Frequently Asked Questions
Product Overview & Purpose
What is Cymulate's Exposure Management Platform?
Cymulate's Exposure Management Platform is a comprehensive solution designed to help organizations continuously identify, validate, and prioritize security exposures across their digital ecosystem. It enables security teams to focus on exploitable risks, optimize threat resilience, and drive measurable improvements in their security posture through continuous threat exposure management (CTEM).
What is the primary purpose of Cymulate's Exposure Management solution?
The primary purpose of Cymulate's Exposure Management solution is to proactively validate cybersecurity defenses, identify vulnerabilities, and optimize security posture. It empowers security teams to stay ahead of emerging threats and improve overall resilience by simulating real-world attacks, prioritizing exposures, and automating remediation.
How does Cymulate's Exposure Management Platform support CTEM?
Cymulate supports Continuous Threat Exposure Management (CTEM) by continuously validating threats, integrating with vulnerability management and exposure discovery tools, and enabling collaboration across security operations, red teams, and vulnerability management teams. This approach ensures a focus on proven, validated threats that measurably improve threat resilience. Learn more.
Who is the target audience for Cymulate's Exposure Management solution?
Cymulate's Exposure Management solution is designed for CISOs, security leaders, SecOps teams, red teams, and vulnerability management teams in organizations of all sizes and industries, including finance, healthcare, retail, media, transportation, and manufacturing. Learn more about roles.
Features & Capabilities
What are the key features of Cymulate's Exposure Management Platform?
Key features include continuous threat validation, unified platform for BAS, CART, and Exposure Analytics, attack path discovery, automated mitigation, AI-powered optimization, complete kill chain coverage, ease of use, and an extensive threat library with over 100,000 attack actions updated daily. See full feature list.
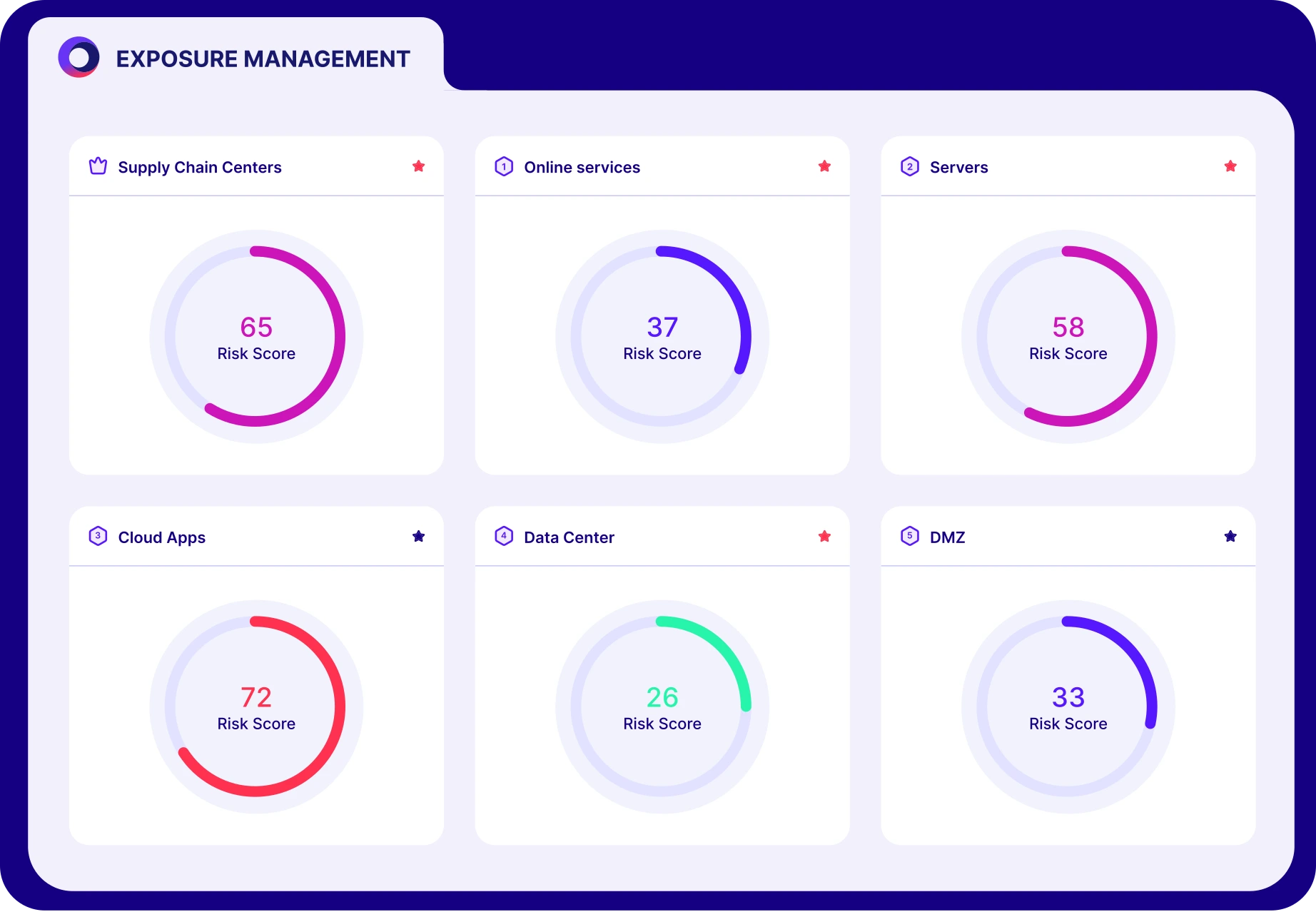
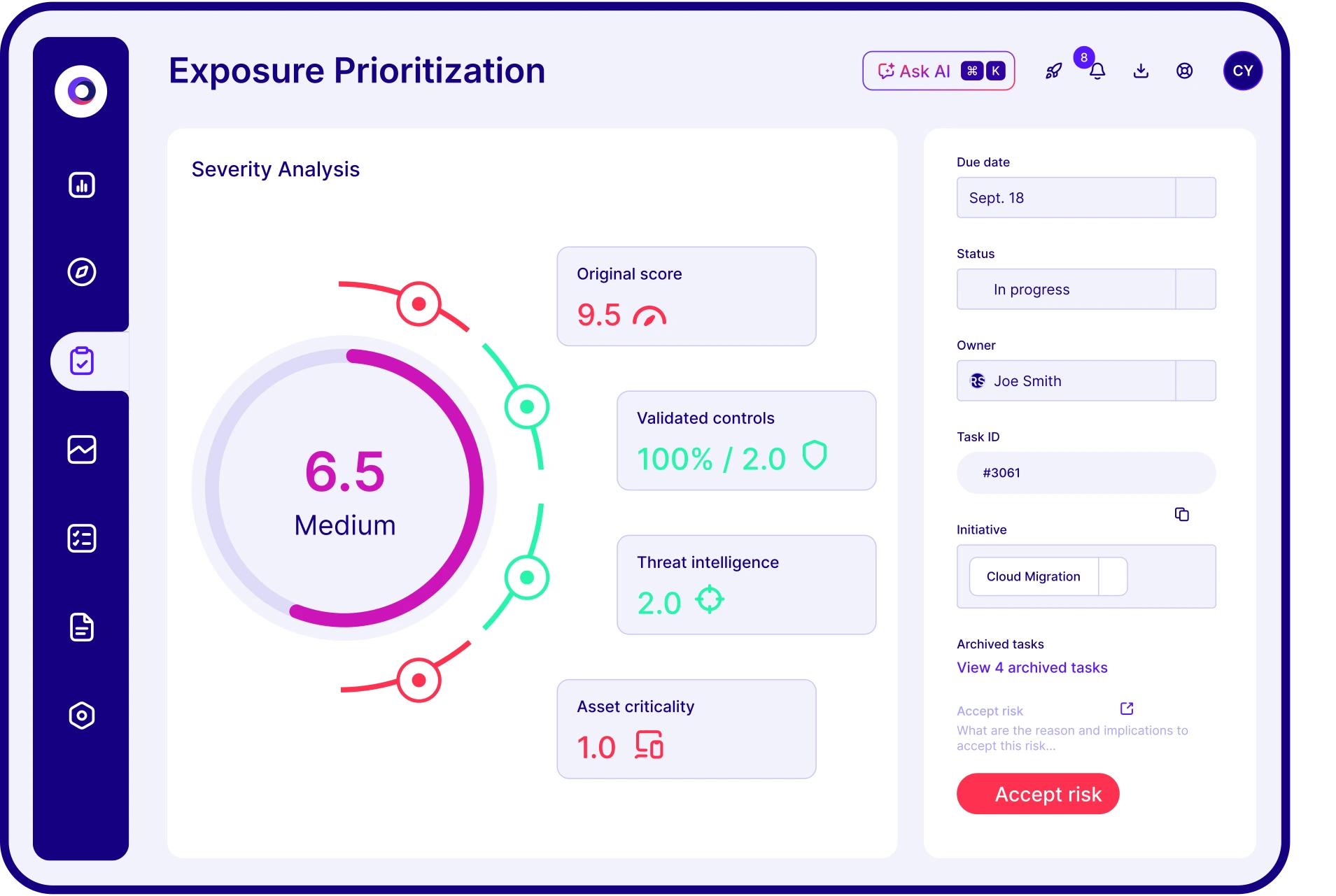
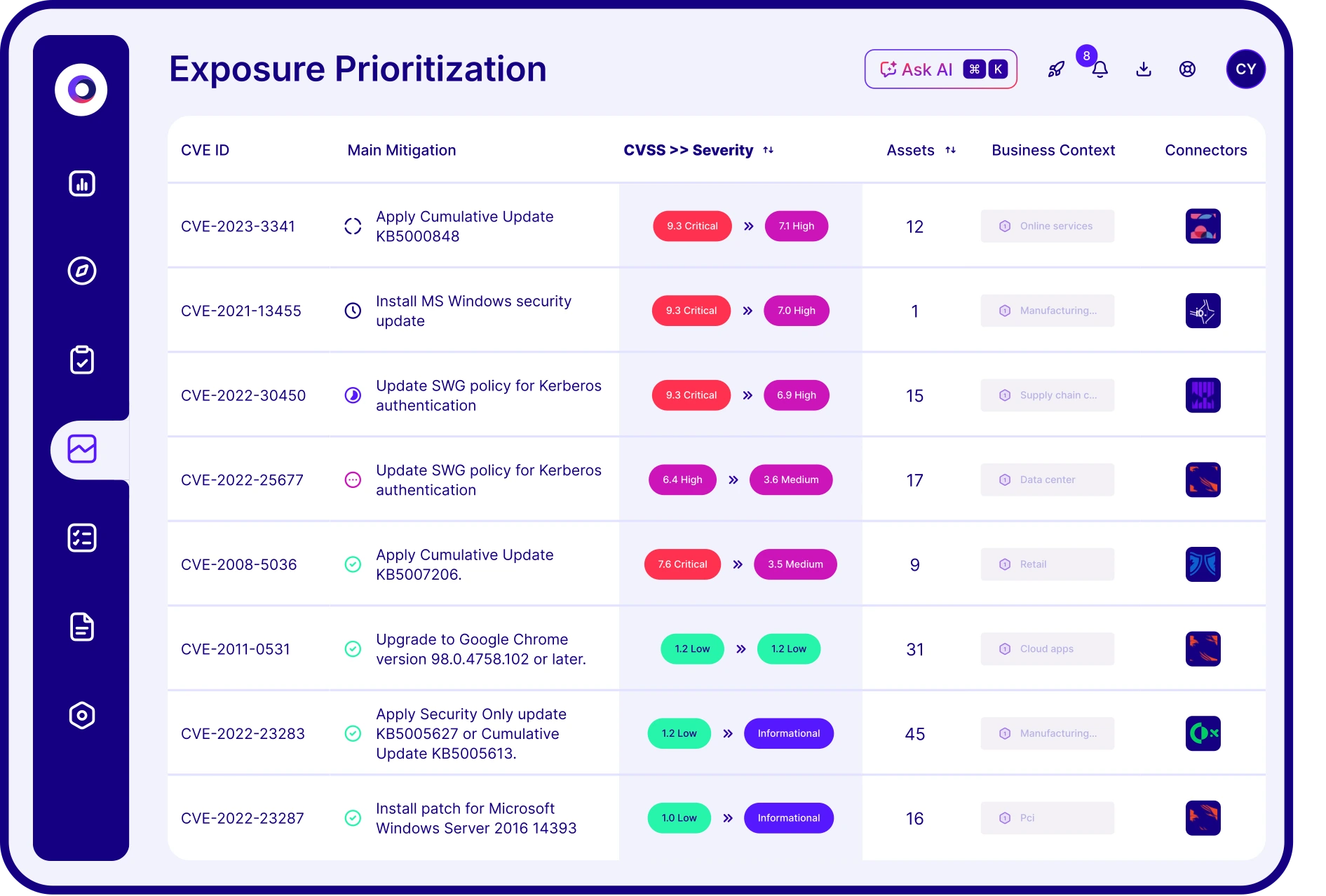
How does Cymulate prioritize exposures?
