Cymulate Aligns Platform to MITRE ATT&CK v18

Cymulate continues to stay ahead of the curve by aligning our platform with the latest developments in the MITRE ATT&CK® framework. With the release of MITRE ATT&CK® v18 , we’ve expanded our attack scenario library and reporting capabilities to reflect the newest techniques and sub-techniques introduced by MITRE.
This update to Cymulate Exposure Validation ensures our customers can maintain comprehensive threat coverage, validate their defenses and fine-tune security controls against the latest adversarial behaviors—all while measuring their threat readiness against the one of the most widely adopted frameworks.
Key highlights
As part of the product updates and alignment to MITRE ATT&CK, Cymulate Exposure Validation now includes:
- An expanded attack scenario library with the new techniques and sub-techniques in MITRE ATT&CK v18
- Visibility into v18-specific adversarial behaviors and how customers can easily run relevant attacks to validate their security posture and maintain threat resilience
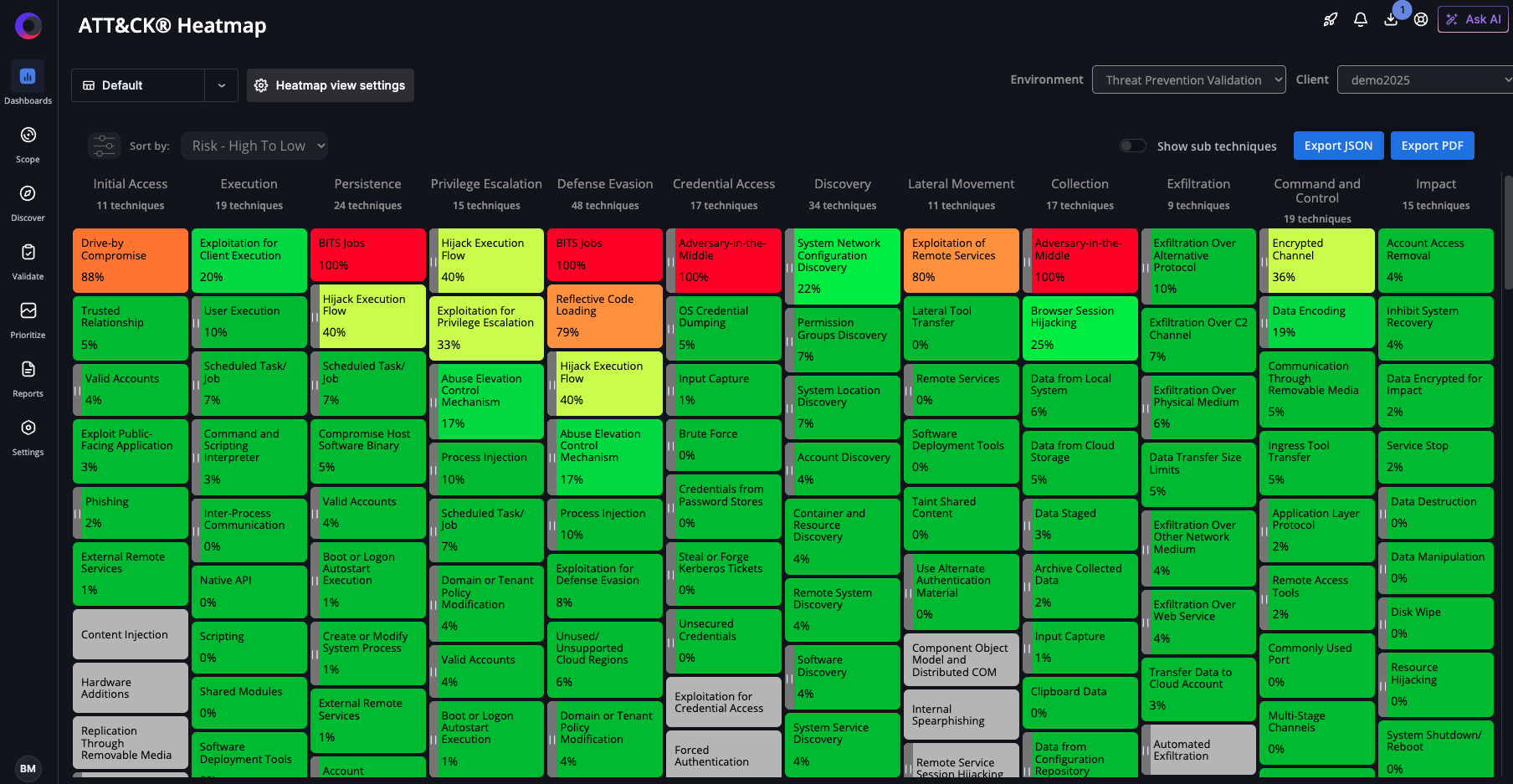
- An updated heatmap of validated detection and prevention validation
What’s new from Cymulate Exposure Validation?
