Frequently Asked Questions
Product Information & CART Overview
What is Continuous Automated Red Teaming (CART)?
Continuous Automated Red Teaming (CART) is a proactive security approach that adds automation and continuous testing to traditional red team exercises. CART regularly simulates real-world attacks on an organization’s systems and applications, validating entire attack paths from infiltration to actions on objectives. These simulations autonomously deploy attack techniques to advance within the network, helping organizations identify and remediate exposures before adversaries can exploit them. Learn more.
How does Cymulate's CART solution work?
Cymulate delivers CART through its cloud-based Exposure Validation platform, accessible via web browser. Only one agent per environment is needed, eliminating the need for on-premise installation. The platform automates network penetration testing and uses Attack Path Discovery to simulate attacks that propagate within the network, searching for critical assets. Users can test any technique at any stage of the kill chain, execute multi-staged chained attacks, and leverage over 100,000 attack scenarios for comprehensive coverage. Read more.
How does CART differ from Breach and Attack Simulation (BAS)?
While BAS focuses on specific attack techniques (e.g., phishing, malware delivery) to validate security controls, CART is broader and tests the entire kill chain in a single assessment. CART simulates how attackers advance through the network from initial compromise to privilege escalation and lateral movement, identifying chokepoints and exposures. Cymulate combines both BAS and CART to continuously and automatically run realistic attacks, ensuring organizations have effective prevention and detection controls. Learn more.
What capabilities does Cymulate provide to enable CART?
Cymulate Exposure Validation offers reusable templates and over 100,000 attack scenarios for ongoing testing. Key capabilities include lateral movement assessments, custom attack creation via a user-friendly workbench, automated Attack Path Discovery, and phishing assessment modules. These features allow organizations to test more environments more frequently without increasing staff, providing enhanced visibility into security gaps and employee resilience. Read more.
How does Cymulate's platform differ from traditional penetration testing services?
Traditional penetration testing provides a one-time, point-in-time assessment that can quickly become outdated and often lacks integration with existing security technologies. Cymulate continuously and automatically validates the entire attack chain, integrating with an organization’s security stack to measure exposures and the effectiveness of controls in real time. This enables businesses to identify and remediate exposures proactively, rather than waiting for annual or bi-annual assessments.
Features & Capabilities
What are the key features of Cymulate's CART solution?
Key features include:
- Continuous, automated offensive testing and exposure validation
- Custom attack chain creation and simulation of advanced threats
- Attack Path Discovery to map lateral movement and privilege escalation
- Blast radius and impact analysis for critical asset protection
- Phishing resilience assessments as part of red team campaigns
- MITRE ATT&CK heatmap visualization for detection coverage
- Over 100,000 attack scenarios and a user-friendly attack workbench
- Automated remediation and integration with SIEM, EDR, and XDR platforms
See full platform details.
What integrations does Cymulate support?
Cymulate integrates with a wide range of security tools, including SIEM (e.g., Microsoft Sentinel, Splunk, IBM QRadar), SOAR (e.g., Palo Alto Cortex XSOAR), EDR (e.g., CrowdStrike Falcon, SentinelOne), vulnerability management (e.g., Tenable, Qualys), cloud security (e.g., Wiz, Check Point CloudGuard), IAM (e.g., Microsoft Active Directory), and ticketing systems (e.g., Jira, ServiceNow). For a full list, visit Cymulate's Partnerships and Integrations page.
Does Cymulate offer an API?
Yes, Cymulate provides an API with a rate limit of 10 requests per second per IP address. Documentation is available at Cymulate API Documentation.
What technical documentation and resources are available?
Cymulate offers solution briefs, data sheets, e-books, and guides covering detection engineering, threat resilience, exposure management, and more. Resources include:
See the full library at Cymulate's Resources Page.
Use Cases & Benefits
Who can benefit from Cymulate's CART solution?
Cymulate is designed for blue teams (SOC analysts/managers), red teams (offensive security professionals), CISOs/CIOs, executives, and stakeholders across industries such as finance, healthcare, retail, technology, manufacturing, utilities, and more. It is suitable for organizations seeking to improve cybersecurity posture, validate threats, and optimize resilience, including those with cloud environments. Learn more about roles.
What business impact can customers expect from using Cymulate?
Customers typically experience:
- 30% improvement in threat prevention capabilities
- 52% reduction in critical exposures
- 60% increase in operational efficiency for security teams
- Quantifiable risk reduction and resilience metrics for executive reporting
- Faster recovery post-attack, addressing the average 6+ days required to restore operations
These metrics help organizations align security with business goals and reduce breach-related costs. See demo.
What problems does Cymulate help solve?
Cymulate addresses challenges such as:
- Difficulty quantifying cybersecurity efforts and risk reduction
- Prioritizing remediation based on real risk
- Manual, time-consuming security operations
- Limited visibility into security posture and exploitable misconfigurations
- Validating cloud security and real-time threat simulation
- Operational inefficiencies in vulnerability management
- Post-breach recovery challenges
The platform provides resilience metrics, automation, and actionable insights to address these pain points.
Can you share specific case studies or customer success stories?
Yes. Notable examples include:
See more at Cymulate's customer stories page.
