Unlock Success with Risk-Based Vulnerability Management
Risk-based vulnerability management is the latest recommended approach to adapt vulnerability assessment (VA) and vulnerability management (VM) to technological and threat landscape evolution and should be at the center of vulnerability prioritization technologies (VPTs) development.
It introduces a switch in perspective from focusing on whether a system gets patched to whether the specific risk of a system vulnerability has been sufficiently mitigated.
By shifting the focus from routine patching to mitigating specific risks, a Risk-Based Vulnerability Management (RBVM) approach offers a proactive and strategic way to enhance cybersecurity measures. This change in perspective aligns with the evolving technological and threat landscape, making it a crucial aspect of modern vulnerability management strategies.
Risk-based vulnerability management represents a paradigm shift in cybersecurity strategies, emphasizing the mitigation of specific risks over routine patching. By adopting this approach, organizations can proactively enhance their security measures by focusing on addressing vulnerabilities with the greatest risk. This evolution in vulnerability management practices, also known as risk management, is essential to keep pace with the constantly changing technological and threat landscape, ensuring a more effective and strategic defense against cyber threats, especially when compared to outdated legacy vulnerability management tools.
This post examines the logic behind that recommended switch in perspective and ways to put it in practice.
The Risks of Relying Mainly on CVSS Scores
Prioritizing patching schedules has traditionally focused on patching vulnerabilities with a high CVSS score first. Yet, a high CVSS score does not necessarily point to a high probability of exploitation. Sometimes, they are even downright inaccurate, as, for example, the CVE-2020-19909 that was published with a 9.8 severity score long after the issue had been fixed. However, relying mainly on CVSS scores can leave organizations vulnerable to software vulnerabilities that may not have a high score but are still exploitable, highlighting the importance of considering the overall risk level of a vulnerability.
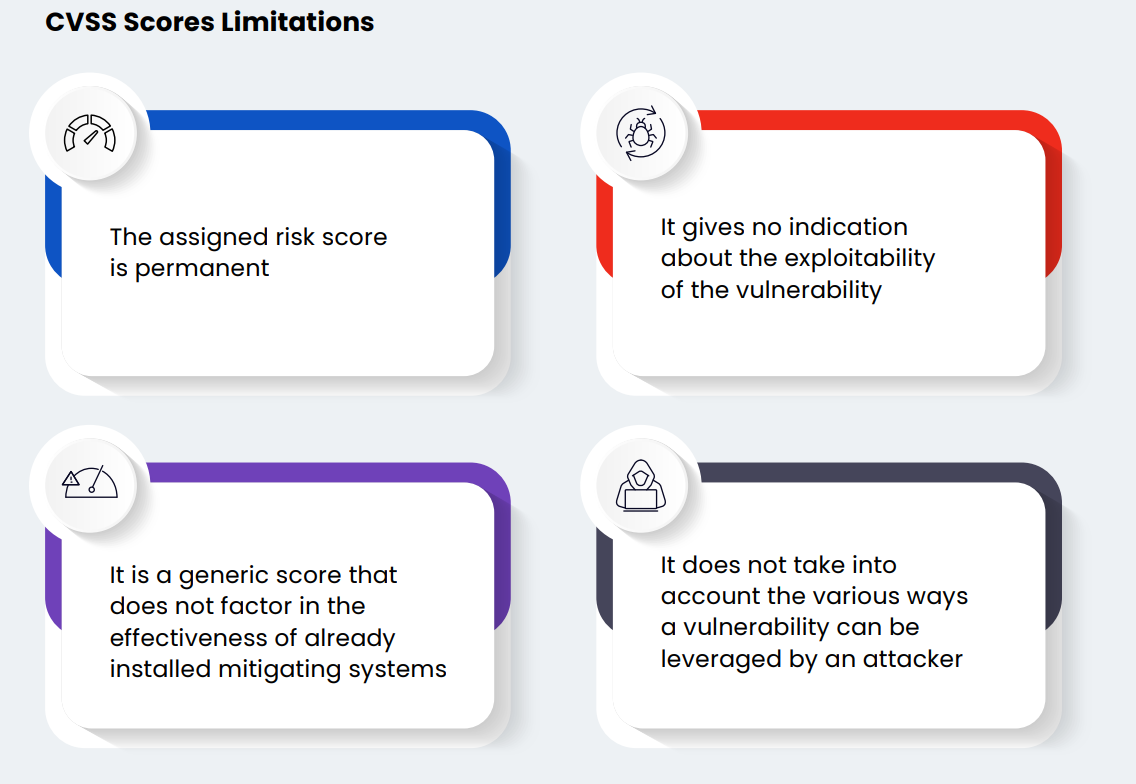
In short, focusing primarily on severity scores might causes defenders to invest their too scarce time for little benefit.