MITRE ATT&CK version 18 introduces 12 new techniques that reflect evolving adversary behaviors across enterprise and cloud environments. Cymulate has expanded its attack simulation library with eight new attack scenarios and updates to three others that align to nine of the 12 new techniques.
The new Cymulate new attack scenarios cover the following new MITRE ATT&CK techniques:
| Technique ID | Technique Name | New Attack Scenario Name | Description |
|---|---|---|---|
| T1059.013 (Execution) | Command and Scripting Interpreter: Container CLI/API | Kubernetes - Mass Get Command Execution | Simulates an adversary executing multiple get and list commands to gather information on all resources within a namespace in containerized environments. |
| T1546.018 (Persistence) | Event Triggered Execution: Python Startup Hooks | Python Startup Hooks Backdoor | Tests the ability to detect an attacker exploiting Python’s startup hooks to create a backdoor by writing a .pth file in the directory. |
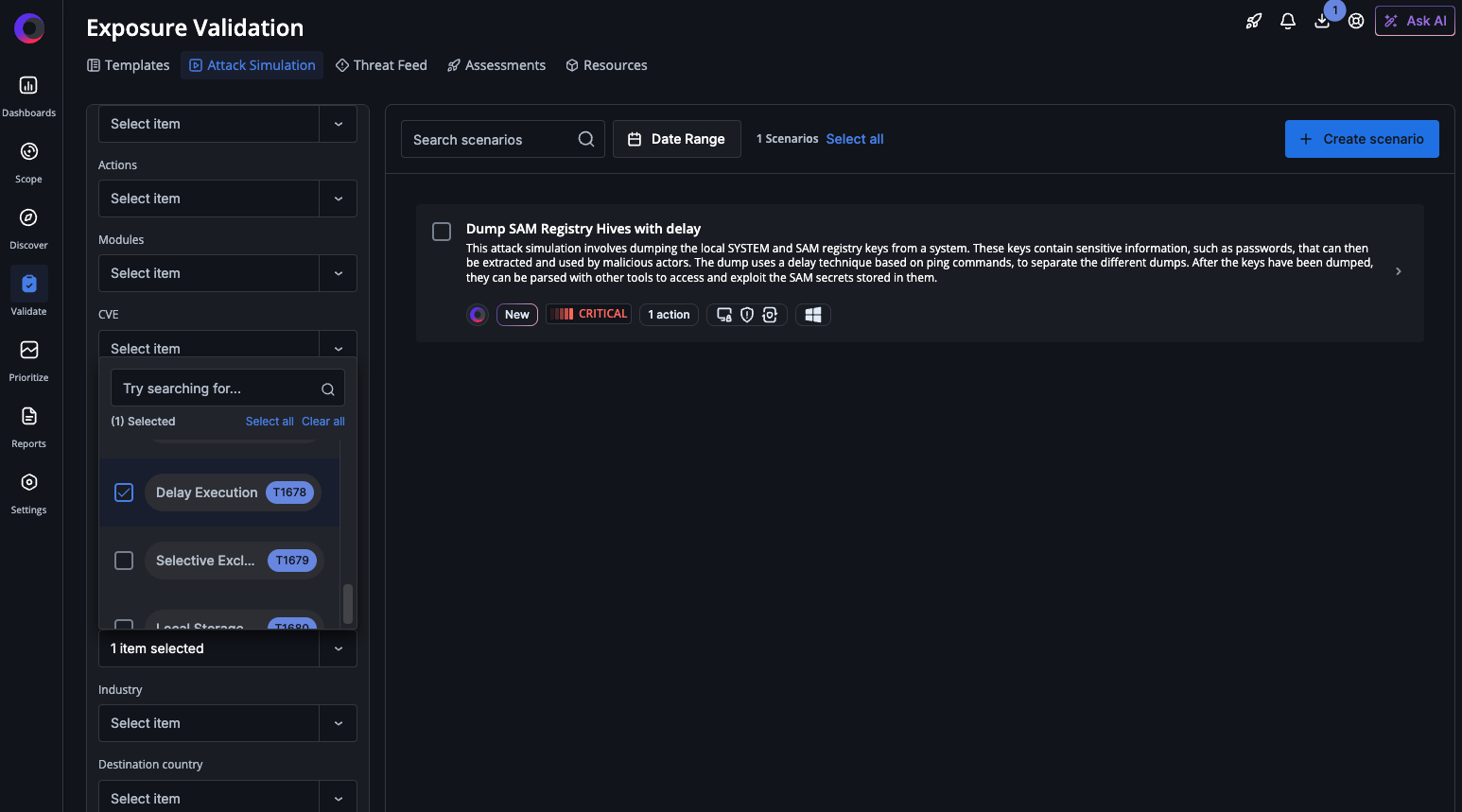
| T1678 (Defense Evasion) | Delay Execution | Dump SAM Registry Hives with Delay | Simulates an attacker employing a delay technique based on ping commands to avoid detection, specifically dumping the local SYSTEM and SAM registry keys from a system. |
| T1036.012 (Defense Evasion) | Masquerading: Browser Fingerprint | Downloader: Curl Browser Fingerprint Masquerading | Simulates an attacker attempting to blend in with legitimate traffic by using a legitimate browser User agent to download a single file from a specified URL to a predetermined location using curl. |
| T1679 (Defense Evasion) | Selective Exclusion | Selective Exclusion Ransomware Simulation | Simulates an attacker using malicious payloads to intentionally evade detection by a creating a folder with various dummy files and encrypting them while excluding certain file types such as .dll and .exe. |
| T1680 (Discovery) | Local Storage Discovery | Local Storage Discovery | Simulates attackers enumerating local drives, disks and/or volumes and their attributes, such as total or free space and volume serial number. |
| T1518.002 (Discovery) | Software Discovery: Backup Software Discover | Backup Software Discovery | Simulates malware or adversaries scanning Windows systems to identify backup solutions like Veeam or Acronis, gathering intelligence for potential data destruction, encryption or recovery prevention attacks. |
| T1213.006 (Collection) | Data from Information Repositories: Databases | ODBC SQL database query | Connect to the target SQL database via ODBC using given credentials and run a custom SQL query. |
Three existing attack scenarios have been updated to simulate T1562.013 Impair Defenses: Disable or Modify Network Device Firewall with scenarios specific to cloud platforms.
| Technique ID | Technique Name | Updated Attack Scenario Name | Description |
|---|---|---|---|
| T1562.013 (Defense Evasion) | Impair Defenses: Disable or Modify Network Device Firewall | Azure - Add Rule to Azure Network Security Group | Simulates an attacker modifying Azure network security group rules to expand access, enabling unauthorized entry, data breaches or lateral movement. Monitoring and controlling NSG changes is vital for prevention. |