Which industries are represented in Cymulate's case studies?
Cymulate's case studies span critical infrastructure, education, engineering, finance, healthcare, insurance, IT services, law enforcement, manufacturing, non-profit, retail, technology, transportation, and utilities. See all industries.
Product Performance & Recognition
What performance improvements have customers seen with Cymulate?
Customers report a 30% improvement in threat prevention, 52% reduction in critical exposures, and a 60% increase in operational efficiency. These metrics are based on customer-reported outcomes and help organizations reduce breach costs and improve resilience. See more.
What industry recognition has Cymulate received?
Cymulate has been named Market Leader for Automated Security Validation by Frost & Sullivan (see announcement) and recognized as a Customers' Choice by Gartner Peer Insights (see blog).
What feedback have customers given about Cymulate's ease of use?
Customers consistently praise Cymulate for its intuitive design and ease of use. For example:
- "It’s easy to use, intuitive, and the customer support is unparalleled." – Ariel Kashir, CISO
- "Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture." – Raphael Ferreira, Cybersecurity Manager
See more testimonials.
Competition & Comparison
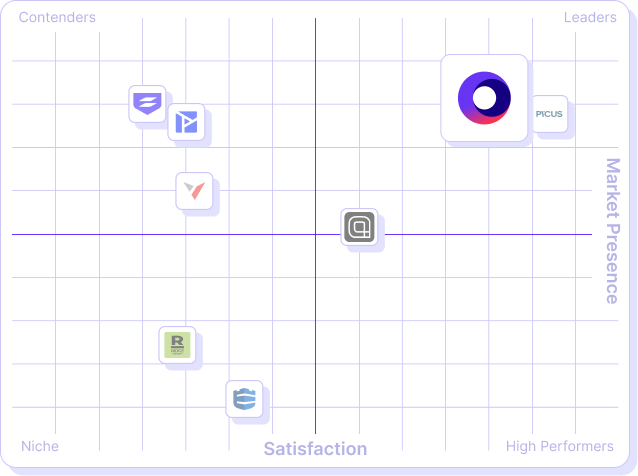
How does Cymulate compare to other CART and BAS solutions?
Cymulate differentiates itself by offering a unified Exposure Management Platform with continuous threat validation, automated remediation, and quantifiable risk metrics. Compared to competitors:
- Pentera: Focuses on penetration testing; Cymulate provides continuous validation and actionable remediation.
- Picus Security: Focuses on security control validation; Cymulate offers real-time simulations and unified management.
- Scythe: Specializes in automated red teaming; Cymulate combines full-kill-chain validation with remediation.
- AttackIQ: Finds security gaps; Cymulate also provides solutions to fix them and quantifiable metrics.
- NetSPI: Offers penetration testing; Cymulate focuses on continuous validation and prioritization.
For more, see Cymulate vs Competitors.
Why should a customer choose Cymulate over alternatives?
Cymulate offers comprehensive coverage, continuous threat validation, tailored solutions for blue/red teams and executives, automation that reduces manual operations by 25%, and measurable impact (30% improved threat prevention, 52% fewer critical exposures, 60% greater efficiency). It is recognized by Frost & Sullivan and Gartner Peer Insights. See comparison.
Security, Compliance & Technical Requirements
What security and compliance certifications does Cymulate hold?
Cymulate is certified for SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1. These cover security, availability, confidentiality, privacy, and cloud security controls. Cymulate also complies with GDPR and implements advanced security features such as role-based access controls, two-factor authentication, and robust encryption. See details.
What are the technical requirements for implementing Cymulate?
Cymulate is designed for easy implementation, requiring only basic infrastructure and a single agent per environment. No on-premise installation is needed. Customers need to meet Cymulate's pre-requisites and technical guidelines, and may require third-party software/licenses depending on integrations. Learn more.
Support, Training & Implementation
How long does it take to implement Cymulate and how easy is it to start?
Cymulate is designed for rapid, easy implementation. Most customers can get started quickly, with minimal configuration. The platform is intuitive and user-friendly, allowing users to receive actionable insights with just a few clicks. Customer testimonials highlight the ease of use and fast onboarding. See more.
What training and technical support is available?
Cymulate provides first-class customer support via email ([email protected]) and live chat (chat support). Educational resources include webinars, solution briefs, and e-books. Customers consistently praise the support team for being exceptional and helpful. Learn more.
How does Cymulate handle maintenance, upgrades, and troubleshooting?
Cymulate ensures continuous accessibility and functionality, except during scheduled maintenance as outlined in the Service Level Agreement. The support team assists with troubleshooting, upgrades, and maintenance, and customers can access educational resources for ongoing learning.
Customer Proof & Success
Who are some of Cymulate's customers?
Cymulate serves over 1,000 customers in 50 countries, including Hertz Israel, Saffron Building Society, a major bank, a sustainable energy company, a retail organization, and a gaming innovator. See detailed case studies at Cymulate's customer stories page.
What feedback have customers given about Cymulate's support?
Customers describe Cymulate's support as unparalleled and consistently helpful. For example, Ariel Kashir (CISO) states, "It’s easy to use, intuitive, and the customer support is unparalleled." See more testimonials.