MITRE ATT&CK v18: New Detection Strategies and Analytics Redefine Cyber Defense

Amanda Kegley, Product Marketing Manager
Yoni Harris, Senior Product Manager
The latest release of the MITRE ATT&CK Framework v18.0 marks a significant change in how the cybersecurity community conceptualizes and documents detections. Effective Oct. 28, 2025, all MITRE ATT&CK framework detections are now updated for each technique and sub-technique by removing traditional Detections (Data Sources) and replacing with Detection Strategies and Analytics. Data Sources have been fully retired.
This transitions static detections to structured Detection Strategies and Analytics marking a major evolution in how ATT&CK aligns with real-world adversary behaviors. Not only is visibility enhanced across tactics, but also cross-tactic correlations are strengthened. This is especially the case between Execution and Persistence, where overlapping telemetry often challenges SOC teams in maintaining detection precision.
Key highlights
- MITRE ATT&CK Framework v18 transforms detections: The latest update replaces traditional Detections (Data Sources) with Detection Strategies and Analytics, creating a behavior-driven model that strengthens visibility and cross-tactic correlation.
- Analytics makes detections actionable: By linking analytics to telemetry, defenders can now understand how and where adversarial behaviors appear, bridging the gap between intelligence and operational defense.
- Data Components redefined for precision: The new structure enhances the connection between telemetry and adversary techniques, enabling more granular detection engineering aligned with real-world threat behaviors.
- Cymulate operationalizes MITRE v18: Fully mapped to MITRE ATT@CK, Cymulate continuously validates detections and auto-generates vendor-specific SIGMA and EDR rules, turning MITRE’s Detection Strategies into measurable, tested detection resilience.
- New Techniques: 12 new techniques have been added to the MITRE ATT&CK v18 Framework.
What’s new in the MITRE ATT&CK v18 Framework
From extensive feedback, the user community has just received a long-awaited change to the MITRE ATT&CK framework. The detection model that has been in place for 10 years has been re-hauled to add realistic layers for behavior-based detection strategies and analytics vs. just data sources. This allows organizations to better align detections with real-world adversary behavior, improving detection accuracy and operational defense effectiveness.
Detection strategies and analytics replace detections
With MITRE’s revamped detection model, the detection mapping for each technique has been updated. Since the introduction of the ATT&CK framework in 2015, each technique detection has been mapped to one or more Data Sources and Data Components. With this new change, each technique detection maps to one or more Detection Strategies and Analytics, as shown below.
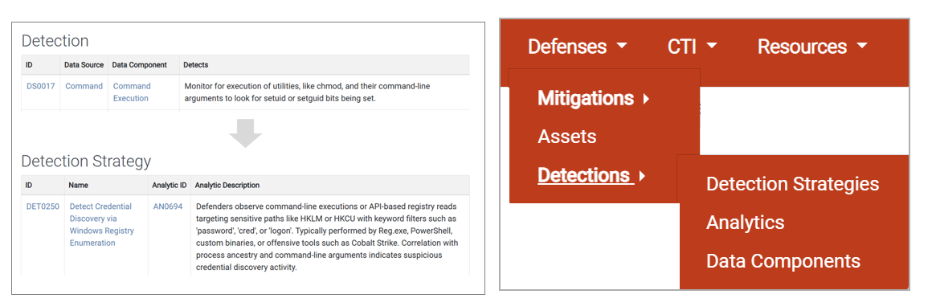
New detection model mapping
The new detection model mapping includes:
- Structured fields such as detection name, description, detection analytics and relevant data sources
- Mappings to data components that highlight where detection telemetry originates (e.g., process creation, registry access, file modification)
- Behavior-driven focus, improving how detection teams align monitoring capabilities to real-world threats
Impact: Defenders can now identify not just what to detect, but how and where adversarial behaviors manifest within telemetry.
Data components redefined
Data Components, the foundation of the MITRE ATT&CK detection layer, now provides clearer links between telemetry and Detection Strategies. This overhaul supports more granular mapping between data sources (e.g., endpoint logs, process monitoring) and adversary techniques.
Introducing analytics for Detections
The introduction of analytics effectively operationalizes the MITRE ATT&CK framework, shifting it from descriptive to actionable. By linking analytics to telemetry-driven detections, defenders can now design detection logic that mirrors adversarial TTPs. This aligns strongly with Cymulate continuous validation approach, ensuring that analytics not only exist in theory but are validated against real, emulated attack behaviors.
