Solutions

Challenge
Launch inbound and outbound web attacks that challenge Secure Web Gateway and Web Proxy efficacy and validate web security and acceptable usage policies.

Assess
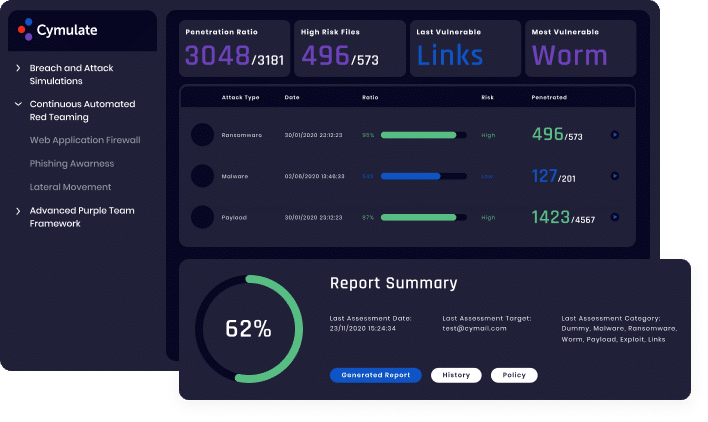
Technical reports identify security gaps and provide information on successful attacks, while executive reports summarize the assessments and provide an aggregate web-security risk score.

Optimize
Prioritize mitigations with standards-based risk scoring and optimize web security with actionable mitigation guidance.
Benefits
Validate the effectiveness of your
web security controls against
threat evolutions and stop attacks
in the pre-exploitation stage.
- Track web security efficacy over time and prevent security drift
- Find, prioritize, and fix security gaps against an exhaustive and continuously updated library of attacks
- Benchmark your web security performance against industry peers
- Safe to run in production
Web Gateway Vector
Furthermore, legitimate websites developed in an unsecure manner are also being compromised and used to spread malware and other attacks.
Cymulate’s Web Gateway vector simulates a myriad of web-based attacks that challenge and assess the efficacy of your web security controls. These controls include cloud and on prem secure web gateways and proxies, content disarm and reconstruction technologies, sandboxing and other types of web-security controls. The Web Gateway vector enables you to measure your organization’s exposure to an extensive and continuously updates database of malicious and compromised websites, malware, and risky files used by threat actors in web-based attacks.
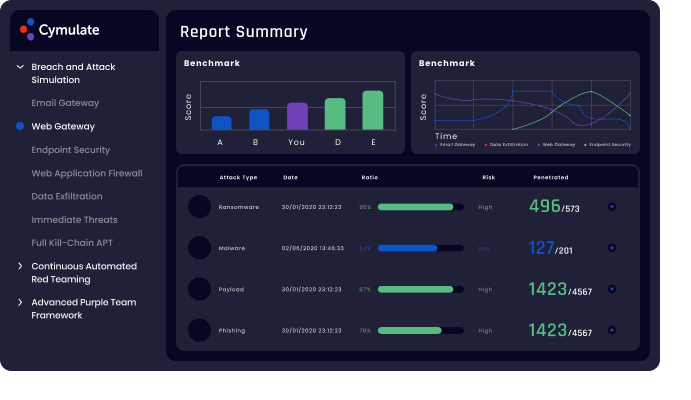
Technical reports provide analysis of the attacks and actionable mitigation guidance that help security teams to shore up their defenses against successful attacks. Standards-based risk scoring enable IT and security teams to identify security gaps, prioritize mitigations and take corrective measures to increase web security control efficacy. Executive reports include trend analysis to identify security drift and industry-peer benchmarking to gain comparative insights.
Common forms of web-based attacks include:
Learn More
More Attack Vectors and Modules

Immediate threats
Validate your defenses against the latest cyber-attacks found in the wild, updated daily.

Full Kill Chain APT
Validate your defenses against APT attack scenarios e.g., Fin8, APT38, Lazarus and custom scenarios.

Web App Firewall
Validate your defenses against web application attacks, including OWASP top ten.

Email Gateway
Validate your defenses against thousands of malicious email constructs, attachments, and links.
Endpoint Security
Validate detection and prevention of endpoint ATT&CK TTPs including ransomware, worms, and more.

Data Exfiltration
Validate that sensitive and critical data cannot be exfiltrated from the organization.

Lateral movement
From an initial foothold propagate within the network to find critical assets.