Cymulate prioritizes exposures by validating their exploitability and ranking them based on prevention and detection capabilities, business context, and threat intelligence. This helps organizations focus on the most critical vulnerabilities and optimize remediation efforts.
Does Cymulate support automated remediation and mitigation?
Yes, Cymulate supports automated mitigation and guided remediation. The platform generates actionable remediation plans based on validated threats, pushes custom detection rules and control updates to security tools, and enables immediate application and verification of remediations. Learn more about automated mitigation.
How does Cymulate use AI and automation in exposure management?
Cymulate leverages AI to simplify threat exposure validation by running intelligent breach and attack simulations that map to threats and detection rules. Automation ensures continuous testing, seamless integration into workflows, and accelerates response to threats through automated control updates and remediation guidance.
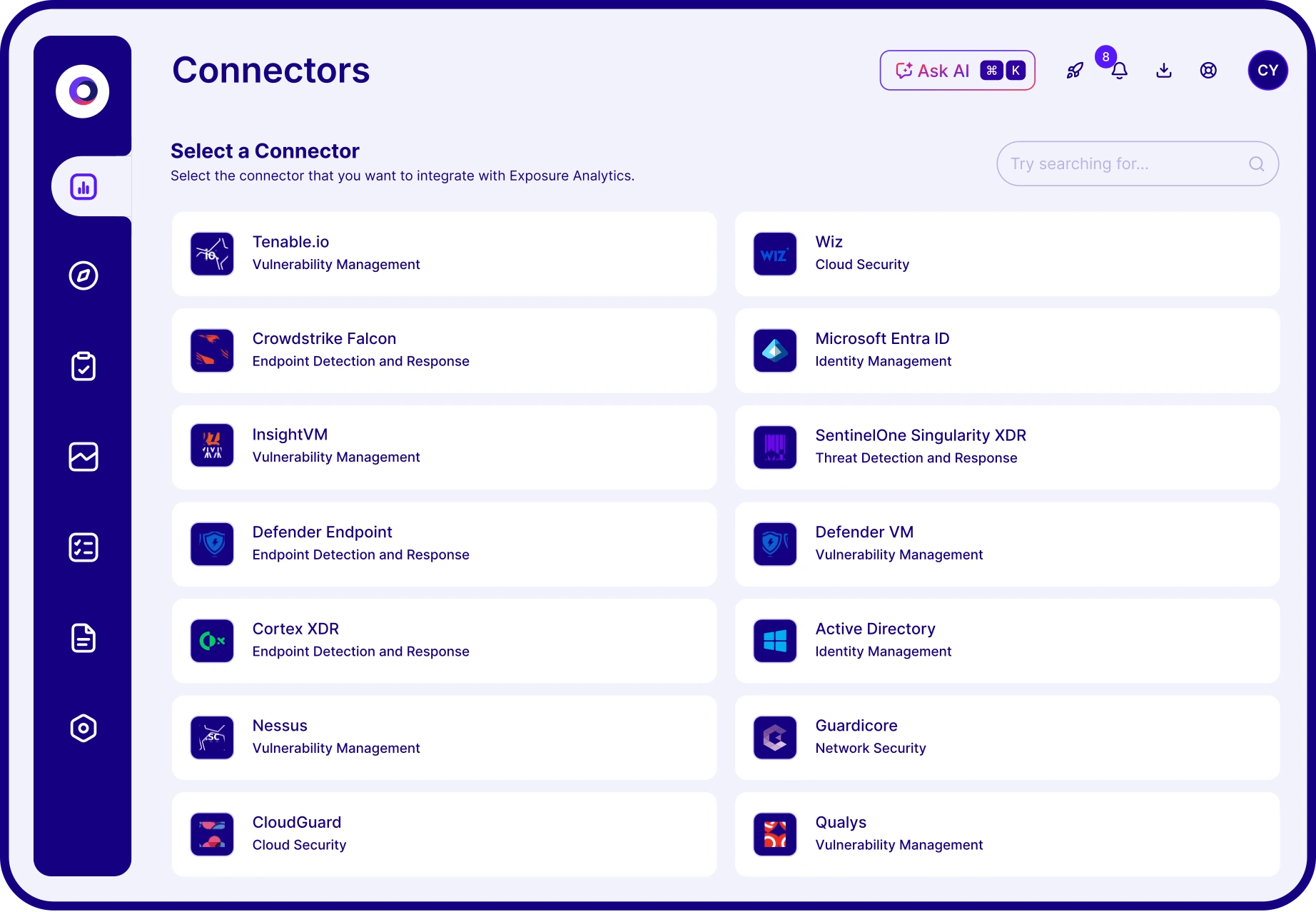
What integrations does Cymulate offer?
