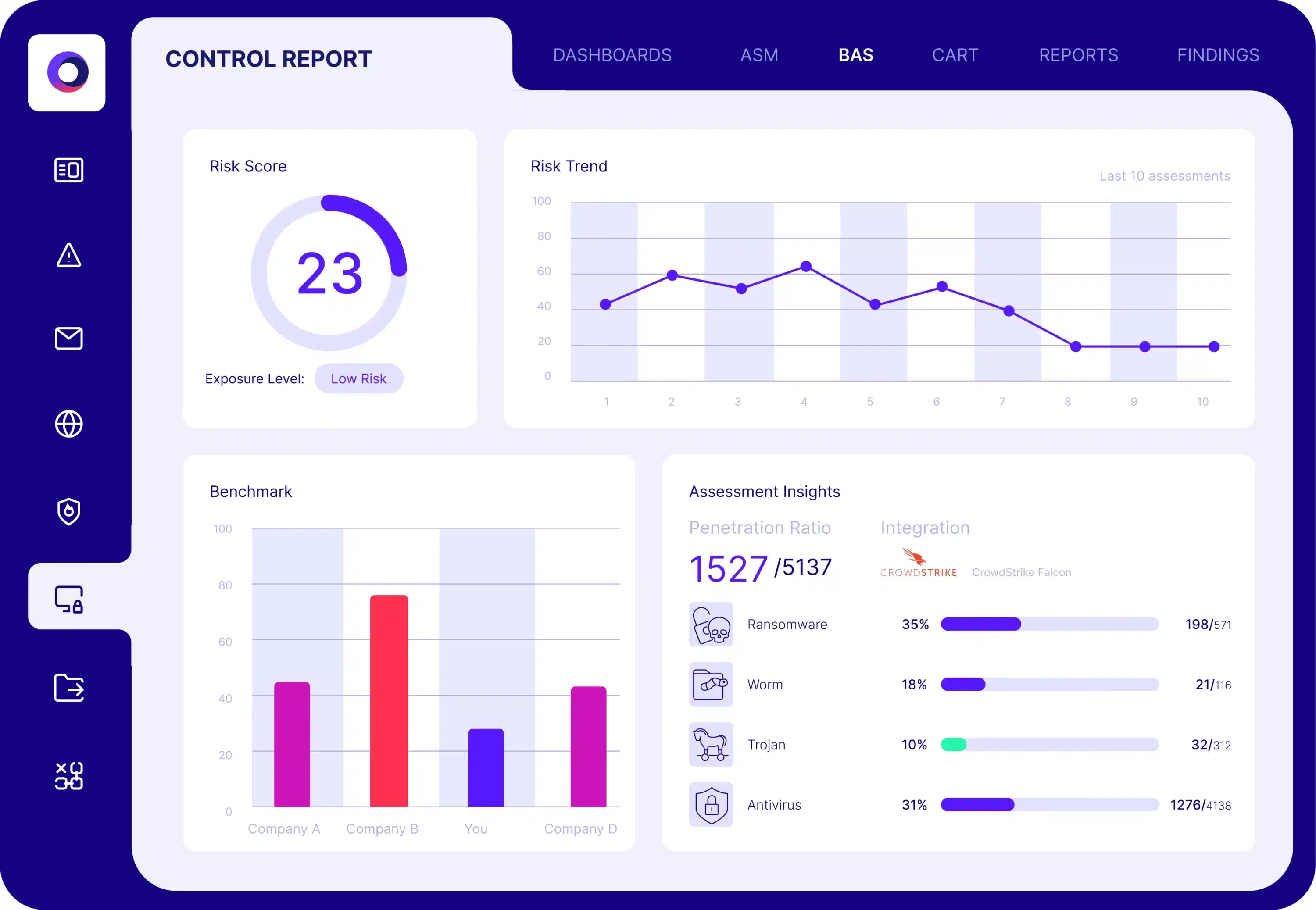
Security Control Validation
The Cymulate Exposure Validation Platform uses breach and attack simulation to validate security controls and harden defenses with real-world testing that identifies control weaknesses and includes policy tuning guidance, automated control updates and custom mitigation rules that can be directly applied to your security controls.
What our customers say about us
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
Breach and Attack Simulation FAQs
BAS is a process that allows businesses to simulate cyberattacks on their systems and networks to identify weaknesses in their security posture. BAS helps organizations proactively identify and address security issues before an attack occurs. It also ensures they are better prepared to defend against real-world threats.
