The Challenge: Anyone Can Fall for Phishing Attacks
Despite significant investments in email security, phishing and business email compromise remains a top “action variety” seen in breaches. In 2021, 43% of breaches involved phishing and/or pretexting according to Verizon’s 2021 Data Breach Investigations Report (DBIR). It is difficult to identify the employees who might compromise the security of an organization until it is too late.
The Solution
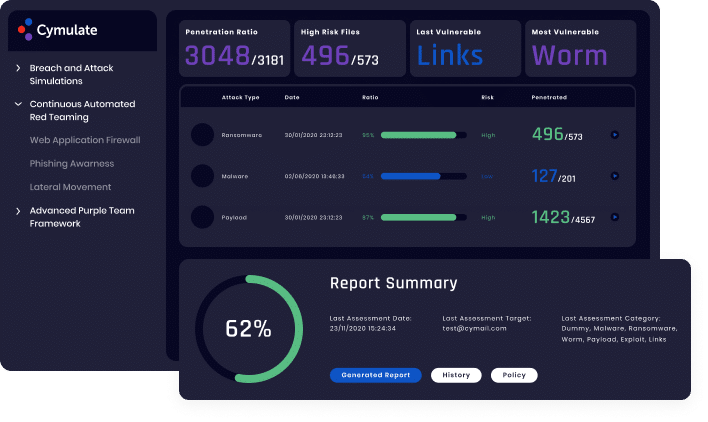
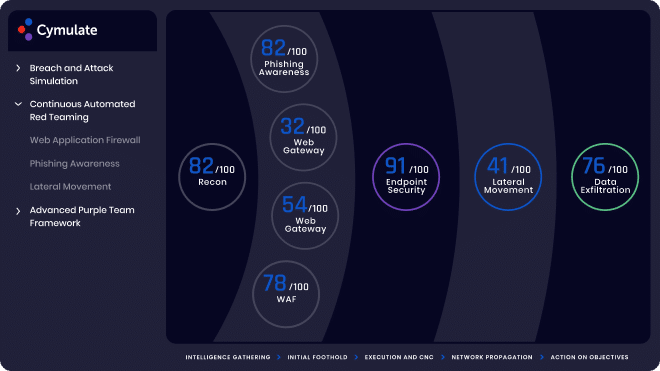
Cymulate’s Phishing Awareness vector is designed to evaluate employees’ security awareness. It simulates phishing campaigns and identifies potential target opportunities.
Since it is designed to reduce the risk of spear-phishing, ransomware or BEC fraud, the solution helps prevent data breaches, minimize malware-related downtime, and save money on incident response. Security awareness among employees is tested by creating and executing simulated, customized phishing campaigns enabling companies to maintain a high level of awareness.
Benefits

Assess Employee Awareness

End-to-End Evaluation

Promote Security Awareness
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Mergers and Acquisitions
Comprehensive M&A security posture analysis of planned acquisitions

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation