Drive Exposure Management with Automated Security Validation & Full Context of Attack Surface
When applying exposure management into practice, cyber programs face the challenge of integrating programs like vulnerability management and threat detection and response—all while struggling to answer the question “How exposed is the organization?”
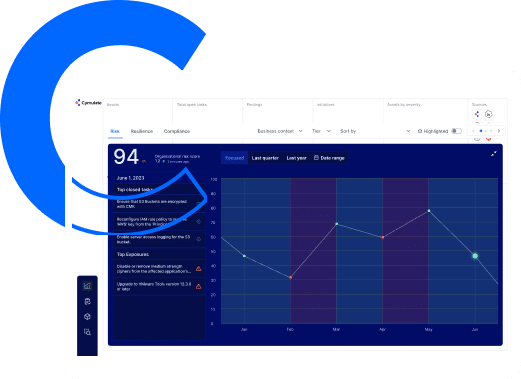
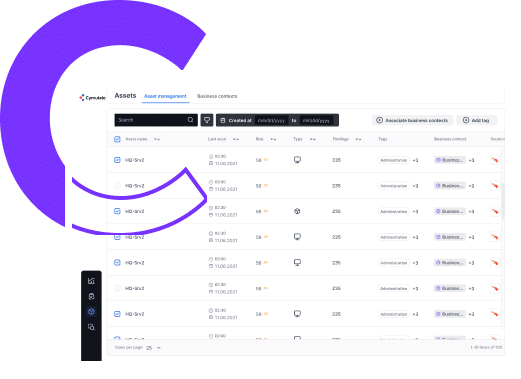
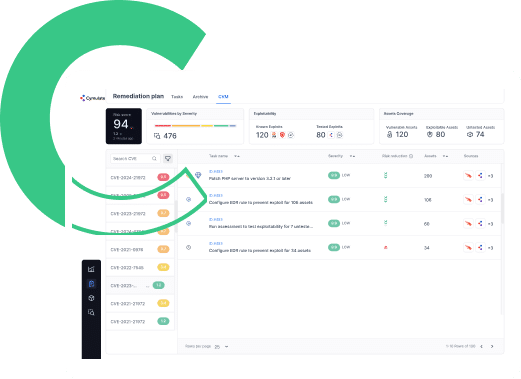
Security teams rely on Cymulate as the single source of truth for threat exposure risk and the actions required to minimize that risk. The Cymulate Exposure Management and Security Validation Platform provides the essential technologies, workflows, and metrics to drive exposure management programs. Cymulate combines full visibility of the attack surface with business context and the most advanced security validation to focus remediation and prove cyber resilience.
Benefits of Cymulate Exposure Management
Maximize Existing Resources
“Cymulate provides us with the insights to close gaps and optimize the controls we already have in our security stack—we don’t need to waste time or money looking for new tools to improve our security.”
Liad Pichon, Director of Cybersecurity, BlueSnap
Benchmark Security Resilience
“Cymulate improved our risk management process and decision-making.”
Yoav Gefen, CISO, Maman Group
Optimize SecOps & Incident Response
“Cymulate enables us to test Nemours’ defenses against the latest cyber threats as they emerge, prioritize remediation efforts, and improve our security team’s incident response skills.“
Jim Loveless, CISO, Nemours
Rationalize Investments
“With Cymulate, we can present quantifiable data to the board and show a direct correlation between investments and the reduction in risk.“
Avinash Dharmadhikari, CISO, Persistent Systems
“Cymulate has been helping me to evaluate my security posture against behavior based as well zero day threats.”
– IT Security & Risk Management Associate
“Technical capabilities provided are outstanding, customer service is highly responsive and product mgmt. is flexible in supporting us with our requests.”
– Security Operations Analyst
“The Cymulate BAS is delivering excellent outcomes, contributing significantly to enhancing my security effectiveness.”
– IT Security & Risk Management Associate
“My experience with the platform was exceptional. It delivers on its promises with easy navigation, effective mitigation steps, and top-notch after sales support.”
– Chief Risk Manager
“Always willing to help offering training sessions and encourage use of the product’s additional available features.”
– Senior Software Engineer
“I believe that Cymulate brings a vision of risks, vulnerabilities and actions that we are unable to pay attention to in our work day.”
– Security Operations Specialist
“The range and breadth of attack scenarios, potential targets and how well each tool integrates is really excellent.”
– Penetration Tester
“We had an excellent experience with Cymulate, from product deployment to while using the platform.”
– Senior Cybersecurity Engineer
“Awesome customer Support and techniques used by Cymulate to identify security gaps.”
– IT Security & Risk Management