Cymulate integrates with a wide range of security technologies, including Akamai Guardicore, AWS GuardDuty, BlackBerry Cylance OPTICS, Carbon Black EDR, Check Point CloudGuard, Cisco Secure Endpoint, CrowdStrike Falcon, Wiz, SentinelOne, and more. For a complete list, visit the Partnerships and Integrations page.
Can Cymulate integrate with our existing security tools?
Yes, Cymulate offers seamless integrations with existing security tools, including vulnerability management solutions, SIEMs, and other security technologies. These integrations allow for automatic import of asset and exposure data, enriched prioritization, and streamlined validation and remediation workflows.
What solution areas does Cymulate cover?
Cymulate covers a wide range of solution areas, including Exposure Validation, Exposure Prioritization and Remediation, Attack Path Discovery, Automated Mitigation, Threat Validation, Detection Engineering, and enabling Continuous Threat Exposure Management (CTEM). Explore all solutions.
How does Cymulate validate exposures?
Cymulate validates exposures by automating offensive security testing, including breach and attack simulation and continuous automated red teaming. This approach provides proof and evidence for exposures, enabling organizations to focus on what is truly exploitable and prioritize remediation effectively.
What is the Cymulate threat library?
The Cymulate threat library is an extensive collection of over 100,000 attack actions aligned to the MITRE ATT&CK framework, updated daily with the latest threat intelligence. This enables organizations to simulate real-world attacks and stay ahead of emerging threats.
Business Impact & Outcomes
What measurable outcomes can customers expect from Cymulate?
Customers can expect up to a 52% reduction in critical exposures, a 30% increase in threat prevention, a 60% increase in team efficiency, and an 81% reduction in cyber risk within four months, as reported by Cymulate customers and case studies. See customer success stories.
How does Cymulate improve operational efficiency?
Cymulate automates processes, leading to a 60% increase in team efficiency and saving up to 60 hours per month in testing new threats. Automation allows security teams to focus on strategic initiatives rather than manual tasks. Learn more.
What business impact does Cymulate deliver?
Cymulate delivers improved security posture, operational efficiency, faster threat validation (40X faster than manual methods), cost savings by consolidating tools, enhanced threat resilience, and better decision-making with actionable insights and quantifiable metrics. See more business outcomes.
Are there real-world case studies demonstrating Cymulate's value?
Yes, Cymulate has numerous case studies, such as Hertz Israel reducing cyber risk by 81% in four months, a sustainable energy company scaling penetration testing, and Nemours Children's Health improving detection in hybrid environments. Explore case studies.
What feedback have customers given about Cymulate's ease of use?
Customers consistently praise Cymulate for its intuitive interface and ease of use. Testimonials highlight the platform's user-friendly dashboard, quick implementation, and accessible support. For example, Raphael Ferreira, Cybersecurity Manager, noted, "Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture." Read more testimonials.
Pain Points & Solutions
What common pain points does Cymulate address?
Cymulate addresses fragmented security tools, resource constraints, unclear risk prioritization, cloud complexity, communication barriers, inadequate threat simulation, operational inefficiencies in vulnerability management, and post-breach recovery challenges. See how customers solved these pains.
How does Cymulate help with fragmented security tools?