Why MITRE ATT&CK v18 changes matter
These updates transform the MITRE ATT&CK framework into a behaviorally-grounded defense model. By shifting to Detection Strategies and Analytics, defenders gain clarity on:
- How adversaries move laterally through systems and networks
- What telemetry sources reveal those movements
- How to align SOC detection engineering with adversary tradecraft
In essence, MITRE is moving away from describing detections to defining how detections can be achieved, bridging the gap between intelligence and operational defense.
Example of new ATT&CK detection model for techniques
The table below describes the new detection model for each technique and sub-technique across all ATT&CK tactics.
| MITRE Detection Layer | ATT&CK Framework v18 Example |
| Technique/Sub-technique | T15502.02 – Credentials in Registry (Tactic: Credential Access) |
| Detection Strategy | DET0250 – Detect registry queries for stored credentials |
| Analytic | AN0694 - Behavioral detection of registry queries by suspicious processes |
| Data Components | DC0032 – Process Creation (Event log) DC0063 – Windows Registry Key Modification (Event log) DC0050 – Windows Registry Key Access (EDR rule) |
New detection model for techniques
Cymulate Platform and integration with MITRE ATT&CK
The Cymulate platform continues to stay aligned to the evolving MITRE ATT&CK framework. The platform has over 90,000 attack simulation tests to validate your configured security controls. Each attack test is integrated and mapped to the MITRE ATT&CK framework for the corresponding technique and sub-techniques, mitigations and detections.
Cymulate accelerates detection engineering for organizations by automatically generating vendor-specific detection rules, which includes EDR and SIGMA-based detections rules for missed attack tests. The platform also provides the MITRE ATT&CK recommended mitigations.
