Go from guessing to knowing—and acting.
You don’t need another list. You need clarity.
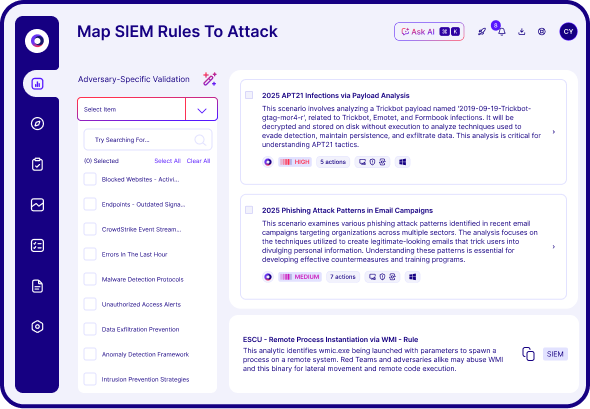
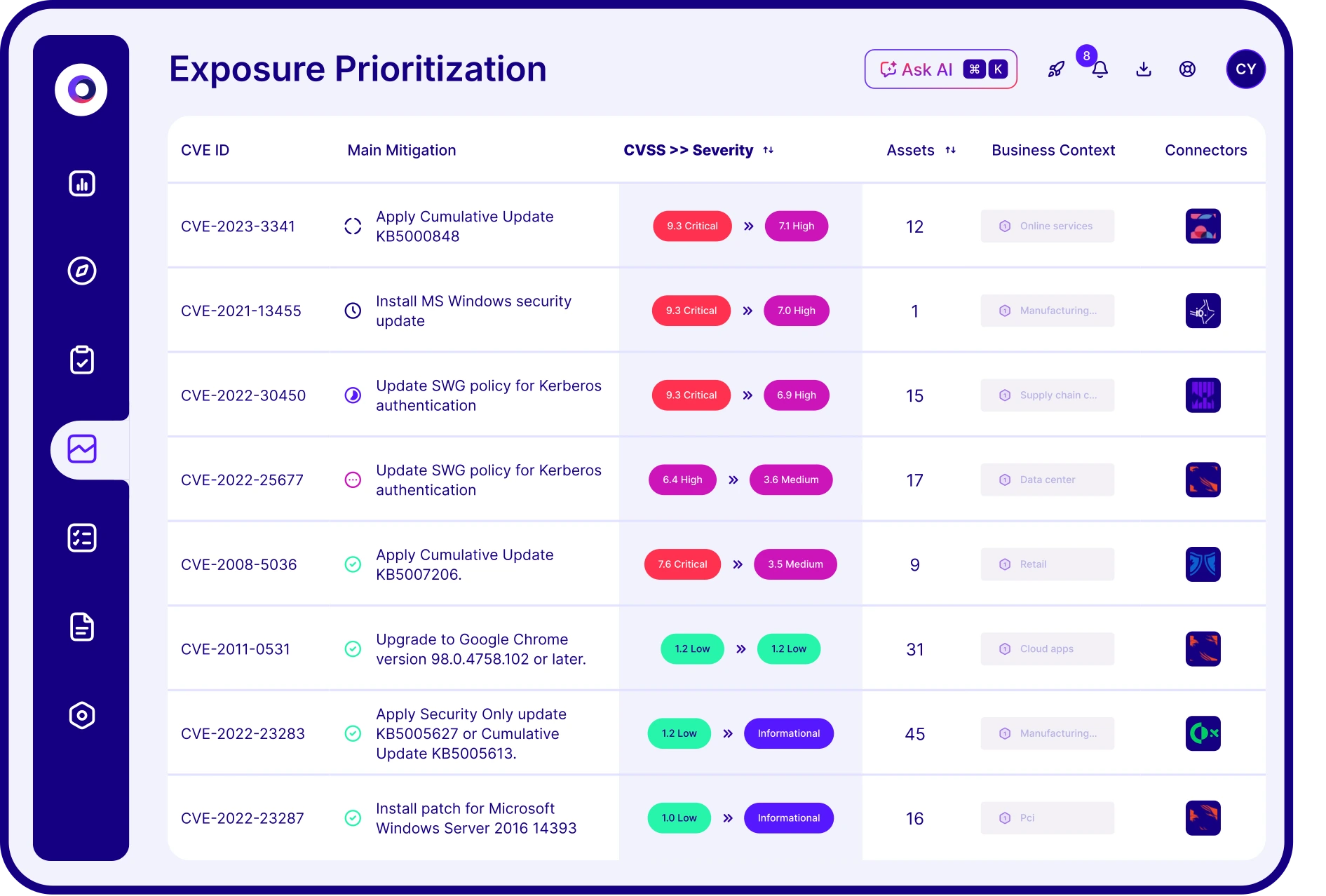
Cymulate surfaces the exposures that can be exploited now and uses AI-powered automation to accelerate the actions that shut them down.
