Automate the Attacker’s View of Your Organization to Discover Weaknesses & Prioritize Remediation
Cymulate Attack Surface Management (ASM) discovers vulnerabilities and misconfigurations to identify assets exposed to unapproved access, exploits, and other attacks. These scans automate the attacker’s view of your organization. With a comprehensive assessment of vulnerabilities, misconfigurations, and over-provisioning, Cymulate ASM enables organizations to identify and prioritize the security weaknesses. Cymulate ASM empowers organizations to manage their attack surface proactively, combining advanced scanning, detailed insights, and mitigation guidance to strengthen their security posture.
Benefits of Cymulate Attack Surface Management

Comprehensive Visibility
Identify external systems and vulnerabilities, both on-prem and in the cloud.

Enhanced Prioritization
Target remediation to close gaps in critical systems, resources, and data

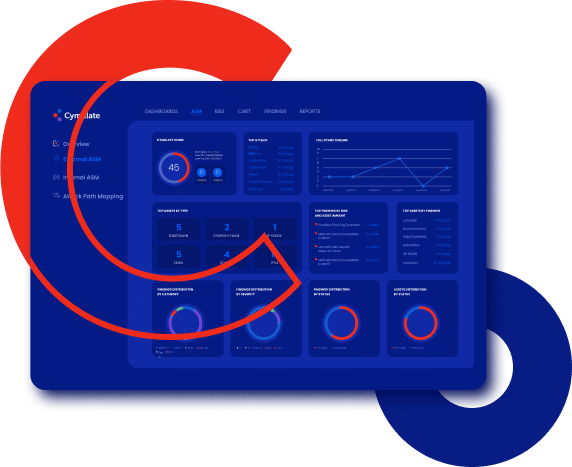
Risk Scoring
Track and trend risk scores for continuous improvement and benchmark against peers
Easy to Deploy & Manage
Agentless solution to identify, diagnose, manage, control, and validate your attack surface
Cymulate Exposure Management & Security Validation Platform
Cymulate Attack Surface Management is available both as a standalone SaaS offering and as an integrated offering within the Cymulate Exposure Management and Security Validation Platform.


“I chose to implement Cymulate ASM because I wanted intelligence on my assets, not just a long list of vulnerabilities that a vulnerability management tool would give me.”
-Shaun Curtis, Head of Cybersecurity, GUD Holdings Limited
Environments
Cymulate provides extensive coverage of on-prem and cloud environments to identify
vulnerabilities and misconfigurations with attack path maps for each security gap.
On-premises
- Internal Systems
- Legacy Applications
- User Networks
Cloud
- IaaS
- Containers
- Serverless/APIs

Hybrid
- Remote Workers
- Shared Services
- Cloud Storage
Backed By the Industry

Cymulate Recognized as ASM Leader
GigaOM announced in its Key Criteria for Evaluating Attack Surface Management (ASM) Solutions, 2024 report

Cymulate Receives Global Infosec Awards 2024
Recognized for Hot Company Attack Surface Management
Related Resources
Attack Surface Management FAQs
ASM is the ongoing process of discovering points within data systems that could be used to attack the organization (servers, applications, services, cloud components, workstations, etc.) and defining and implementing remediation strategies to address gaps.
Cymulate ASM is designed to meet the needs of businesses of all sizes and industries. The platform provides organizations with comprehensive visibility into their digital assets and potential vulnerabilities. Cymulate ASM uses automated scanning to identify potential attack vectors within on-prem, hybrid, and cloud environments and provides real-time insights and recommendations for mitigating risk. This helps businesses proactively manage their attack surface and reduce their exposure to cyber threats.
Cymulate ASM automates the attacker’s view of your on-prem, cloud, and hybrid environments by identifying vulnerabilities and misconfigurations in autonomous system numbers (ASN), domains (email and web), subdomains, IPs, ports, services, applications, and cloud platforms. The platform also scans the dark web for sensitive information and indicators of data leaks and cyberattacks.
The external attack surface of an organization includes sensitive or proprietary information stolen from the organizations that ends up for sale or exchange on the dark web, which potentially leads to further attacks or breaches. Both the dark web and publicly available information contribute to an organization’s external attack surface by providing intelligence about the organization that attackers can use to target systems, accounts, and individuals.
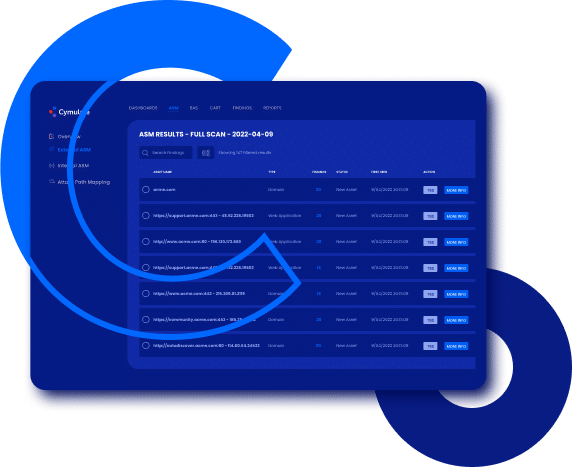
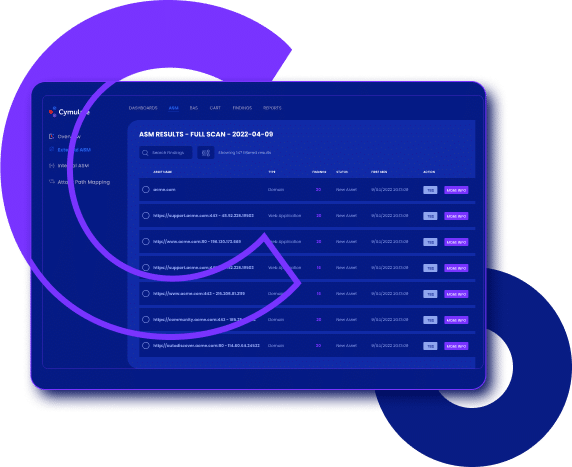
Cymulate ASM includes asset discovery scans and monthly comprehensive scans. Asset Discovery Scans are weekly, non-intrusive scans that identify assets within an organization’s IT infrastructure. The scan helps organizations gain visibility into their assets, including any unauthorized devices or software. The monthly Full Scans conducted provide a comprehensive assessment of an organization’s IT infrastructure. It identifies all assets within the infrastructure and performs vulnerability scanning on domains, subdomains, applications, and infrastructure. The full scan detects vulnerabilities, web misconfigurations, open ports, and more. The results of the full scan include a detailed report of discovered assets, vulnerability findings, and a risk score to help organizations prioritize their mitigation efforts effectively.
No, Cymulate ASM is designed to assess and monitor an organization’s external digital footprint—the part of its network that is visible from the outside, such as exposed web servers, applications, and services. This assessment is done from the perspective of an external attacker looking for publicly accessible systems and vulnerabilities that could be exploited.