This integration perfectly embodies the intent behind MITRE v18’s Detection Strategies. As Data Components are now more granular, Cymulate simulates techniques like T1552.002 – Credentials in Registry and auto-generate SIGMA rules, which provides tangible validation layers. It ensures that detection engineering keeps pace with ATT&CK’s evolving taxonomy, turning framework alignment into measurable detection resilience. Cymulate is fully aligned with this ATT&CK framework shift and continuously running attack simulations validates that the right detections are in place.
Cymulate in Action: Example MITRE ATT&CK technique simulation
For the example technique, T1552.002 - Credentials in Registry, the Cymulate platform has numerous attack tests that attempt to query registries for stored credentials to validate if the EDR is properly configured to capture this malicious activity, specifically to confirm the presence of the EDR:hunting log source (as illustrated above).
Below is one of the example attack tests Cymulate has in its library for this specific technique.
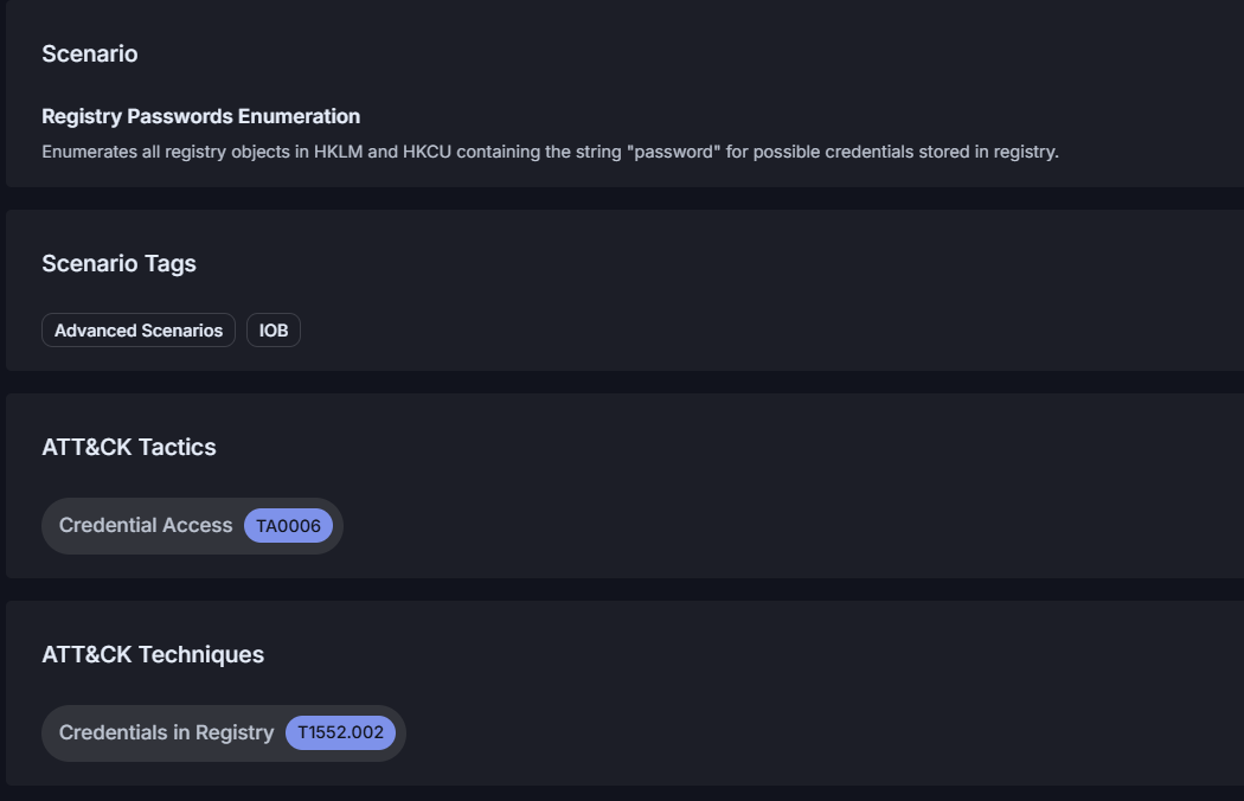
Scenario description and mapping to MITRE ATT&CK technique T1552.002
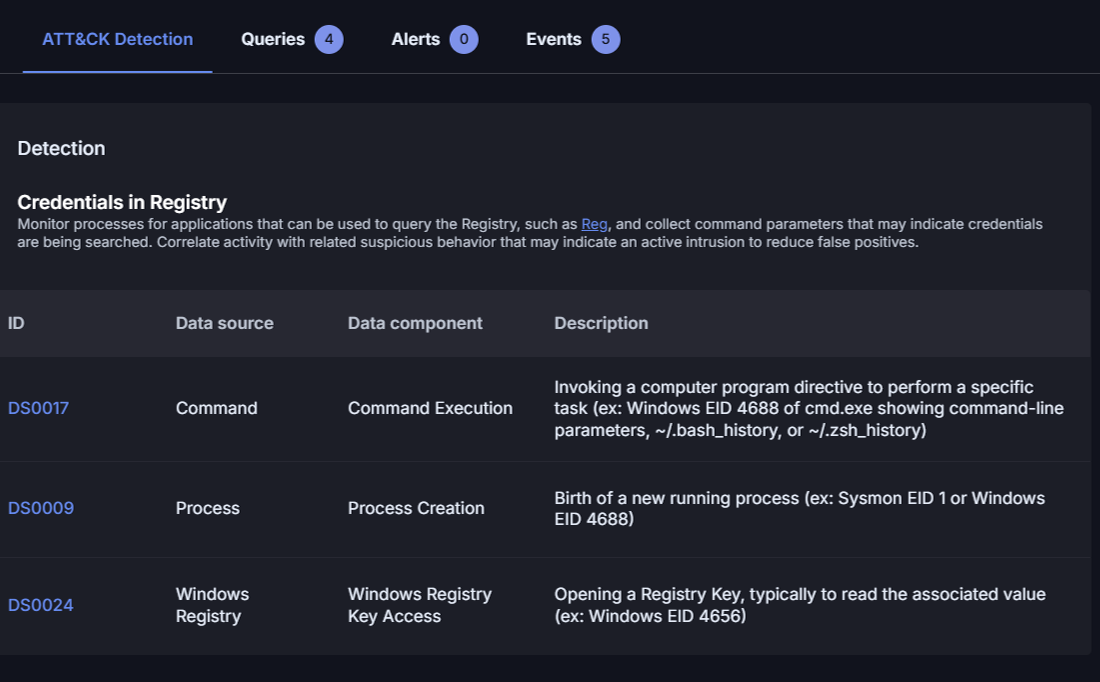
General mapping to MITRE ATT&CK detections (current model v17.1)
The picture above depicts the traditional detection mapping model currently in the Cymulate platform. Cymulate will be updating the detections for each attack tests with the new model.
Once attack scenarios have been run, Cymulate delivers a status of detected or not detected. Cymulate automatically depicts the mitigations, which include detection rules that can be customized for your specific vendor security technology.