The only CTEM platform designed specifically
for true defense orchestration
How we help
threats
validated
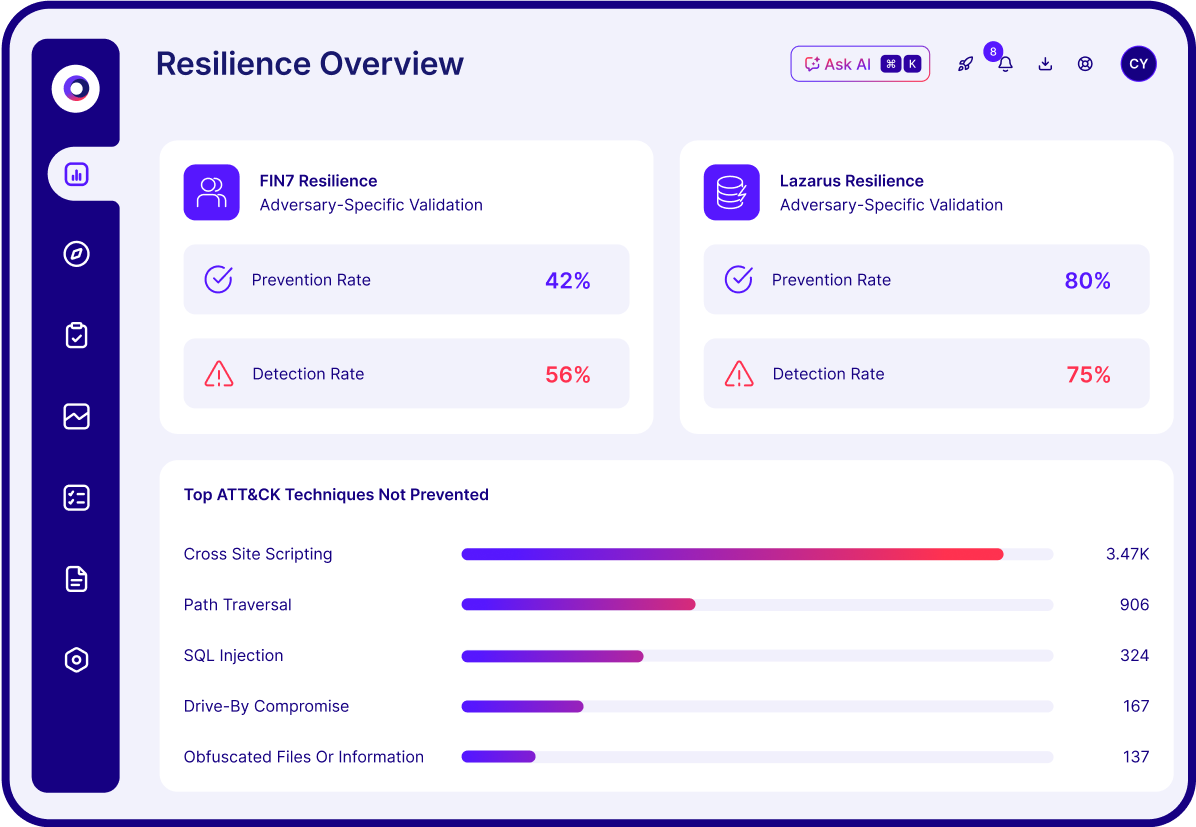
Full-spectrum validation across tools, controls, and environments—so you know exactly where defenses fail.
Our customers see around corners.
Operational Outcomes You Can Expect
40X
Faster threat validation, from days to hours
85%
Improvement in threat detection accuracy
24/7
Continuous security posture monitoring
Our edge. Your advantage.
