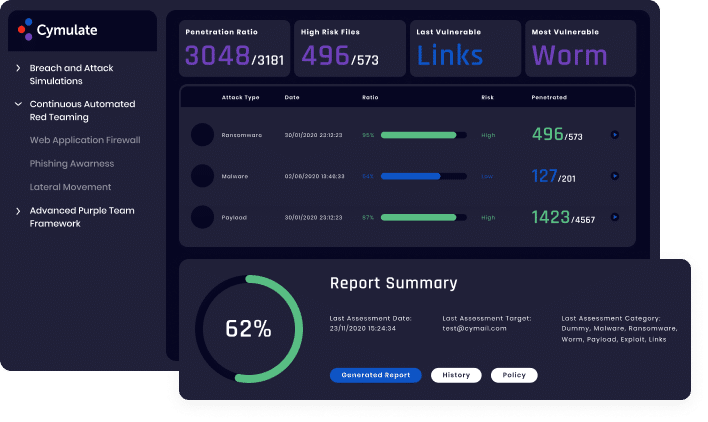
The Problem: Unclear Reporting
Security leaders and executives want to quantify risk and the impact of various security programs. They need metrics to know how a new project, or a vendor consolidation initiative has affected the organizations security posture.
The Solution
Cymulate Exposure Management and Security Validation allows you to quantify risk using standards based scoring methodologies. This enables you to baseline your security performance and measure the impact of security programs, making it easier to convey results to business executives and the board.

The Problem: Insufficient Resources
Your cybersecurity team will always suffer from a backlog of projects and activities, so you need to be sure that they are working effectively and efficiently.
The Solution
Cymulate Exposure Management and Security Validation increases the efficiency of your team by automating activities such as threat intelligence testing, red teaming, and security drift prevention, it prioritizes security gaps so that they are not wasting time on secondary issues.

The Problem: Budgeting Ineffectively
Prioritizing security spend based on the business criticality of different environments is a best practice. You may tolerate more risk in your branch network than you do in your finance systems. But are you achieving the desired outcomes?
The Solution
Cymulate Exposure Management and Security Validation enables you to measure the security effectiveness of different business environments in production and allocate spend to achieve the desired outcomes.
Why We Are Better
Multi-Environment
Consistent Scoring Across the Full Kill-Chain
Fast Results
SaaS Based
Benefits

Increase Productivity

Be More Effective

Maximize Returns
Learn More