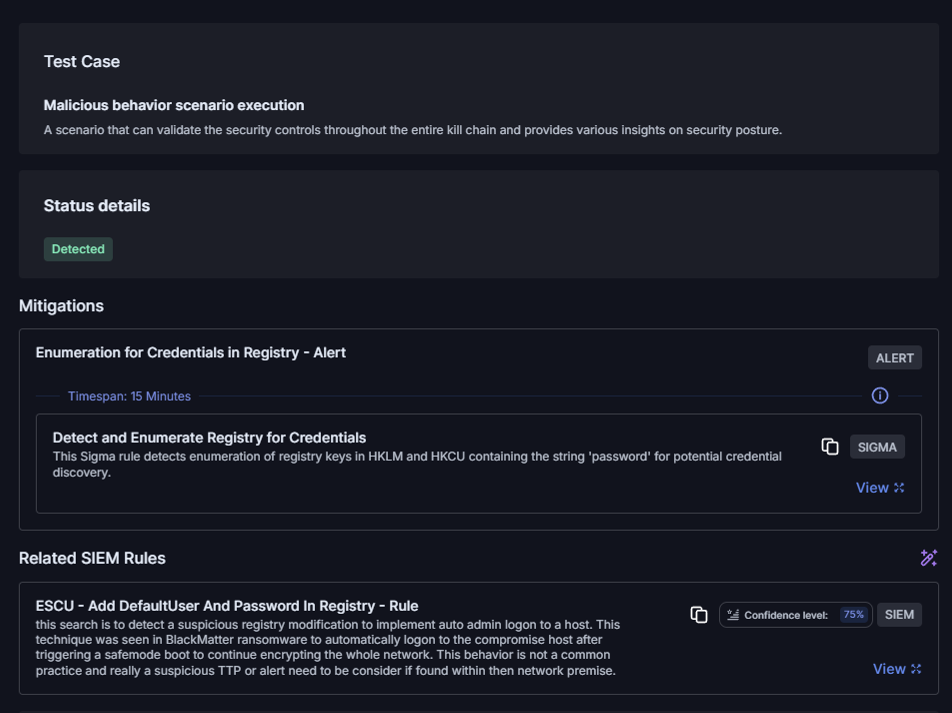
Attack test simulation result & available auto-generated rules
For this specific rule, Cymulate automatically generated this SIGMA rule to specifically detect this activity.
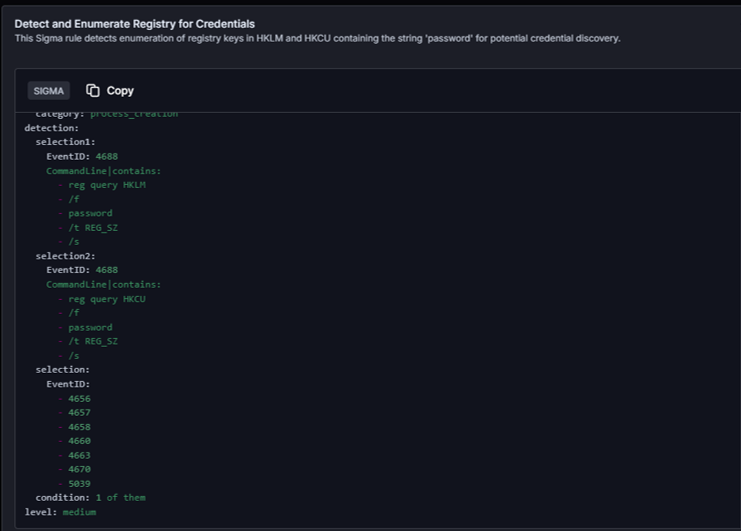
Detection rule with event code including 4656 and 4657 aligned to MITRE ATT&CK log sources.
