Cloud Security Validation
Validate your cloud defenses against today’s cloud-focused threat actors and optimize your cloud security.
Threat actors target dynamic cloud environments to exploit security weaknesses.
Increase in cloud intrusions in the previous year
Source: Crowdstrike
Container workloads lack proper protection
Source: Crowdstrike
Cyber breaches involve cloud-stored data
Source: IBM
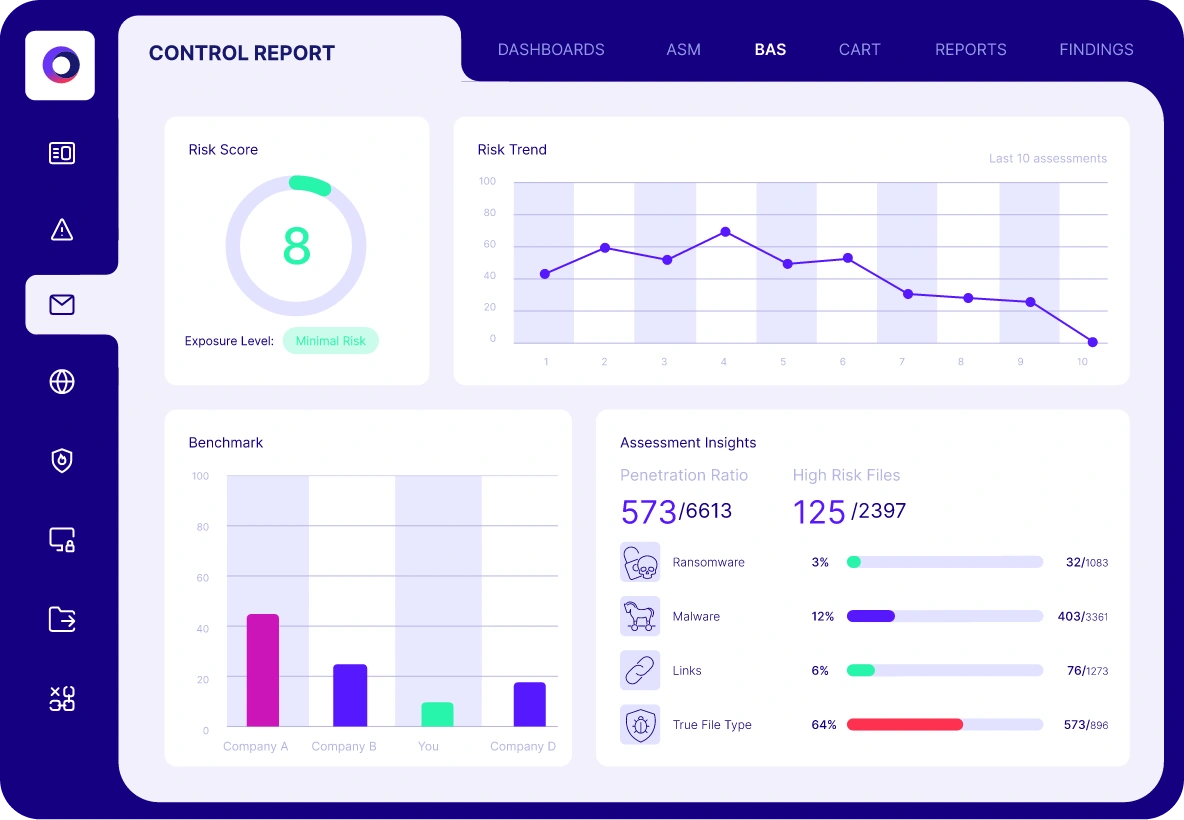
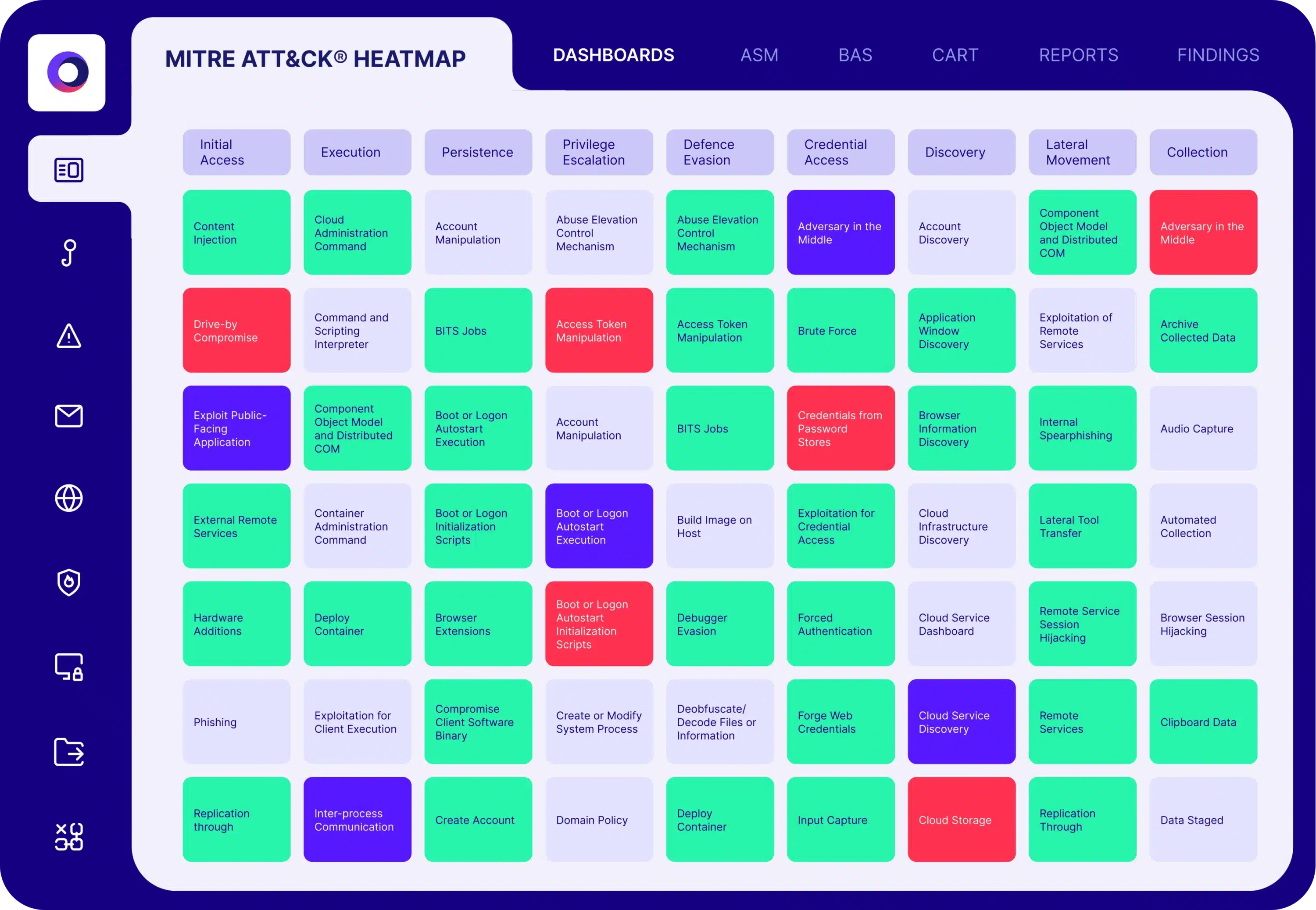
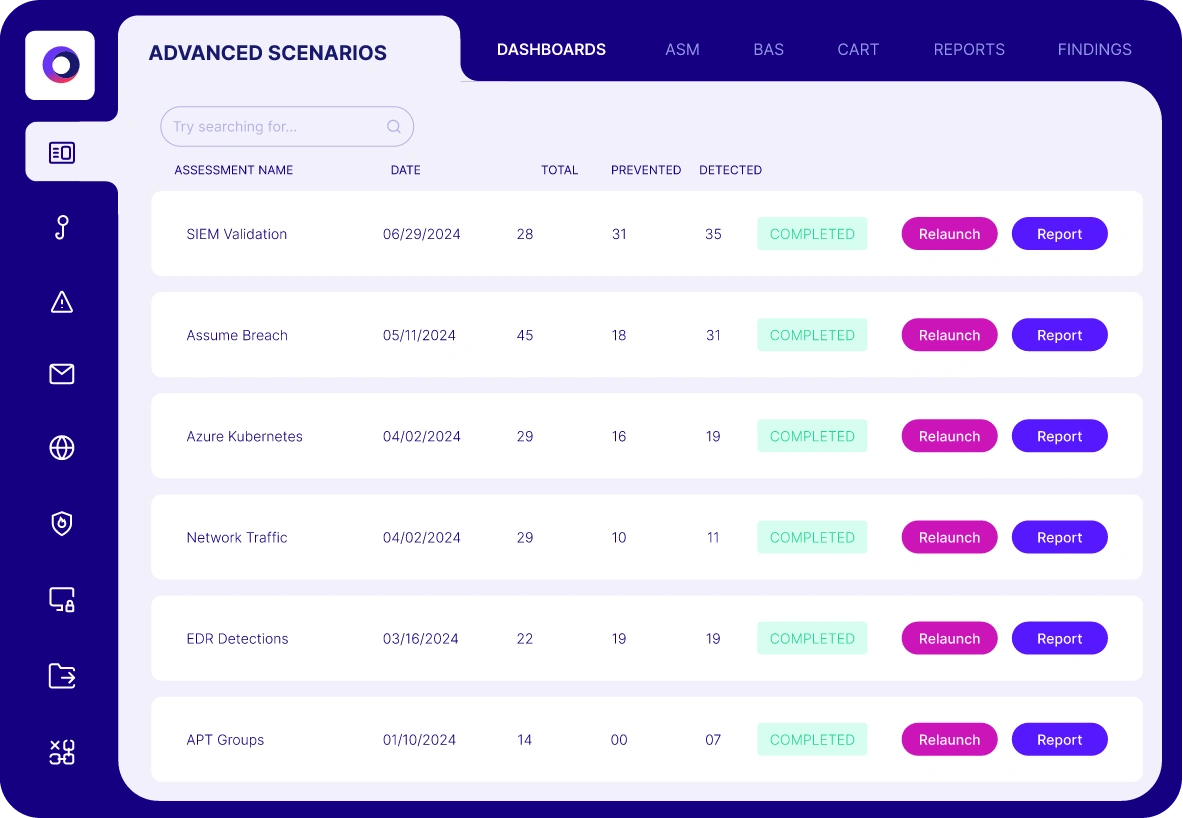
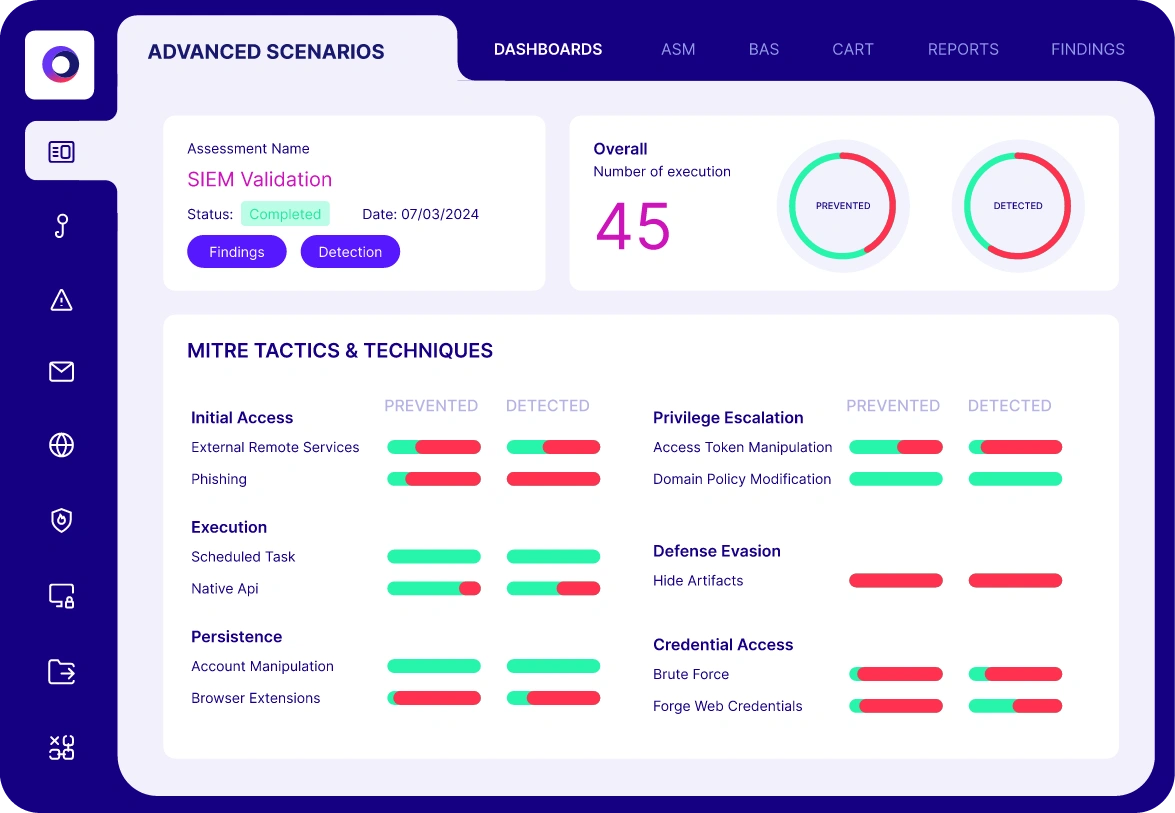
Automated Security Validation for Cloud Security
Cymulate provides both pre- and post-exploitation simulations to test and validate the threat detection and runtime security controls for different layers of your cloud architecture.
Solution Results
60%
Increase in SecOps
team efficiency
finance company
81%
Reduction in cyber
risk in four months
Global Transportation
168
Exploits prevented
from one policy change
healthcare organization
Solution Benefits
What our customers say about us
Organizations across all industries choose Cymulate for automated cybersecurity validation of their security controls across the different layers of their cloud architecture.