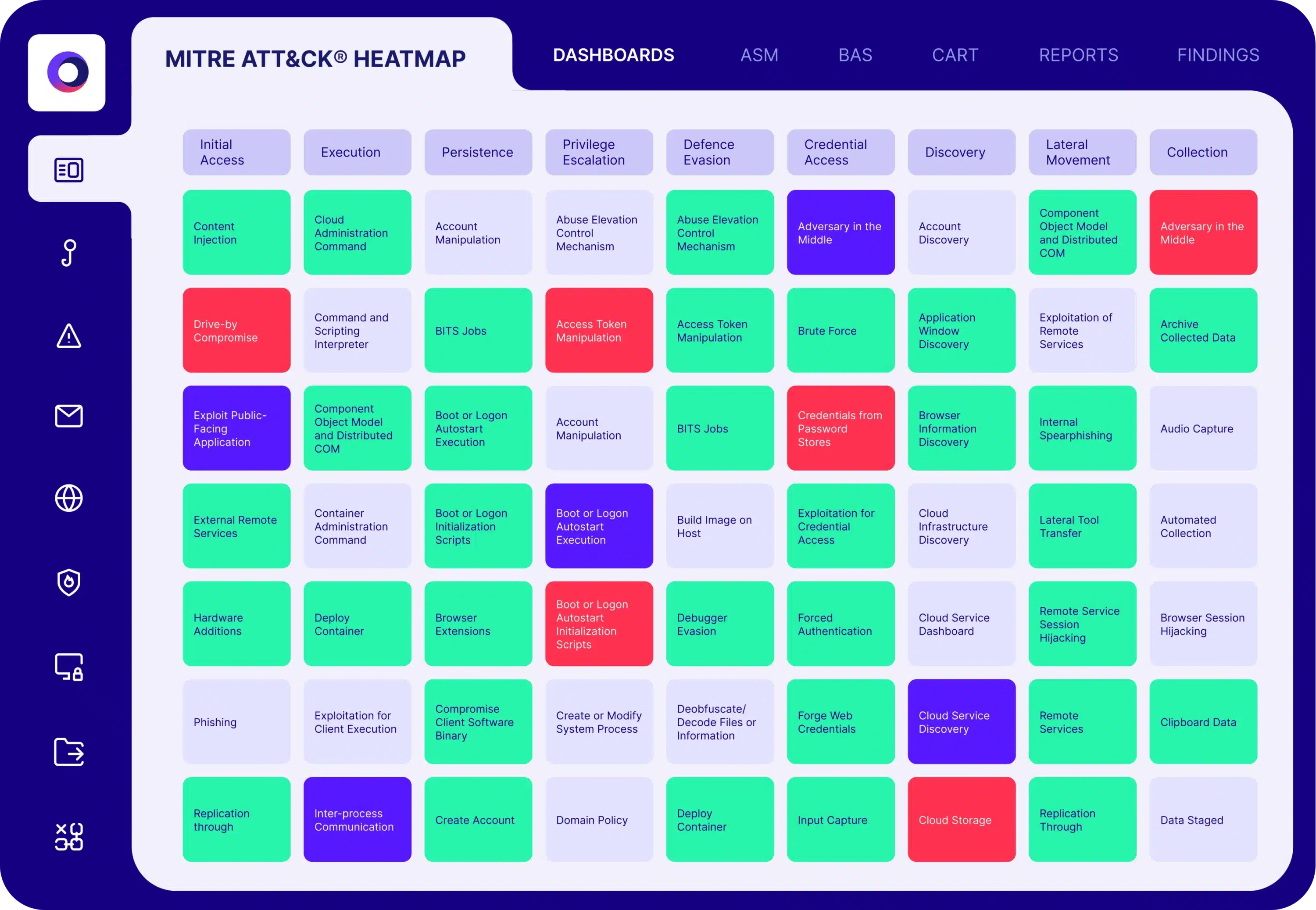
Vulnerability scans list vulnerabilities found in an organization’s environment and prioritize them based on the Common Vulnerability Scoring System (CVSS) rather than the vulnerability’s exploitability in the organization’s specific environment. Cymulate BAS continuously provides organizations the visibility on how well their security controls prevent vulnerabilities from being exploited. This allows companies to create a risk-reduction action plan based on prioritization. Cymulate’s simulated and emulated attacks complement severity with exploitability and account for the effectiveness of compensating security controls in an environment.
Cymulate BAS provides organizations with comprehensive security control validation. The modular solution addresses a wide variety of business and technical use cases. Security professionals leverage Cymulate’s insights to prioritize and reduce cyber risk, justify investments, provide proof of security resilience to management and boards, and for compliance and regulatory programs. Additionally, companies that utilize Cymulate BAS, CART (Continuous Automated Red Teaming), and ASM (Attack Surface Management) gain visibility into the full spectrum of their organizations’ exposure and breach feasibility—with one consolidated platform.
