The Challenge: Due Diligence of Mergers & Acquisitions
Including cybersecurity due diligence in the merger or acquisition process has become a central concern when evaluating potential acquisitions. Prior to an M&A, the acquiring party’s objective is to identify financial or reputational risks to the acquiring party. Post–M&A, their objective is to securely execute the integration strategy. While standard security auditing practices provide a high-level view of the security matureness of the intended acquisition, it lacks data about the operational effectiveness of their security stack at the post–M&A integration stage. Acquiring companies want to accelerate post–M&A cybersecurity due diligence so that the business can reap the benefits of integration quickly and securely.
The Solution
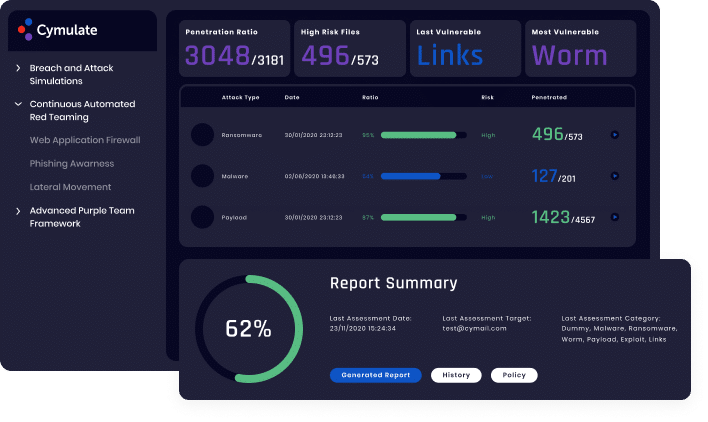
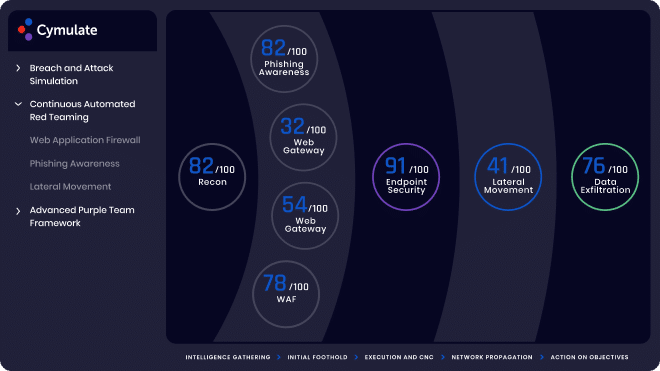
SaaS–based Cymulate enables companies to perform rapid risk assessments for cyber security due diligence. By performing a full kill-chain security validation assessment on the M&A target infrastructure, the acquiring company gains comprehensive visibility on the operational effectiveness of the target’s security stack. Furthermore, non-intrusive, outside-in reconnaissance provides attack surface visibility and security intelligence on the target company to identify risk prior to the M&A. By incorporating security validation in the cybersecurity due diligence life cycle of M&As, companies can assess risk and accelerate time to value by gaining comprehensive security visibility of the target company fast.
Benefits

Comprehensive Risk Visibility

Streamlined Absorption

Prevent Potential Risk
Learn More
Simply Know
Control and assure the security posture
of your organization with the most
comprehensive Extended Security Posture Management platform.
More Solutions
Learn how Cymulate makes it easy to keep all angles of your company safe and secure.

Security Control Validation
Comprehensive SIEM/SOC and IR assessment with many scenarios permutations

SIEM Validation
Optimized SIEM Performance
with enhance detection and
reduced false positives

Operationalizing Threat Intelligence
Continuously updated emerging threats resilience evaluation

Cloud Security Validation
Continuous cloud security control validation and mitigation optimization

Attack Surface Management
Continuous Security Validation with 360°
exposure visibility, comprehensive
threat vector identification
and resilience scoring

Attack Based Vulnerability Prioritization
Data backed optimized mitigation prioritization

SOC and SOAR Validation
End-to-end threat detection and IR playbook optimization through comprehensive automated continuous security validation