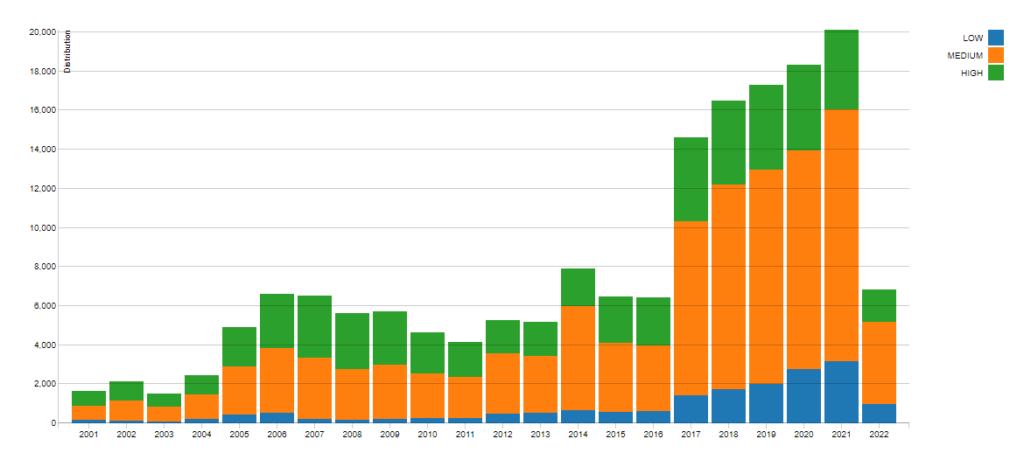
The combination of the continuously changing threat landscape and the evolution of complex IT environments generate new potential attack paths every day. With the number of vulnerabilities increasing exponentially (see figure 1), vulnerability management can no longer rely only on the Common Vulnerability Scoring System (CVSS) to determine a patching schedule. CVSS scores are an invaluable element to incorporate when establishing a vulnerability patching schedule, but they do not fully describe each vulnerability; a CVSS score lacks context. Unfortunately, common Vulnerability Scanners and Risk-Based Vulnerability Management tools are mainly based on CVSS scores and do not take into consideration compensating controls, the chance of being exploited, or evaluate the actual risk posed by a vulnerability.
Vulnerability Prioritization Demands Context
Context is essential for vulnerability management because it enables you to truly understand:
- If a vulnerability can be exploited
- How a vulnerability can be exploited and the various ways it can be leveraged by an attacker
- If an exploited vulnerability can allow an attacker to escalate or move laterally within your environment
- Which assets a vulnerability affects
- If there are compensating controls in place to prevent a vulnerability’s exploitation
For example, without context, you might decide to patch a vulnerability with a CVSS score of 10 when you unknowingly have compensating controls already in place that prevent its exploitation.
Using Attack Simulation to Add Context
The best way to understand a vulnerability in context is through simulated attacks. If you simulate an attack based on the exploitation of a specific vulnerability, it can provide invaluable information about the vulnerability itself. Breach and Attack Simulation (BAS) is an efficient method to validate security controls and can provide an added dimension to vulnerability management.
The latest and most advanced Vulnerability Prioritization Technology (VPT) in the market is Context Vulnerability Management (CVM). CVM incorporates both simulated and emulated attacks into your vulnerability management to provide the full context of a vulnerability in your specific IT environment to establish a vulnerability patching schedule. The context that simulated attacks provide allows you to:
1. Consider compensating controls
By analyzing the results of simulated and emulated attacks, an organization can prioritize a vulnerability’s required patching criticality based on its environment’s actual exposure. It considers compensating security controls and deprioritizes vulnerabilities defended by security controls already in place. Discovering that a vulnerability with a high CVSS score isn’t accessible in your environment allows your team to focus on patching the vulnerabilities that can be exploited. Additionally, a company can determine if fine-tuning other security controls is enough to prevent an exploit until the next scheduled patching window. Alternatively, a simulated attack may determine that a vulnerability with a low CVSS score can be used to reach critical assets and needs to be patched urgently. When a company has complete visibility of its IT environment end-to-end, it increases team efficiency and maximizes resources.
2. Measure and communicate value
BAS tools collect data and analytics that security leaders can use to measure and convey vulnerability management efficacy and impact on security posture to executive leadership. Instead of reporting how many vulnerabilities they patched, they can quantify the impact their patching activity has on their security posture and even focus this measurement down to an individual patch if required. The ability to use metrics facilitates communication with executives who do not understand the technical effects of fine-tuned security controls.
3. Increase team efficiency and maximize resources
BAS tools enable organizations to correlate the criticality of vulnerabilities with the value of assets, allowing them to optimize patching prioritization and reduce the patching workload. If the same asset appears in multiple simulated attacks, an organization can focus its remediation efforts on strengthening the controls surrounding that one asset instead of patching multiple vulnerabilities. This makes a significant impact in less time, with minimal resources. Additionally, the results of simulated attacks improve workload management and help avoid downtime. For example, an organization can determine if a patch needs to be taken care of immediately because there is a high risk to the entire business or, alternatively, if the patch can wait until the next patching window.
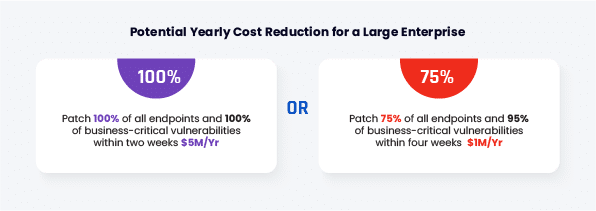
Maximize Impact and Reduce Risk with CVM
Production–safe simulated attacks provide organizations with a comprehensive view of their IT environment and add context to uncovered vulnerabilities. When correlated with assets’ business values, it enables fine-tuning the patching prioritization schedule to maximize impact on risk exposure and remain within defined risk tolerance limits.
CVM is a direct result of production–safe attacks launched proactively to assess an IT environment’s resilience. The information yielded by those assessments provides security teams immediate answers to the effectiveness of compensating controls protecting vulnerable machines, enabling them to accurately prioritize remediation, patching, or reconfiguration of compensating security controls. With CVM, you can reduce risk, in less time, with less manpower.
For a free demo and more information about how to use CVM to stay ahead of the game and prioritize your vulnerabilities, click here >>








