The Challenge: Managing an Expanded Digital Footprint
Business-driven digital transformation has expanded the digital footprint of a business environment, making it increasingly complex to manage. As a result, the external attack surface has grown exponentially, and adversaries are finding windows of opportunities to exploit their targets.
The Solution
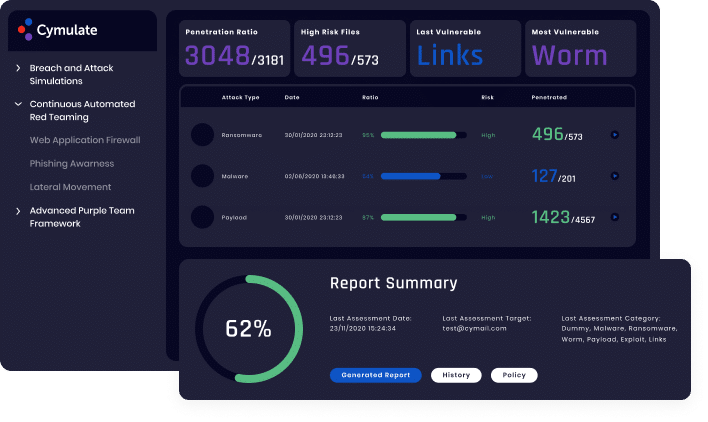
Cymulate automates the discovery, analysis, and testing of an organization’s digital footprint and applies a risk-based approach to attack surface management.
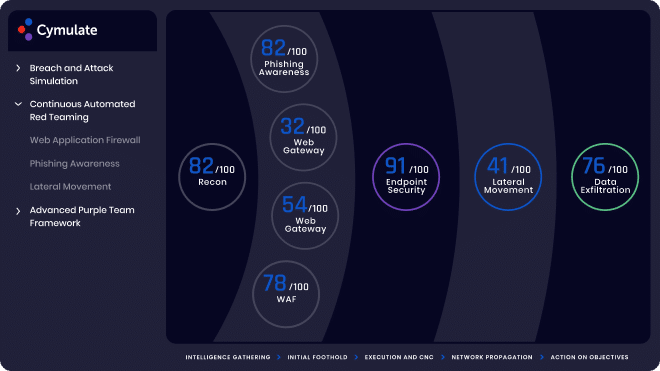
The platform performs reconnaissance to discover vulnerabilities and potential doorways into the organization, such as open ports and exposed cloud storage. Once a vulnerability or potential doorway is discovered, automated red teaming attempts to breach the organization’s defenses to assess each exposure’s risk.
Benefits

Visibility of Exposed External Assets

Identify High-Risk Exploitable Vulnerabilities
Attack Surface Resiliency Scoring
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation