Automated Mitigation
Build threat resilience and eliminate threat exposure with automated security control updates.
Go Beyond Validation to Mitigate Threat Exposure
Exposure management is more than finding gaps. It’s about building resilience to real threats. Cymulate integrates with security controls to push updates for immediate threat prevention.
Test new threats daily
Simulate the latest threats with the Exposure Validation daily threat feed.
Intergrate with controls
Connect to security controls with APIs integrations.

Push control updates
Update security controls for immediate threat prevention.
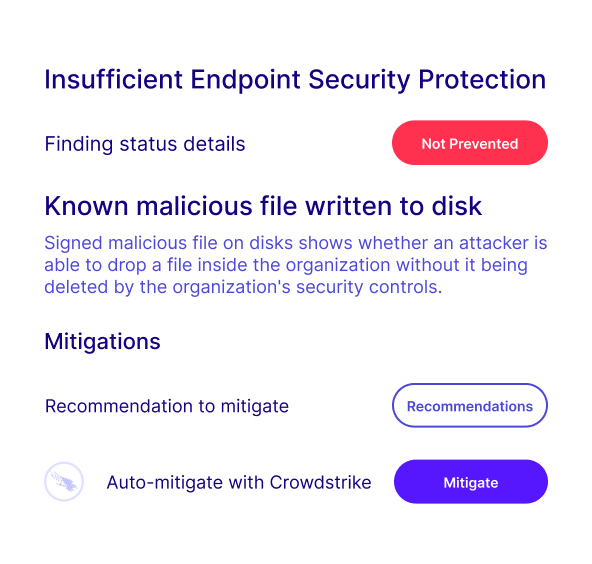
Cymulate Automated Mitigation Benefits
Optimize your threat prevention and detection with efficiency, scale and speed. Build threat resilience and mitigate threat exposure with automation that eliminates the manual processes of updating security controls for identified security gaps.
Mitigate faster
Optimize prevention
Operationalize CTEM
Reduce dwell time
Results & Outcomes
30%
Better Threat
Prevention
CYMULATE CUSTOMER AVERAGE
40x
Faster Threat
Validation
CYMULATE CUSTOMER AVERAGE
70%
Fewer Pen Test
Findings
IT SOLUTIONS CUSTOMER
Integrate with Security Controls to Harden Defenses
As Cymulate validates exposures and identifies security gaps, automated mitigation deploys targeted threat updates to security controls for immediate prevention based on indicators of compromise (IoCs), such as file hashes, registry keys and URLs directly to connected security controls.
Test like an attacker.
Schedule a call with one of our experts.
What our customers say about us
Organizations across all industries choose Cymulate for award-winning breach and attack simulations to validate their security controls.
Automated Mitigation FAQs
Automated mitigation is the process of directly updating security controls based on the results validation and testing from Cymulate Exposure Validation. This enhanced cyber resilience by providing immediate threat prevention for the threats that successfully bypassed controls.
CTEM requires the coordination of multiple teams, so automation plays a key role to reduce friction, accelerate action and free up resources to address more complex needs. The result of automation is faster mitigation of specific threats and greater threat resilience.
When Cymulate validates that an indicator of compromise (IoC) bypasses security controls, Cymulate makes the IoC available for users to push threat updates directly to the control via API integrations.
Without automated mitigation, Cymulate users can manually copy content or download files and feeds that can be directly applied to security controls.