Cymulate vs.
the Alternative
of exposures & threats

“I have never worked with a better
customer success team.”
– Liad Pichon, Director of Cybersecurity, BlueSnap
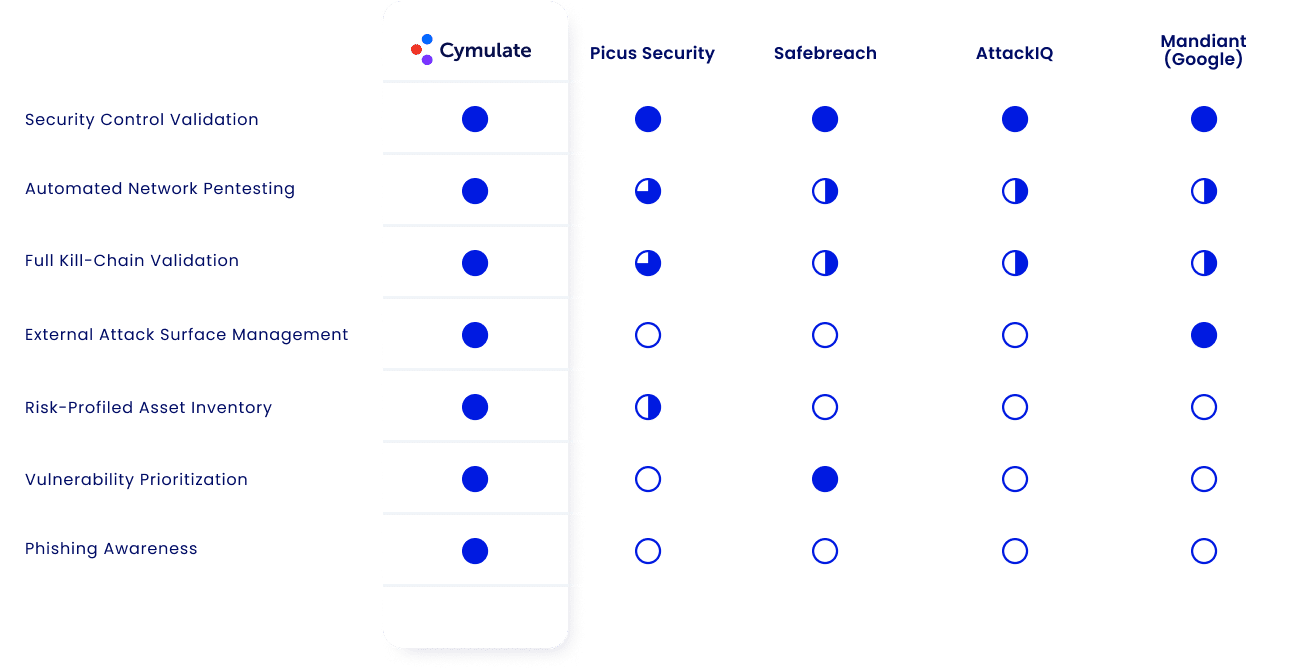
Want details on how Cymulate compares to other solutions?
See how Cymulate stacks up to the competition
Top Reasons to Switch to Cymulate

Most Comprehensive
Automate offensive testing with both breach & attack simulation and automated pentesting

360 Analysis
Provides full context with insights about your attack surface, critical assets, and exposures

Every Environment
Production-safe platform that deploys on-prem, in the cloud, or in hybrid environments

Scalable
Dynamic dashboards to enhance organizations’ interactions with their multiple security environments

Easy to Use
Less than an hour to implement
with out-of-the-box templates and automation

Customer Obsessed
Security experts provide hands-on assistance to support your security & exposure validation program
We chose Cymulate because we saw right away that it would require much less effort and time on our part to get immediate and effective insight into security program, and the solution could easily be leveraged globally.”
– IT Security & Risk Management Associate

Cymulate is super easy to use and answers the tough boardroom questions. It is a force-multiplier for my small team. I can use it to easily test efficacy in a fire-and-forget automated manner.”
– Eric Bowerman, CISO, Elara Caring

Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture.”
– Raphael Ferreira, Cybersecurity Manager, Banco PAN

Cymulate provides us with the visibility and standardization we were missing. The platform’s analytics and reporting make providing a holistic view of our cyber security posture to management and the board easier.”
– Renaldo Jack, Group Cybersecurity Head, Globeleq

As a repeat buyer, I am confident in recommending Cymulate for the visibility it provides to manage our security resources effectively and the efficiencies we gain with continuous security optimization that is simple to use.”
– Craig Bradley, Senior VP of IT, YMCA

Basic vulnerability scans tell you where you’re vulnerable, but Cymulate tells you if you will be compromised. Vulnerability scanning just gives a report; Cymulate gives us intelligence.”
– Shaun Curtis, Head of Cybersecurity, GUD Holdings

Trusted by leading brands worldwide