| AWS - Security Group Updated to Allow Ingress for Any IP to Any Port | Simulates creation of an AWS Security Group allowing all IPs full access, exposing resources to internet threats, enabling potential unauthorized access, data breaches and exploitation of cloud vulnerabilities. | ||
| GCP - Firewall Rule Set To Ingress From Any IP And Specific Ports | Simulates an attacker creating a GCP firewall rule allowing global ingress traffic, exposing services to unauthorized access, exploitation and data breaches by bypassing restrictions on remote desktop or database access. |
These new attack scenarios in Cymulate Exposure Validation are available via the “attack scenario workbench” to run as individual assessments or included in new or existing assessment templates.
Why these MITRE ATT&CK v18 updates matter for security teams
Running the newly released scenarios from MITRE ATT&CK v18 ensures organizations remain proactive in addressing evolving threats. These scenarios enable security teams to:
- Validate coverage against the latest adversarial tactics
- Identify and close security control gaps across endpoints, identities and cloud workloads
- Strengthen detection and response capabilities based on real-world attack simulations
By continuously validating against new techniques, Cymulate helps organizations identify gaps and build resilience—while measuring validated prevention and detection in the MITRE ATT&CK heatmap.
Unsupported MITRE ATT@CK v18 techniques
Of the 12 new techniques in v18, Cymulate does not automate validation for three of them due to environmental or ethical constraints.
| Technique ID | Technique Name | Reason for Unsupported Simulation |
| T1677 (Execution) | Poisoned Pipeline Execution | Requires simulation of offensive behavior specifically on application build servers. |
| T1681 (Reconnaissance) | Search Threat Vendor Data | A Reconnaissance technique before Initial Access, which is external to an organization and cannot be reproduced or prevented and detected. |
| T1204.005 (Execution) | User Execution: Malicious Library | Not recommended as it will most likely be flagged as malicious and removed and unable to run again |
What’s next in the Cymulate platform?
Cymulate is planning future enhancements to further align to the major change in detections. Our roadmap includes:
- Revamping the detection validation engine to align with MITRE’s updated detection taxonomy
- Innovating in detection engineering to map detections to analytics and response mechanisms
- Expanding correlation capabilities between simulation results and SOC detection analytics
These innovations will empower customers to transition from validation to continuous detection engineering, providing a deeper understanding of detection effectiveness and resilience.
Experience Cymulate Exposure Validation firsthand
We encourage Cymulate users to explore the new MITRE ATT&CK v18 scenarios today. Run the new simulations, review your results and work with your Customer Success Manager for guidance on optimizing your defenses or troubleshooting any issues.
If you are not a customer, schedule a demo to see how you can validate your threat resilience against MITRE ATT&CK with Cymulate Exposure Validation.