The Challenge: Managing the Growing Number of Emerging Vulnerabilities
Regardless of the amount of effort and resources invested, organizations are unable to manage the growing amount of vulnerabilities in their environment. Companies have taken to prioritizing vulnerability patching based solely on the Common Vulnerability Scoring System (CVSS) score, but just because a vulnerability is discovered does not mean it can be exploited. For example, a security team might decide to patch a vulnerability with a CVSS score of 10 when it unknowingly has compensating controls already in place that prevent its exploitation.
The Solution
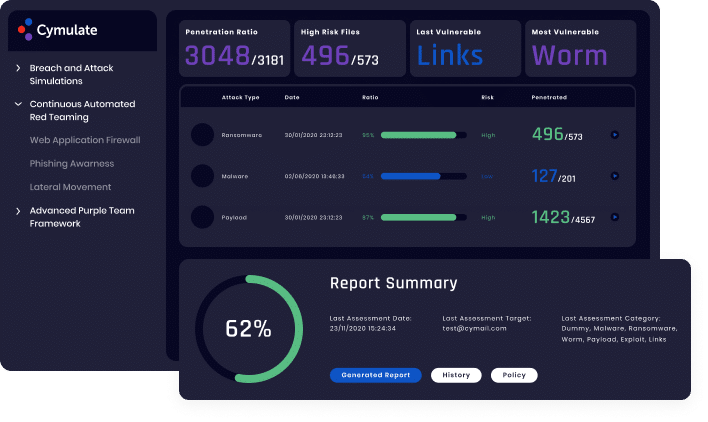
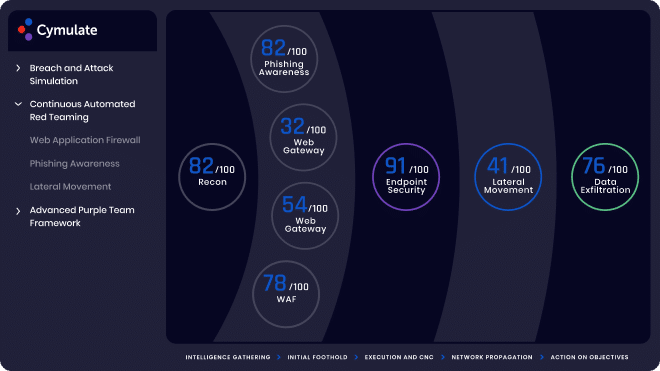
By adding the Attack–Based Vulnerability Management (ABVM) dashboard to Cymulate’s security control validation process, organizations are instantly provided with additional context about their vulnerabilities. ABVM integrates with common vulnerability scanners to inform security teams about the effectiveness of compensating controls protecting vulnerable machines and assets. ABVM combines the results of Cymulate’s simulated attacks with data from the organization’s vulnerability scanner to enable teams to accurately prioritize vulnerability remediation, patching, or reconfiguration of compensating security controls. Additionally, with these findings, Cymulate correlates the criticality of vulnerabilities with the value of assets, allowing security teams to optimize patching prioritization and reduce the patching workload.
Benefits

Improved Staff Workload Management

Reduced Vulnerability Exposure Time

Minimized Costs
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Cymulate Exposure Management
and Security Validation.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation