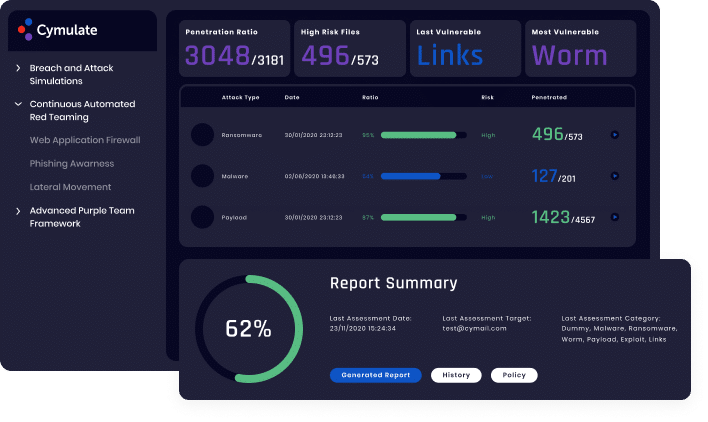
The Challenge: Scaling Adversarial Activities
It can be difficult to scale Red Teaming activities because Red Teamers’ daily responsibilities are time-consuming and labor-intensive, leaving less opportunity for high value tasks. Additionally, a Red Teamer‘s level of expertise can limit the effectiveness of an assessment; an assessment is only as good as the skills of the person running it.
The Solution
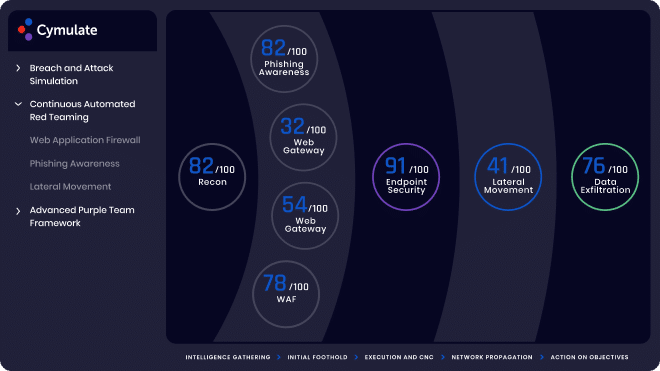
Cymulate provides Red Teams a platform to increase their operational efficiency and optimize their adversarial activities in a production-safe environment. Cymulate’s Red Team capabilities include Attack Surface Management (ASM), Phishing Awareness, Lateral Movement, Full-Kill Chain Advanced Persistent Threat (APT) Campaign, and Advanced Scenarios. These capabilities enable Red Teamers to:
- Automate assessment scripts and repetitive, labor-intensive manual tasks
- Scale adversarial activities by simultaneously running hundreds of attacks at the level of a team’s most seasoned expert
- Customize attacks with the freedom to create, modify, and run chained or atomic attack campaigns
Blue Teams that want to run offensive campaigns can also benefit from these capabilities with easy-to-use, out-of-the-box assessments. Additionally, these capabilities enable Blue Teams to improve adversarial skills on the job and decrease time to mitigation.
Benefits

Reduce Tedious Tasks

Accurately Assess Breach Feasibility
Increase Collaboration
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation