IF YOU'RE NOT VALIDATING, YOU'RE NOT PROTECTING
Exposure Validation
Surface the threats that can actually be exploited with the most comprehensive combination of validation techniques, in an AI-powered platform that's easy to use.
Security teams are overwhelmed by the large number of potential exposures found in their organizations.
New security flaws
reported daily
Source: Dark Reading
Vulnerabilities
patched each month
Source: Bitsite
Breaches involve
unpatched vulnerabilities
Source: Ponemon Institute
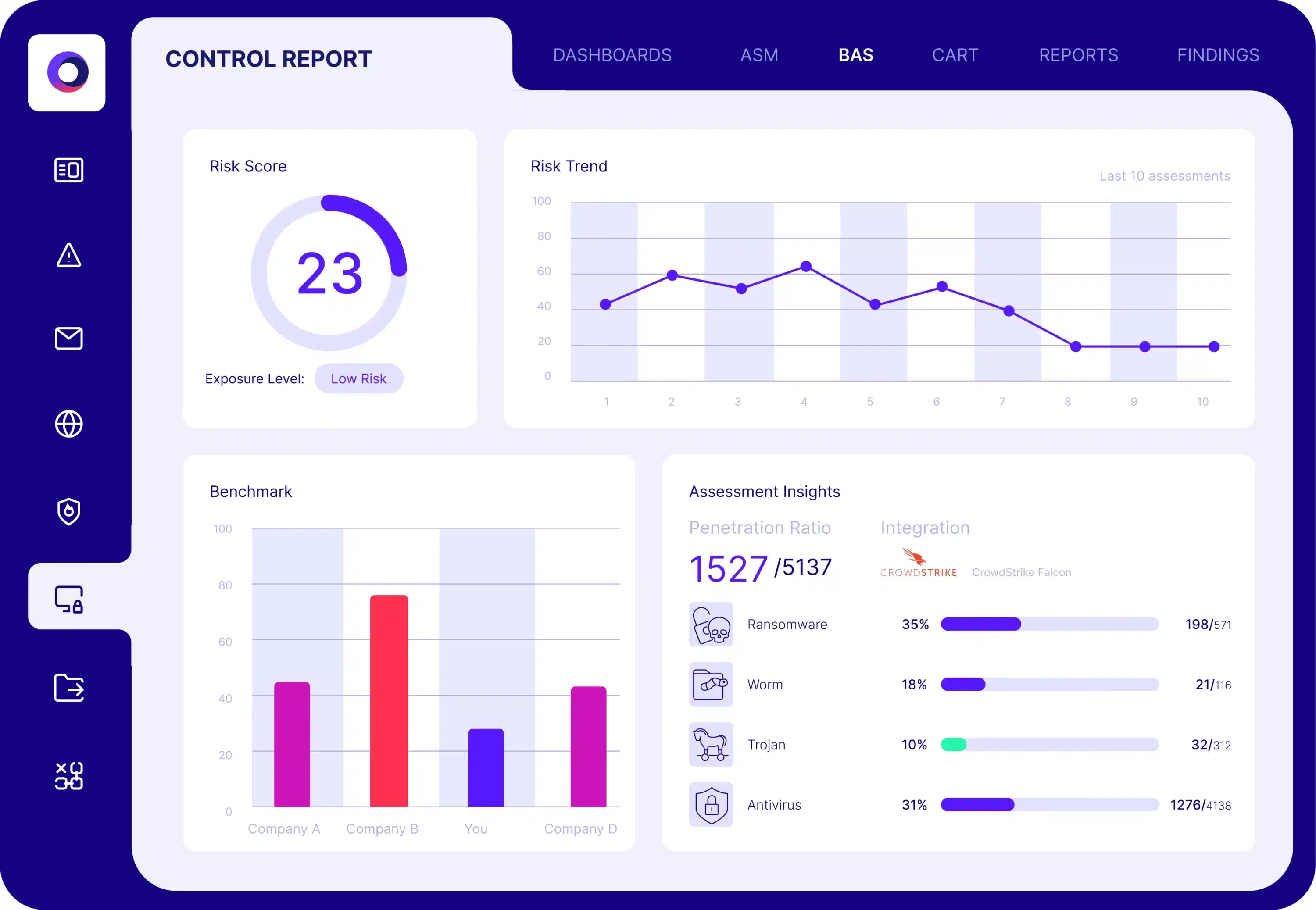
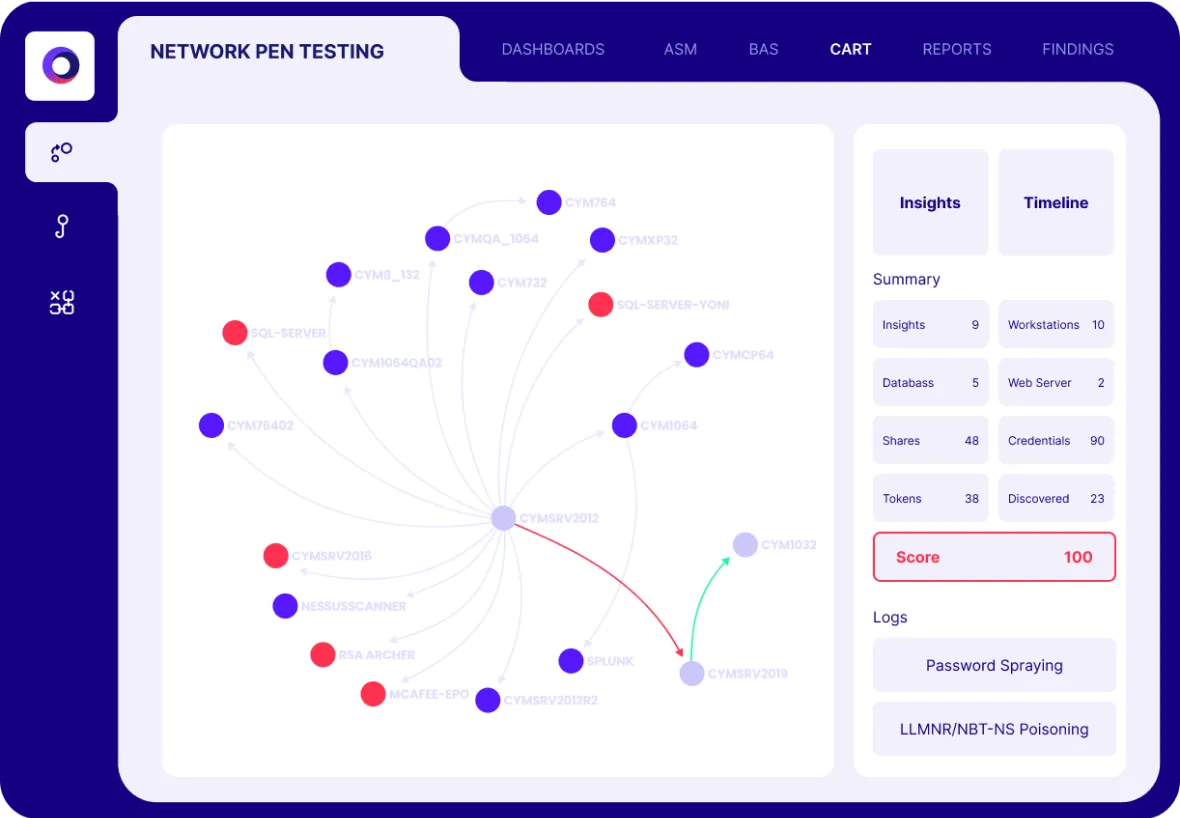
Focus on True Exposures
With market-leading breach and attack simulation and automated red teaming, Cymulate puts validation at the heart of exposure management, so you can focus on what’s truly exploitable in your environment.
Exposure Validation Solution Results
81%
Improvement in risk
score in four months
global transportation
168
Exploits prevented
from one policy change
healthcare company
60%
Increase in team
efficiency
FINANCE COMPANY
Solution Benefits
Customers are saying...
Organizations across all industries choose Cymulate to drive their exposure management programs with exposure validation.