Solutions

Challenge
Deploy attack techniques, tools and methods used to gain access, elevate privileges, and spread across systems, following the initial compromise of a single endpoint.

Assess
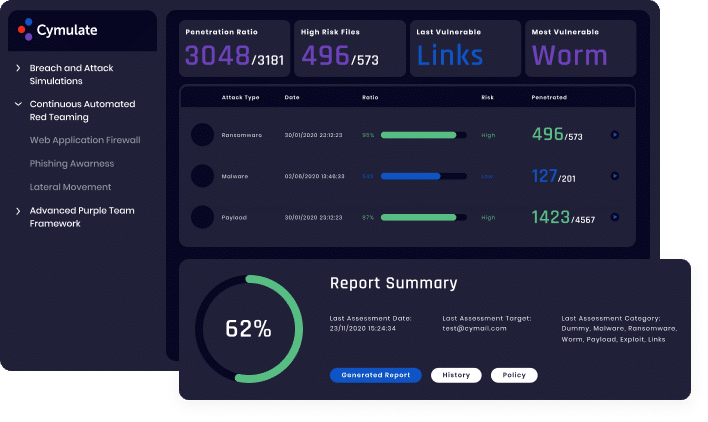
See how far an attacker can propagate within the network, which attack and spreading techniques were used at every hop, and shares, credentials and other assets that were discovered or used.

Optimize
Resilience to lateral movement, segmentation enforcement, fix infrastructure misconfigurations and improve IT hygiene.
Benefits
Visualize and mitigate attack paths from initial foothold to enterprise crown jewels
- Gain visibility on critical assets and vulnerable machines at risk from an adversary landing in the network
- Prevent security drift – continuously validate IT hygiene and use of best practices
- Mitigate attack techniques and tools and infrastructure misconfigurations manipulated by attackers
- Improve ineffective segmentation policies and enforcement
- Production safe
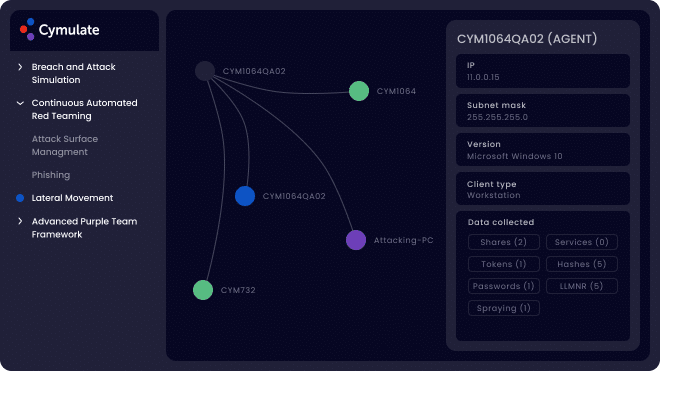
Lateral Movement
Starting from a single compromised endpoint, this validation module challenges your internal networks by applying a variety of real techniques and methods used by attackers to gain access and control additional systems on a network. Once an organization’s perimeter defenses fail and endpoint security is bypassed, providing the attacker a foothold in the organization (see Endpoint Security Vector) lateral movement inside the network is a common next step in a breach or ransomware scenario.
Cymulate’s Lateral Movement vector simulates a compromised workstation inside the organization and exposes the risk posed by a potential cyberattack or threat. Real techniques and methods are used to laterally move inside the network. Vulnerabilities and vulnerable machines are correlated to Vulnerability Scanner findings through out-of-the-box integrations. Vulnerabilities are not exploited in order to remain production safe.
Learn More
More Attack Vectors and Modules

Immediate threats
Validate your defenses against the latest cyber-attacks found in the wild, updated daily.

Full Kill Chain APT
Validate your defenses against APT attack scenarios e.g., Fin8, APT38, Lazarus and custom scenarios.

Web App Firewall
Validate your defenses against web application attacks, including OWASP top ten.
Endpoint Security
Validate detection and prevention of endpoint ATT&CK TTPs including ransomware, worms, and more.

Data Exfiltration
Validate that sensitive and critical data cannot be exfiltrated from the organization.

Web Gateway
Validate your defenses against malicious inbound and outbound web browsing and command and control.

Email Gateway
Validate your defenses against thousands of malicious email constructs, attachments, and links.