Solutions

Challenge
Launch web application attacks such as SQL injection, cross-site scripting (XSS) and file inclusion.

Assess
Prevention of vulnerability exploitation in web applications including OWASP application security flaws.

Optimize
WAF protections and frequent changes to the web site such as new forms, libraries and other software modules are protected.
Benefits
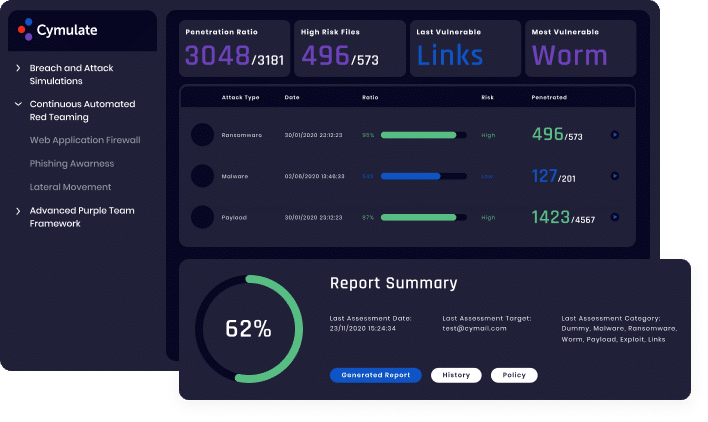
Validate the effectiveness of your Web Application Firewall
(WAF) against threat evolutions and stop attacks in the pre-exploitation stage.
- Track WAF effectiveness over time and prevent security drift
- Find, prioritize, and fix security gaps against an exhaustive and
continuously updated library of web application attacks - Benchmark your web application security performance against industry peers
- Safe to run in production
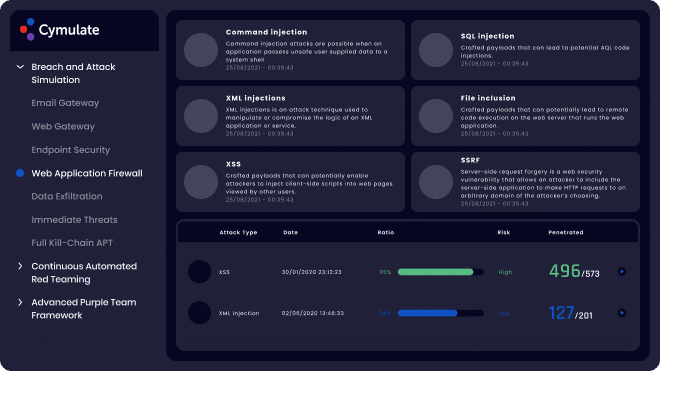
Web Application Firewall (WAF) Vector
Furthermore, the number and diversity of threats continues to increase, from advanced malware to web-specific application-layer attacks, as well as denial and distributed denial of service (DoS, DDoS) attacks and security-induced usability issues. Regarding security, organizations rely on WAF for protecting their web apps. These days, cybercriminals and novice black hats easily find all sorts of automated attack tools and exploit kits online. With such tools, all they need to do is insert a URL address as the target and launch their attack. A successful attack can bring down a website that is used to generate revenue for the organization. Every minute of down time costs the organization a lot of money, impacts its brand credibility and translates into business loss. A notorious example is the infamous Equifax breach that was caused by an application server vulnerability (Apache Struts) affecting over 140 million consumers.
The Web Application Firewall vector will validate the configuration, implementation, and efficacy, to ensure that the Web Application Firewall blocks malicious payloads before they get to your Web Application. The platform simulates an attacker who tries to bypass your organization’s WAF and reaches the web application, after which they attempt to perform malicious actions, such as mining sensitive information. The assessments use real payloads with benign outcomes that do not put the organization’s web applications at risk.
Technical reports provide analysis of the attacks and actionable mitigation guidance that help security teams to shore up their defenses against web application attacks. Standards-based risk scoring enable IT and security teams to identify security gaps, prioritize mitigations and take corrective measures to increase WAF efficacy. Executive reports include trend analysis to identify security drift and industry-peer benchmarking to gain comparative insights.
Learn More
More Attack Vectors and Modules

Immediate threats
Validate your defenses against the latest cyber-attacks found in the wild, updated daily.

Full Kill Chain APT
Validate your defenses against APT attack scenarios e.g., Fin8, APT38, Lazarus and custom scenarios.

Lateral Movement
From an initial foothold, propagates within the network to find critical assets.

Data Exfiltration
Validate that sensitive and critical data cannot be exfiltrated from the organization.
Endpoint Security
Validate detection and prevention of endpoint ATT&CK TTPs including ransomware, worms, and more.

Web Gateway
Validate your defenses against malicious inbound and outbound web browsing and command and control.

Email Gateway
Validate your defenses against thousands of malicious email constructs, attachments, and links.