Exploitable Vulnerabilities: Prioritize What Poses Real Risk
Not all cybersecurity vulnerabilities are created equal.
While Common Vulnerability Scoring System (CVSS) scores are useful indicators of severity, they often lack critical context: exploitability within your environment. Chasing every “critical” CVE can waste valuable time and resources, especially when many are not exploitable in practice.
This is where a shift toward risk-based vulnerability management, powered by continuous security validation, becomes essential. By focusing on exploitable vulnerabilities, security teams can cut through the noise and address what truly matters.
We’ll explore how and why prioritizing exploitable threats — rather than theoretical ones — can drastically improve your organization’s security posture.
What Makes a Vulnerability Exploitable?
There is a defined scale to what makes a vulnerability truly exploitable. A vulnerability becomes exploitable when there is a viable path for an attacker to leverage it in your environment. This typically requires:
- Publicly available exploit code
- Favorable conditions like weak configurations or elevated privileges
- Reachability (e.g., exposed endpoints, lateral access, etc.)
The CVSS scoring system, widely used for assessing vulnerability severity, fails to account for many of these contextual nuances. A “Critical” CVE may be irrelevant if a web application firewall (WAF) blocks it or the asset is isolated. Conversely, a “Medium” vulnerability can be weaponized when chained with others or paired with misconfigurations, something CVSS won’t catch.
The Limitations of Traditional Vulnerability Management
Most organizations still rely heavily on monthly or quarterly vulnerability scans tied to CVE databases. This approach has several shortcomings, including:
- Lack of environmental context: Traditional scans don’t evaluate whether a vulnerability is actually exploitable.
- False positives: Teams are often flooded with alerts that pose no real-world risk.
- Slow and reactive cycles: Monthly scanning can’t keep up with rapidly evolving threats or agile environments.
- Overwhelming volume: With thousands of new CVEs published annually, deciding what to patch becomes a guessing game.
This leads to inefficient use of remediation resources and leaves real threats exposed.
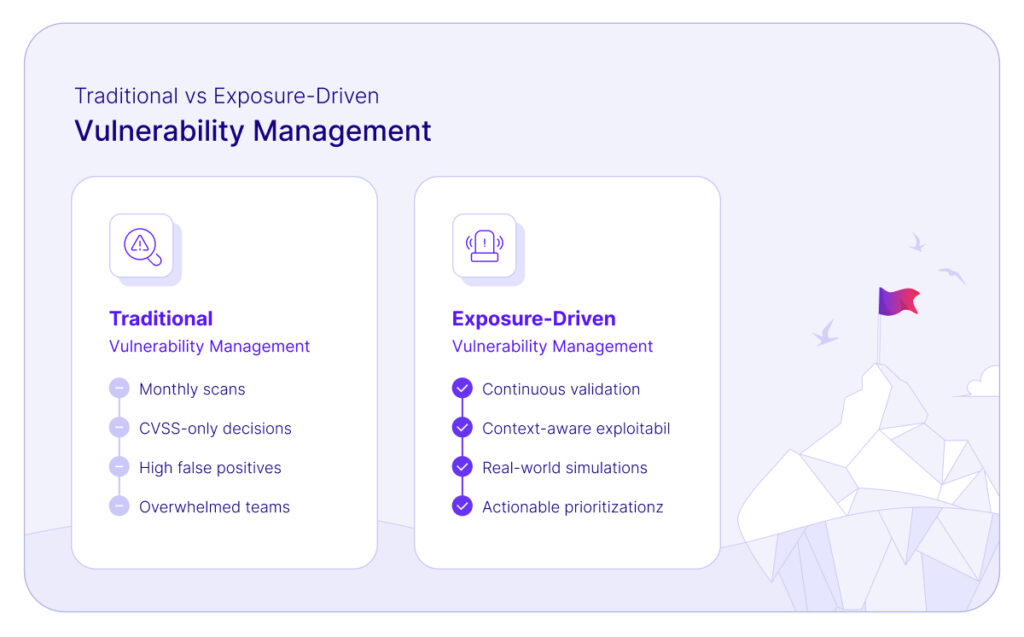
Why Continuous Security Validation is a Game-Changer
Continuous security validation changes the game by testing vulnerabilities in your live environment, under realistic conditions. Instead of assuming a threat is exploitable based on a static score, this approach answers a more important question:
"Can this vulnerability actually be exploited here and now?"
By simulating attacker behavior (such as lateral movement, privilege escalation, and post-exploitation activities) validation reveals:
- Which CVEs are truly exploitable
- How attackers could pivot using combined weaknesses
- What compensating controls are effectively reducing risk
This empowers remediation teams with actionable insights, not theoretical risks.
Prioritizing What Matters: Real-World Scenarios
Let’s walk through a few realistic examples that demonstrate how security validation helps prioritize what truly matters.
1. Volume vs. Risk
A security team scans their environment and uncovers 300 vulnerabilities. Continuous validation via Cymulate reveals only 15 are exploitable based on real attack simulations. That’s a 95% reduction in remediation workload—without increasing risk exposure.
2. Critical ≠ Exploitable
A “critical” CVE in a web server component raises alarms. However, validation confirms that existing WAF rules and network segmentation prevent exploit paths. The team defers patching, saving time and avoiding unnecessary disruption.
3. Chained Exploits Elevate Risk
A seemingly low-risk, medium CVE is discovered in a legacy application. Validation reveals that, when chained with two other low-severity issues, attackers can escalate privileges and access sensitive systems. The vulnerability is immediately prioritized for remediation.
These examples reflect the power of context-aware, exposure-driven prioritization, moving beyond static scores toward operationally relevant risk reduction.
Cymulate’s Role in Exposure-Driven Vulnerability Prioritization
The Cymulate platform is purpose-built to validate exposures and guide risk-based remediation efforts. Instead of relying solely on CVSS, Cymulate continuously tests whether vulnerabilities can be exploited in the context of your specific environment.
Key capabilities include:
- Integration with existing scanners and SIEMs: Import vulnerability data and prioritize based on real exploitability.
- Continuous threat exposure validation: Simulate full attack paths, from initial access to lateral movement.
- Contextual risk insights: Understand which controls are mitigating threats and where gaps remain.
By aligning vulnerability data with real-world attack behavior, Cymulate transforms traditional vulnerability management into a proactive, threat-informed process.
Learn how Cymulate validates exposures and read the Threat Exposure Validation Impact Report 2025.
Best Practices for Focusing on Exploitable Vulnerabilities
Ready to move beyond “patch everything” toward smart, risk-aligned remediation? Start with these best practices:
1. Validate Early and Often
Adopt continuous or weekly validation cycles, especially after major deployments, patching events, or configuration changes.
2. Combine Threat Intel with Validation
Leverage up-to-date threat intelligence alongside exploit testing to understand the current tactics threat actors are using—and how they align with your weaknesses.
3. Prioritize Based on Business Impact
Focus on known exploitable vulnerabilities that impact critical systems, data, or compliance mandates.
4. Automate Where Possible
Integrate validation platforms like Cymulate with your security stack to streamline prioritization and remediation workflows.
Focus on What’s Real
Vulnerability severity scores are a starting point. But exploitability is what truly matters. The reality is clear: teams can’t patch everything, and chasing every high CVSS score wastes time, money and focus.
By embracing continuous security validation, organizations can focus on the vulnerabilities that represent real risk. This means:
- Reducing alert fatigue
- Improving patch efficiency
- Strengthening overall resilience
It’s time to shift from patch-all to validate-then-patch.
Request a demo of Cymulate Exposure Validation to see how your team can start prioritizing what’s actually exploitable today.

