The Problem: Scaling Capacity
Scaling a red team’s capacity while retaining the creativity and expertise of the seasoned experts on the team.
The Solution
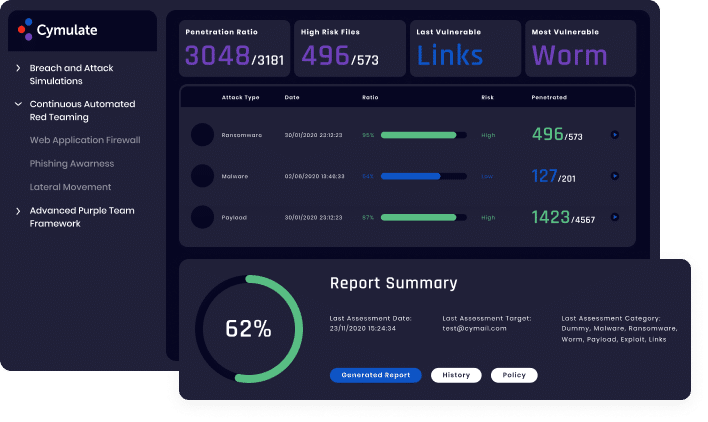
Cymulate is an open attack framework that enables experts to create assessment and scenario templates s that can be shared and reused by everyone in the team, in the addition to the rich library of resources available out of the box.

The Problem: Lack of Productivity
Increasing the operational efficiency of your pen testers and red teamers.
The Solution
Cymulate Exposure Management and Secutrity Validation enables you to automate and offload bespoke but repetitive attack campaigns and scenarios, integration with security controls provide a purple teaming experience for immediate results, reports are generated immediately including detection and mitigation guidance and Sigma rules for SIEM optimization.

The Problem: Outdated Methods
Monolithic auto pen testing tools don’t leverage the skills of your red team.
The Solution
Your Red Team is looking for the same level of openness and flexibility that threat actors have. With Cymulate, you can have both automated red teaming and an open framework to use your preferred tools and techniques, enabling you to leverage automation without compromise.
Why We Are Better
Rich Repository
Central Reporting
Purple Teaming
Custom Queries
Benefits

Increase Efficiencies

Share Expertise

Scale Red Team Resources
Learn More