The Cymulate Difference
Continuous Threat Validation
24/7 automated attack simulation to validate your security posture in real-time
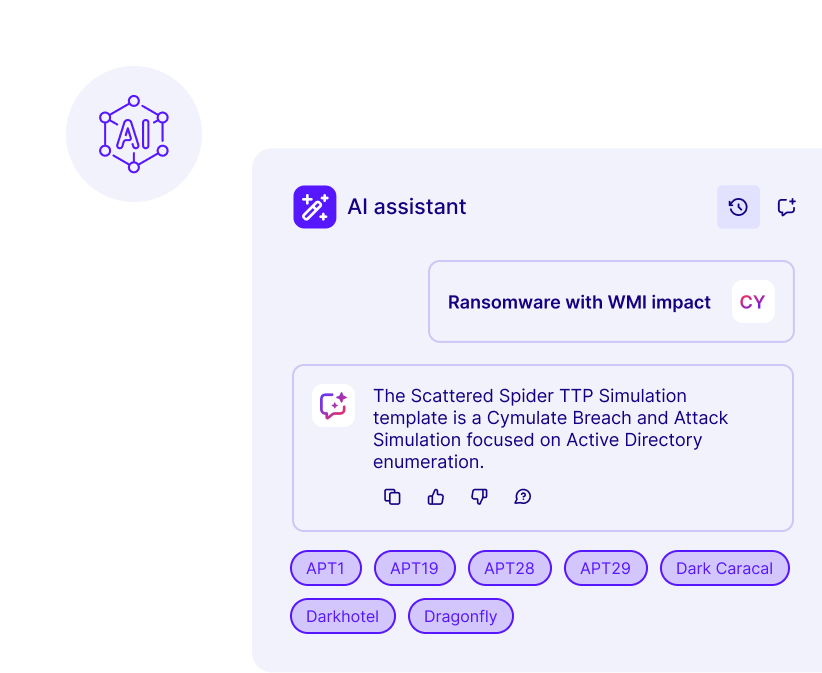
AI-Powered Optimization
Machine learning algorithms provide actionable insights for security improvement
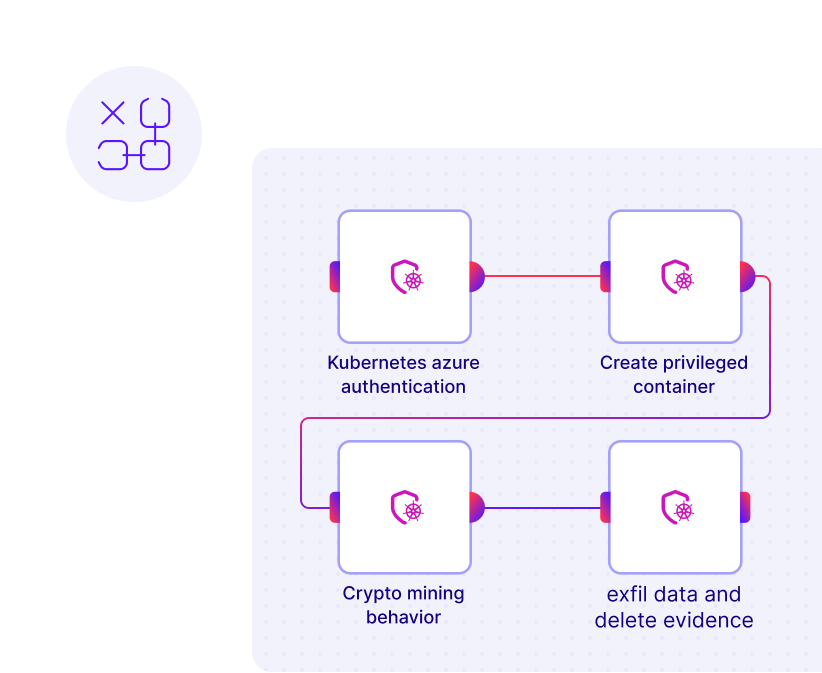
Complete Kill Chain Coverage
Full attack lifecycle simulation from initial access to data exfiltration
Go ahead. Compare us.
Why We’re Leading the Market
Cymulate vs. BAS Platforms (AttackIQ, SafeBreach, Picus)
Cymulate delivers AI-driven, easy to deploy, continuously updated attack simulations with automated and actionable, vendor-specific remediation.
Cymulate vs. Automated Pen-Testing (Pentera, H3)
Automated pen-testing identifies vulnerabilities. Cymulate delivers continuous, safe and scalable adversarial simulation.
Cymulate vs. Security Control Assessment Tools
Unlike security control assessments, Cymulate validates threats with production-safe attack simulation.
Cymulate vs. Traditional Vulnerability Management
Unlike vulnerability management, Cymulate validates threat exposure with production-safe attack simulation.
Cymulate vs. Red Teaming frameworks (Scythe, Metasploit, Cobalt Strike)
Cymulate delivers AI-driven, easy to deploy, continuously updated attack simulations with automated and actionable, vendor-specific remediation – unlike red team tools that only focus on testing without a path to improvement.
See what the buzz is about.