Problem
Endless tasks compounded by lack of prioritization results in wasted time on issues that contribute nothing to an organizations security posture.
Solution
Cymulate Exposure Management and Security Validation discovers and prioritizes critical issues so that your team can address high impact exposures first.

Problem
With the persistent cyber-skills shortage, security operations continuously face a lack of qualified personnel and are required to do more with less, leaving little time for projects, exercises and training.
Solution
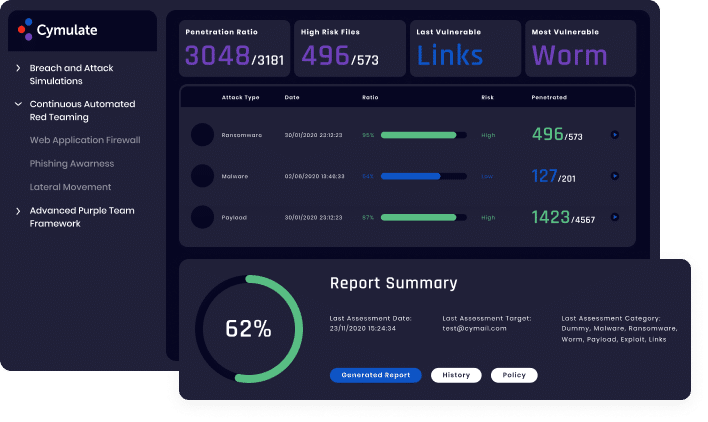
Continuous Security Validation enables the SOC team to automate and perform more security testing and health checks, run more incident response exercises and improve their adversarial skills on the job, making them better defenders.

Problem
SOC teams are inundated with information overload and slow, manual fine tuning of SIEM rules create a long window of exposure to threats.
Solution
Continuous Security Validation enables the SOC team to fine tune SIEM and AI-based detections of real adversarial behaviors. Cymulate Sigma rules, automated custom SIEM queries, and integrations with SIEM and SOAR systems accelerate the process of continuous improvement.
End-to-End Enterprise Cyber-Risk Management
purple teaming a daily practice by putting the adversary in the hands of the SOC for continuous improvement.
Security Operations
Prioritize Patching
Identify attackable vulnerabilities to prioritize patching
Health Checks
Automate health checks and security assurances
QA Policy, Configuration, and Software Updates
Validate security operational effectiveness after changes to the security infrastructure
Attack Surface Management
Know what an adversary can discover and e aware of changes to assets, vulnerabilities and risk
Alert Investigation and Escalation
Validate and optimize EDR detections and SIEM alerts based on attacks
Proactive Threat Hunting
Launch APT simulations to exercise pro-active threat hunting
Incident Response
Simulate incidents to practice incident response playbooks
Asses Threat Intelligence
Launch threat intelligence led assessments updated daily to the platform
Benefits

Increase Efficiencies

Optimize Detections

Upskill the Team
Operationalize Threat Intelligence
and the MITRE ATT&CK Framework

MITRE ATT&CK
Implementation

Threat Intelligence
Assessments

Custom
Scenarios
SOAR
Findings
via API

Portal
Queries
IoCs and IoBs
Mitigations Guidance
Queries
IoCs and IoBs
Mitigations Guidance
SOAR
Findings
via API

Portal
Learn More