Remediation processes are unfortunately not instantaneous. According to the Infosec Institute, the average time to patch a vulnerability is between 60 and 150 days, and security and IT teams tend to take at least 38 days to push out a patch.
For critical vulnerabilities that present immediate risk to the organization, 38 days is much too long of an exposure window. But 38 days or longer may be acceptable for vulnerabilities protected by compensating controls or face no imminent threat activity.
To tackle this issue, Gartner and other thought leaders are now advocating the adoption of what they call risk-based vulnerability management (RBVM).
What is a Risk-Based Vulnerability Management Approach?
In an April 2023 report, Gartner asserted that “RBVM is different from traditional VM methodologies — namely, in its focus on applying risk quantification targeting to your specific threat landscape and advocating for a range of compensatory methods outside of just patching.”
Risk-based vulnerability management involves identifying and prioritizing the most critical vulnerabilities that pose the highest level of risk to a business. By focusing on these vulnerabilities, organizations can allocate resources more effectively and address the most pressing security concerns. This approach allows security teams to proactively mitigate risks and enhance their overall security posture. Through the use of threat intelligence and data-backed security decisions, organizations can ensure they are targeting the vulnerabilities that have the most significant impact on their business operations, thus focusing on the likelihood of a vulnerability being exploited.
Embracing a Risk-Based Vulnerability Management (RBVM) approach marks a crucial shift in how security and IT teams address vulnerabilities within an organization. By prioritizing critical vulnerabilities based on the level of risk they pose, companies can streamline their response efforts effectively. This strategic focus enables resources to be allocated where they are most needed, heightening the overall security posture of the organization. Ultimately, RBVM empowers teams to proactively address potential threats and make informed decisions rooted in data and threat intelligence, ensuring a targeted and impactful vulnerability management strategy.
Practically, that means evaluating the vulnerabilities threat severity based on its exploitability in context. When compensating controls are reducing or eliminating the possibility to actually exploit a vulnerability, it can remove the urgency of remediating CVSS with a high vulnerability severity score. Conversely, a lower scored CVE with a higher exploitability risk and vulnerability risk should be pushed higher in the prioritization schedule, streamlining remediation efforts.
Implementing a Risk-Based Vulnerability Management (RBVM) Approach
To encourage moving from a theoretical stance to a practical one, that Garner report highlighted “enabling technologies” to implement risk-based vulnerability management, such as:
- External attack surface management (EASM)
- Breach and attack simulation (BAS)
- Vulnerability prioritization technology (VPT)
External Attack Surface Management
As defined by Gartner, external attack surface management (EASM) is “the processes, technology and managed services deployed to discover internet-facing enterprise assets and systems and associated exposures.” EASM thus enables a risk-based vulnerability management program based an overall visibility of assets and their respective risks.
Increasingly, EASM is converging with vulnerability scanners to combine vulnerability assessments of both internal and external assets with identifying misconfigurations in on-prem, cloud, and hybrid environments.
Breach and Attack Simulation
Breach and Attack Simulation (BAS) automates the continuous testing of threat vectors to validate controls, assess the impact of emergent threats, and confirm threat exposure risk. Gartner asserts that BAS enables a risk-based vulnerability management program with their “demonstrable capability to proactively highlight how vulnerabilities will directly affect your environment, utilizing vulnerability intelligence and exposure analytics.”
Cymulate Breach and Attack Simulation (BAS) validates cybersecurity controls by safely conducting threat activities, tactics, techniques, and procedures in production environments. Cymulate BAS helps prioritize vulnerabilities by validating the security controls that are designed to prevent exploits of those vulnerabilities, such as a web application firewall protecting a web app’s vulnerabilities and weaknesses.
In a dynamic cybersecurity landscape, the need for robust risk-based vulnerability management is paramount. Identifying vulnerabilities and misconfigurations across on-prem, cloud, and hybrid environments is crucial in safeguarding organizational assets from potential threats. Attack Surface Management emerges as a pivotal tool in this endeavor, facilitating the discovery of vulnerabilities and misconfigurations to pinpoint assets vulnerable to unauthorized access and malicious exploits.
However, without proper context, legacy vulnerability management may not be able to effectively protect your modern attack surface. This lack of context can cause your security team to waste time chasing after the wrong issues, while missing many of the most critical vulnerabilities that pose the greatest risk to your business. To truly master risk-based vulnerability management, it is important to incorporate breach and attack simulation to gain a comprehensive understanding of your organization's security posture.