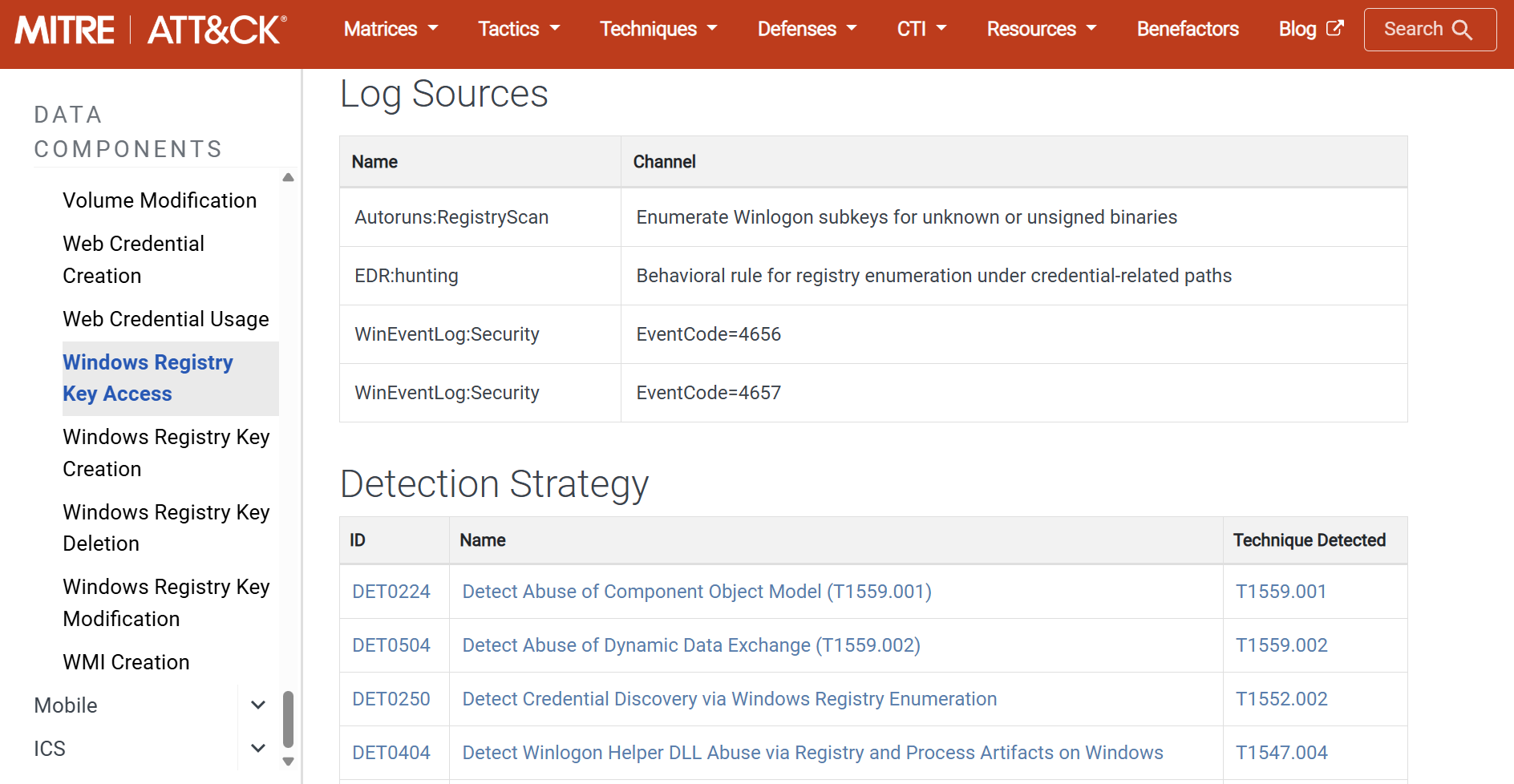
Log source for data component
Ensuring security controls are continually detecting this malicious activity improves overall threat resilience to prevent and/or minimize security breaches.
What’s next for MITRE ATT&CK Framework
MITRE is already preparing for the next evolution of ATT&CK, as described in their recent blog post. The organization has indicated another milestone change by splitting the “Defense Evasion” tactic into two new tactics:
- Stealth
- Impair Defenses
While this change is still in development, it reflects MITRE’s ongoing effort to capture adversary intent with greater precision. In addition, it plans on moving existing techniques to the appropriate tactic that did not quite fit into Defense Evasion, such as T1548 - Abuse Control Mechanism (move to Privileged Escalation) and T1578.005 - Modify Cloud Compute Configurations (move to Persistence).
Moving into 2026, MITRE’s roadmap includes:
- Updating detections to match the detection strategies model.
- Expanding cyber threat intelligence (CTI) content, including new software, groups and cross-domain campaigns.
- Broadening asset coverage into more sectors and system types.
- Refining and recategorizing techniques
- Introducing additional sub-techniques.
- Launching the ATT&CK Advisory Council, a new body for structured community feedback on framework evolution and strategic direction.
Operationalizing MITRE ATT&CK v18 with Cymulate
As MITRE ATT&CK continues to evolve, Cymulate is actively updating our platform to ensure that our attack simulation, detection engineering and mitigation mapping are fully aligned with MITRE ATT&CK v18 and beyond.
Our commitment is clear. Cymulate customers will benefit from industry-standard mitigation and detection mapping, behaviorally aligned analytics and comprehensive coverage of ATT&CK techniques. By keeping pace with MITRE’s evolution, Cymulate empowers organizations to transform framework awareness into operational threat resilience.
Want to see Cymulate in action to learn about the platform and how it’s aligned to the MITRE ATT&CK framework? Sign up for a demo and see what the platform can do for you.