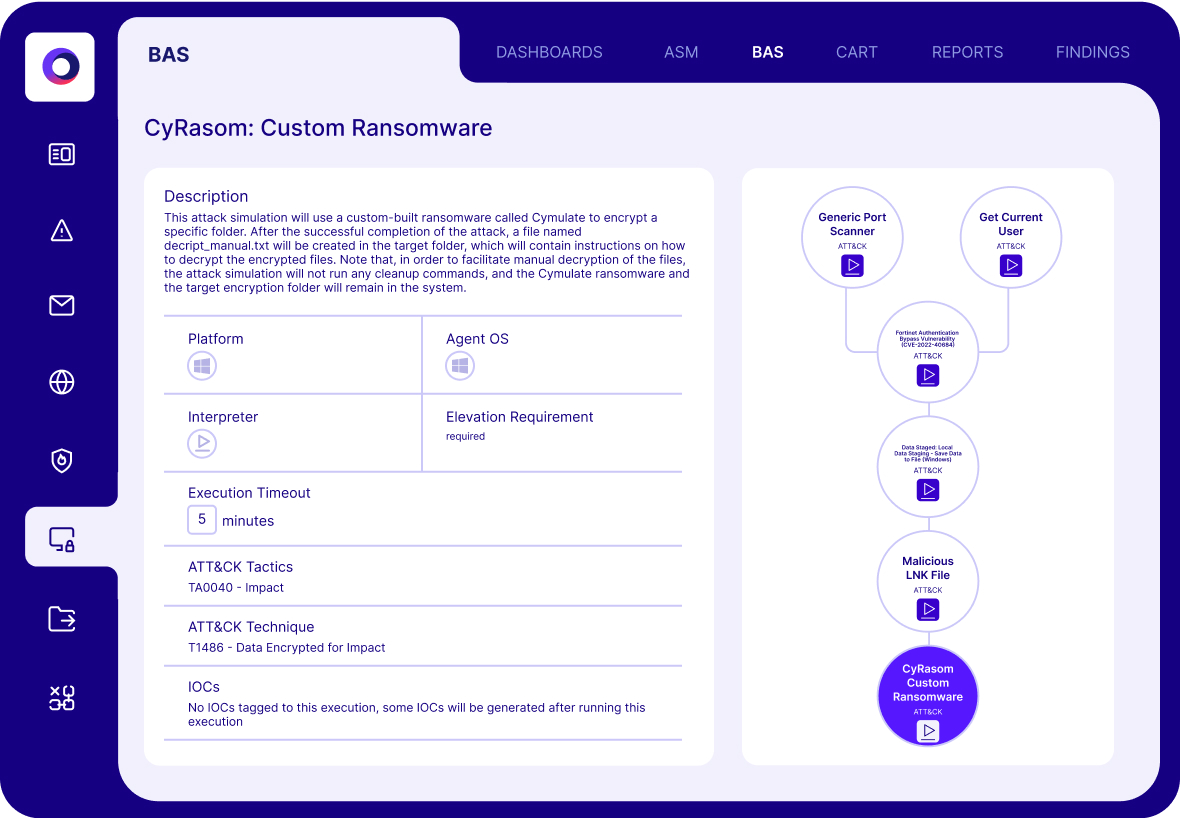
Cymulate BAS launches attack scenarios to discover security gaps and assess the layers of an organization’s security stack. It is cloud-based, providing continuous updates that enable customers to test new threats as they emerge. Deployment is quick and easy, with assessments launched directly from the cloud and some requiring a lightweight agent that serves as a proxy, minimizing installation and maintenance efforts. Cymulate BAS Scenarios includes control validation capabilities for email gateways, web gateways, web application firewalls, endpoint security, and data exfiltration. Additional capabilities feature immediate threat assessments, full kill-chain scenarios, and advanced scenarios—a customizable open-attack framework.
Every organization, regardless of size or industry, can benefit from a BAS solution. Cybersecurity threats are prevalent across all sectors and implementing a BAS solution can help companies identify and address weaknesses in security controls and exploitable vulnerabilities in their security infrastructure before they are exploited by attackers. It is recommended to find a consolidated platform that covers many use cases and can scale and adapt to an organization’s evolving security needs as it progresses in its cyber maturity.
Cloud environments use a multi-layered architecture that includes applications, containers / Kubernetes, cloud workloads and cloud infrastructure. Cymulate BAS and BAS Advanced Scenarios can be used for automated security validation of your cloud runtime environment.
- Applications: Use the WAF assessment to validate security for web apps hosted in the cloud.
Containers / - Kubernetes: Use BAS advanced scenarios to validate the detection of malicious behaviors in containers running Kubernetes on Azure, AWS and GCP.
- Cloud Workloads: Use the endpoint security assessment for cloud workloads hosting virtual machines.
- Cloud Infrastructure: Use BAS advanced scenarios to validate detections of malicious behaviors in your Azure, AWS or GCP infrastructure.
Cymulate BAS has specific automated security validation assessments for the following attack vectors:
- Secure Email Gateways (SEG)
- Secure Web Gateways (SWG)
- Web App Firewalls (WAF)
- Endpoint Security (AV / EDR)
- Data Loss Prevention (DLP)
- Cloud Security (CWPP, Cloud IDS)
- Container / Kubernetes Security (K8S)
- Network Security (IPS/IDS)
- SIEM/SOAR Detections
The Cymulate Attack Scenario Workbench provides the capability to create custom attack simulations specific to your environment.
Traditional penetration testing services typically involve a one-time assessment of an organization’s security posture. Cymulate BAS provides ongoing, continuous assessments that simulate various real-world attack scenarios on specific security controls. This allows businesses to identify and remediate vulnerabilities in real-time rather than waiting for an annual or bi-annual assessment.
GET A PERSONALIZED DEMO
Want to stay ahead of
evolving threats?
“Cymulate allows for continuous and automated testing, which helps organizations stay ahead of evolving threats without much manual intervention.”
– Information Security Administrator, Construction Industry