Moreover, Breach and Attack Simulation (BAS) emerges as a proactive approach to continuously test threat vectors, assess emerging threats’ impact, and validate controls. By conducting simulated threat activities in production environments.
In the realm of cybersecurity, the concept of risk-based vulnerability management has become increasingly crucial. As organizations navigate through a dynamic landscape fraught with emergent threats, the need to assess and confirm threat exposure risk is more critical than ever. BAS, as advocated by Gartner, offers a proactive approach by highlighting vulnerabilities' direct impact on an environment through vulnerability intelligence and exposure analytics, providing valuable insights into potential impacts of a breach or attack.
Cymulate Breach and Attack Simulation (BAS) plays a pivotal role in this scenario by validating cybersecurity controls in real-world settings, prioritizing vulnerabilities, and safeguarding assets across varied environments. Its ability to simulate threat activities.
In the ever-evolving realm of cybersecurity, risk-based vulnerability management stands as a cornerstone in defending against potential threats and breaches. By leveraging tools like Cymulate Attack Surface Management and Breach and Attack Simulation (BAS), organizations can proactively identify vulnerabilities, assess threat impact, and strengthen their security posture.
Cymulate's BAS not only helps in pinpointing assets vulnerable to attacks but also validates cybersecurity controls in real-world scenarios, offering a comprehensive approach to safeguarding critical assets. The continuous testing of threat vectors ensures that vulnerabilities are identified and mitigated promptly, reducing the organization's overall risk exposure.
Vulnerability Prioritization Technology
Vulnerability prioritization technology (VPT) “streamlines a range of vulnerability telemetry sources into a single location — using intelligence sources, analytics, and visualizations and to efficiently provide prioritized, pragmatic recommendations on how best to perform critical remediation/mitigation activities.”
Gartner indicates that VPTs could contribute to a risk-based vulnerability program if they were to “apply quantitative methods to drive the focus of your VM process so that the most pressing threats are addressed as the highest priority.”
In the realm of cybersecurity, the concept of risk-based vulnerability management stands as a crucial pillar in fortifying defenses against potential exploits and threats. By leveraging tools such as web application firewalls to shield weaknesses, organizations can proactively mitigate risks that could compromise their digital assets.
In the realm of cybersecurity, Risk-Based Vulnerability Management (RBVM) emerges as a strategic approach to fortify defenses against potential exploits and threats. By leveraging tools such as Cymulate Breach and Attack Simulation (BAS), organizations can proactively identify vulnerabilities, assess threat impact, and strengthen their security posture.
Cymulate's BAS plays a pivotal role by pinpointing assets vulnerable to attacks and validating cybersecurity controls in real-world scenarios. This comprehensive approach ensures that vulnerabilities are identified and mitigated promptly through continuous testing of threat vectors, ultimately reducing the organization's overall risk exposure.
Amidst the ever-evolving landscape of cyber threats, the significance of robust vulnerability management strategies cannot be overstated.
VPT vs. Cymulate Exposure Analytics
While many vulnerability assessment tools are adding features to aid in prioritization, Cymulate takes a more holistic approach. It integrates an RBVM approach into the Cymulate Threat Exposure and Security Validation Platform as a feature of the Exposure Analytics solution.
Exposure Analytics pulls data from vulnerability management platforms, asset inventories, clouds, security controls, and the IT infrastructure. By integrating with tools for breach and attack simulation and continuous automated red teaming, Cymulate Exposure Analytics creates a risk score that considers the exploitability and effectiveness of compensating security controls.
The result is a contextualized vulnerability prioritization that correlates findings with both security findings severity and business priorities.
Exposure Analytics increases the benefits of implementing an RBVM approach by offering the built-in capability of correlating findings with user-defined business priorities and offering the options of either using Cymulate BAS and CART tools or integrating with external security validation processes.
The significance of robust vulnerability management strategies cannot be emphasized enough in today's cybersecurity landscape. The incorporation of Cymulate Attack Surface Management within an organization's security framework represents a strategic step towards identifying and mitigating vulnerabilities across varied environments, thereby enhancing resilience against unauthorized access and cyber threats.
In the realm of vulnerability assessment tools, Cymulate stands out with its comprehensive approach compared to traditional methods. By integrating a Risk-Based Vulnerability Management (RBVM) approach into the Cymulate Threat Exposure and Security Validation Platform through Exposure Analytics, organizations can leverage a holistic solution that pulls data from various sources like vulnerability with unmatched accuracy.