Cymulate integrates exposure data and automates validation to provide a unified view of the security posture, closing gaps in visibility and control caused by disconnected tools.
How does Cymulate address resource constraints in security teams?
Cymulate automates manual processes, improves operational efficiency, and enables teams to focus on strategic initiatives, helping organizations do more with limited resources.
How does Cymulate help prioritize risk?
Cymulate validates and ranks exposures based on exploitability, business context, and threat intelligence, enabling teams to focus on the most urgent and critical vulnerabilities.
How does Cymulate support cloud security and hybrid environments?
Cymulate secures hybrid and cloud infrastructures through automated compliance and regulatory testing, increasing visibility and improving detection and response capabilities. See Nemours Children's Health case study.
How does Cymulate help with communication barriers for CISOs?
Cymulate provides quantifiable metrics and insights to justify investments and align security strategies with business objectives, making it easier for CISOs to communicate risk and value to stakeholders. Learn more for CISOs.
Implementation & Support
How long does it take to implement Cymulate?
Cymulate is designed for quick and easy implementation, operating in agentless mode with no need for additional hardware or complex configurations. Customers can start running simulations almost immediately after deployment. Schedule a demo.
What support options are available for Cymulate customers?
Cymulate offers comprehensive support, including email support ([email protected]), real-time chat support, a knowledge base with technical articles and videos, webinars, e-books, and an AI chatbot for instant answers and guidance. See webinars.
How easy is it to start using Cymulate?
Cymulate is easy to implement and use, requiring minimal resources and no dedicated hardware. The platform integrates seamlessly into existing workflows, and customers can begin leveraging its capabilities with just a few clicks.
Security & Compliance
What security and compliance certifications does Cymulate hold?
Cymulate holds SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1 certifications, demonstrating adherence to industry-leading security and privacy standards. See details.
How does Cymulate ensure data security?
Cymulate ensures data security through encryption for data in transit (TLS 1.2+) and at rest (AES-256), secure AWS-hosted data centers, a tested disaster recovery plan, and a strict Secure Development Lifecycle (SDLC) with continuous vulnerability scanning and third-party penetration tests.
Is Cymulate GDPR compliant?
Yes, Cymulate incorporates data protection by design and has a dedicated privacy and security team, including a Data Protection Officer (DPO) and Chief Information Security Officer (CISO), ensuring GDPR compliance. Learn more.
What product security features does Cymulate offer?
Cymulate's platform includes mandatory 2-Factor Authentication (2FA), Role-Based Access Controls (RBAC), IP address restrictions, and TLS encryption for its Help Center, ensuring robust product security.
Pricing & Plans
What is Cymulate's pricing model?
Cymulate operates on a subscription-based pricing model tailored to each organization's requirements. Pricing is determined by the chosen package, number of assets, and scenarios selected for testing and validation. For a detailed quote, schedule a demo.
Competition & Differentiation
How does Cymulate differ from other exposure management solutions?
Cymulate stands out with its unified platform combining BAS, CART, and Exposure Analytics, continuous 24/7 threat validation, AI-powered optimization, complete kill chain coverage, ease of use, and the most advanced threat library with daily updates. It delivers measurable outcomes and is recognized as a market leader by Frost & Sullivan. See Cymulate vs competitors.
What advantages does Cymulate offer for different user segments?
CISOs benefit from quantifiable metrics and strategic alignment; SecOps teams gain automation and efficiency; red teams access advanced offensive testing; and vulnerability management teams get automated validation and prioritization. Learn more by role.
What industry recognition has Cymulate received?
Cymulate has been named a Customers' Choice in the 2025 Gartner Peer Insights, recognized as a market leader for automated security validation by Frost & Sullivan, and is highly rated by security professionals worldwide. See Gartner recognition.
Company & Vision
What is Cymulate's mission and vision?
Cymulate's mission is to transform cybersecurity practices by providing tools for continuous threat validation and exposure management. The vision is to create a collaborative environment where organizations can achieve lasting improvements in their cybersecurity strategies. Learn more about Cymulate.
How does Cymulate ensure ongoing innovation?
Cymulate updates its SaaS platform every two weeks with new features, such as AI-powered SIEM rule mapping and advanced exposure prioritization, ensuring customers always have access to the latest capabilities.