Network Security Validation
Simulate external and internal network traffic to validate and
optimize security controls.
Threat actors use sophisticated tactics and techniques to intercept and exploit network traffic.
Organizations encountered C2
traffic in their network
Source: Akamai
Overall web traffic originates
from botnets
Source: Akamai
All network traffic
is malicious
Source: Cloudflare
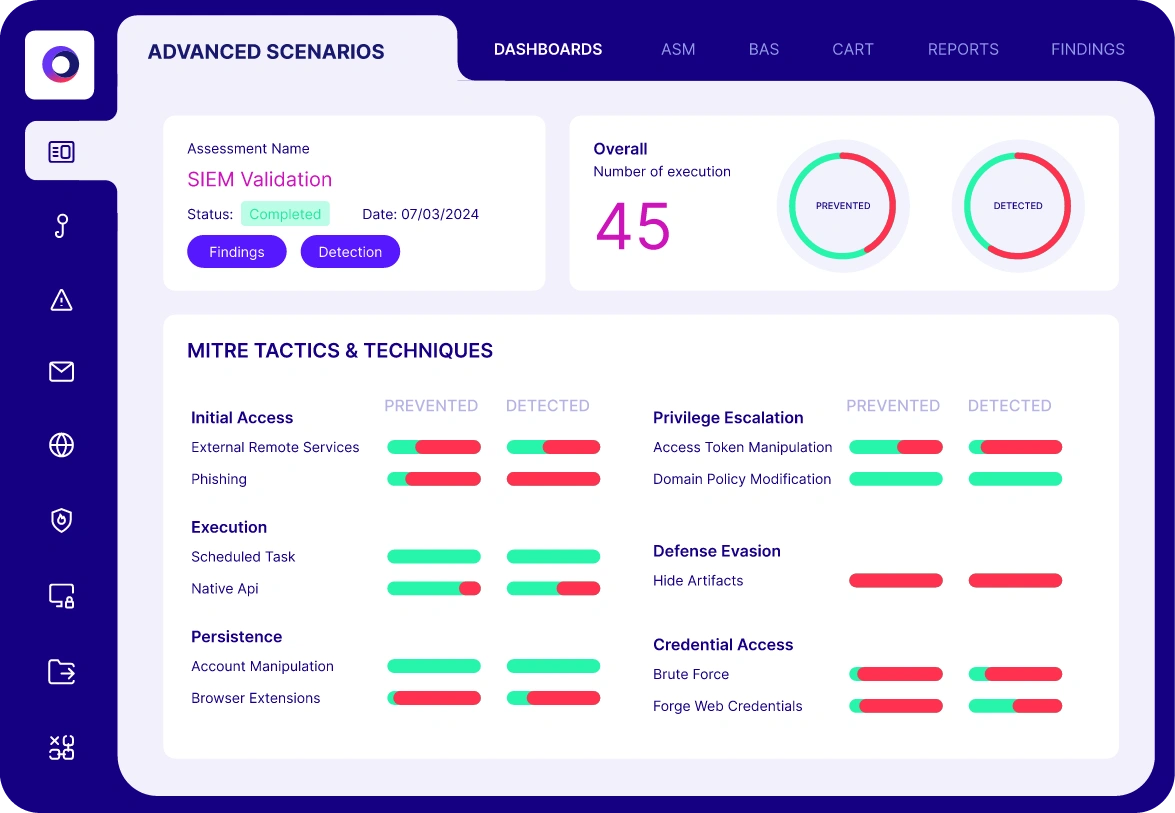
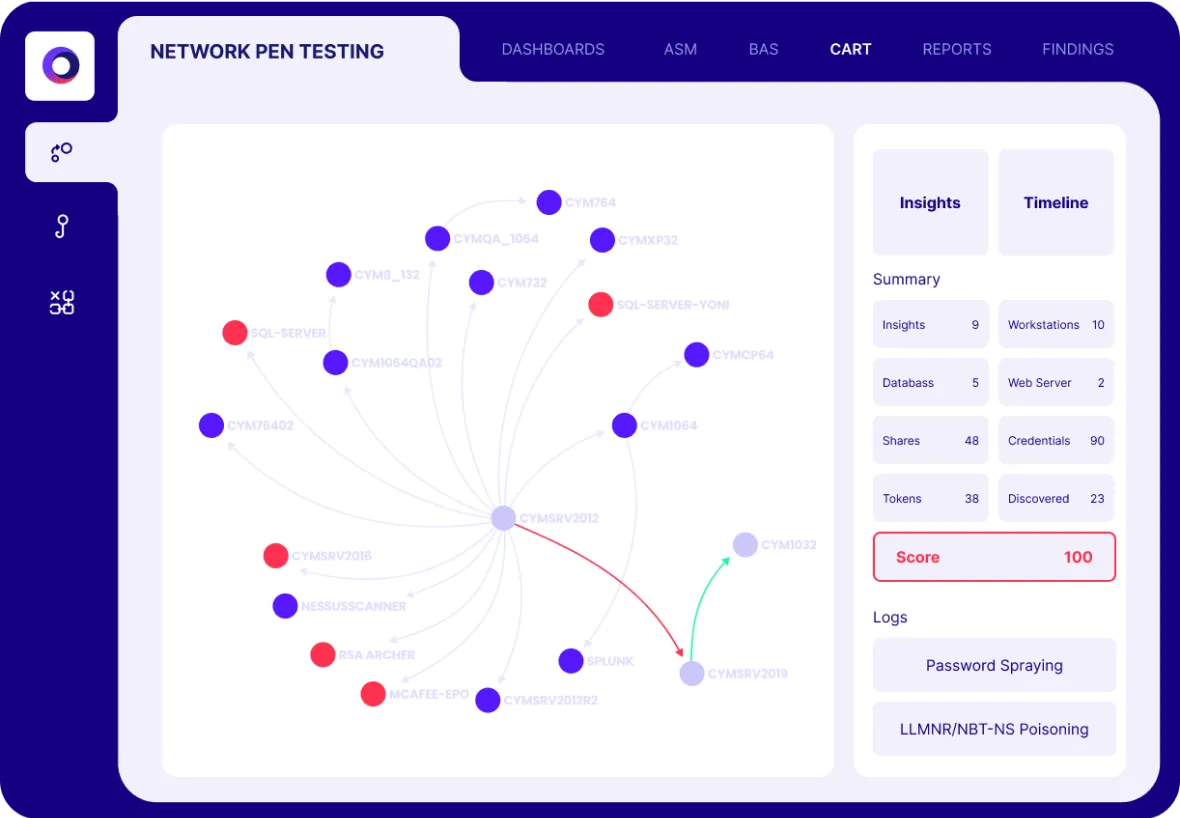
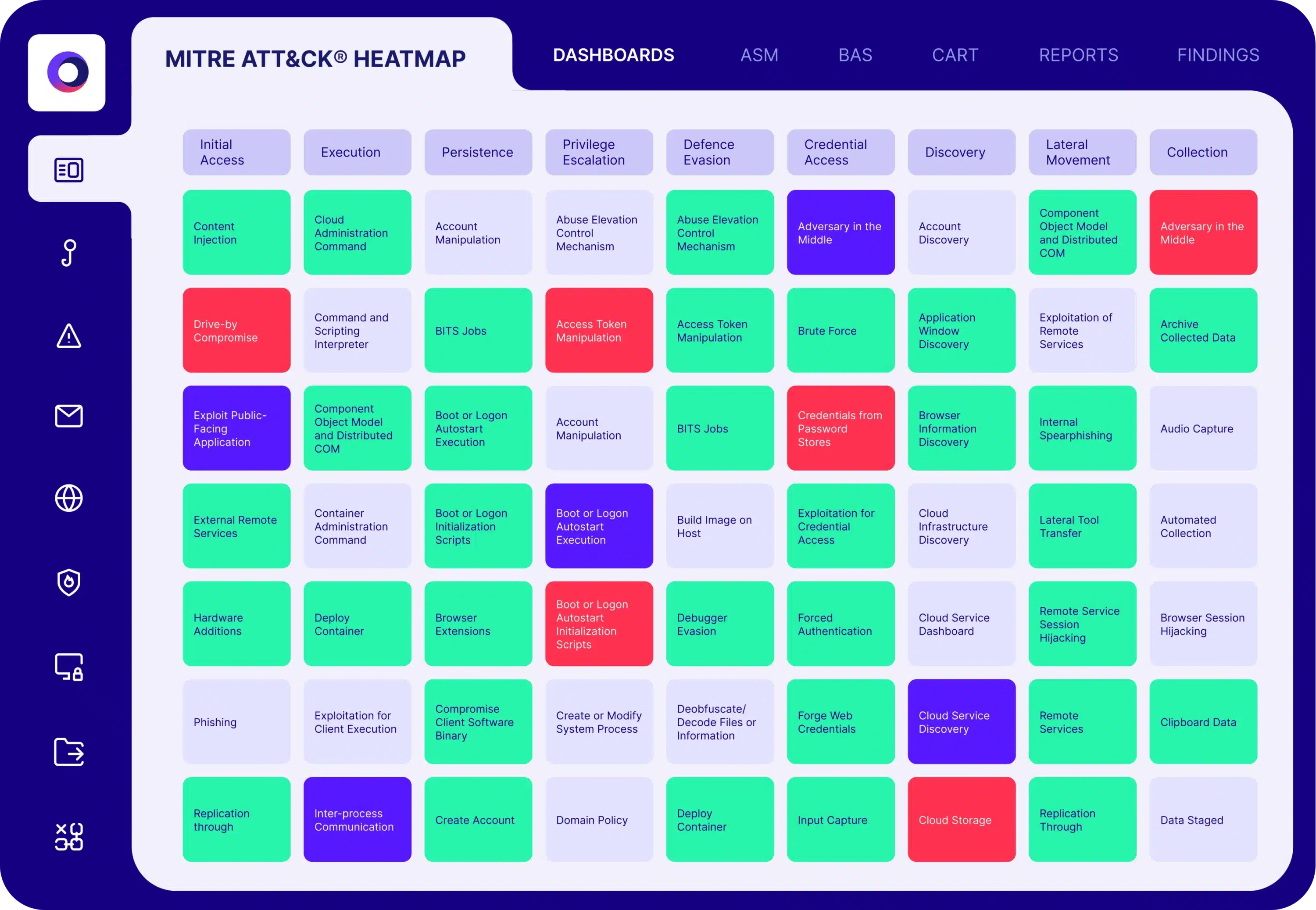
Automated Security Validation for
Network Security
Cymulate delivers automated security validation to simulate malicious network traffic for both north–south traffic into and out of the network and east–west internal traffic across the network. Network security validation assessments enable you to test the effectiveness of security controls and policies associated with your:
- Web gateways and firewalls
- Intrusion prevention / detection systems
- Network segmentation
- Lateral movement
- Data loss prevention
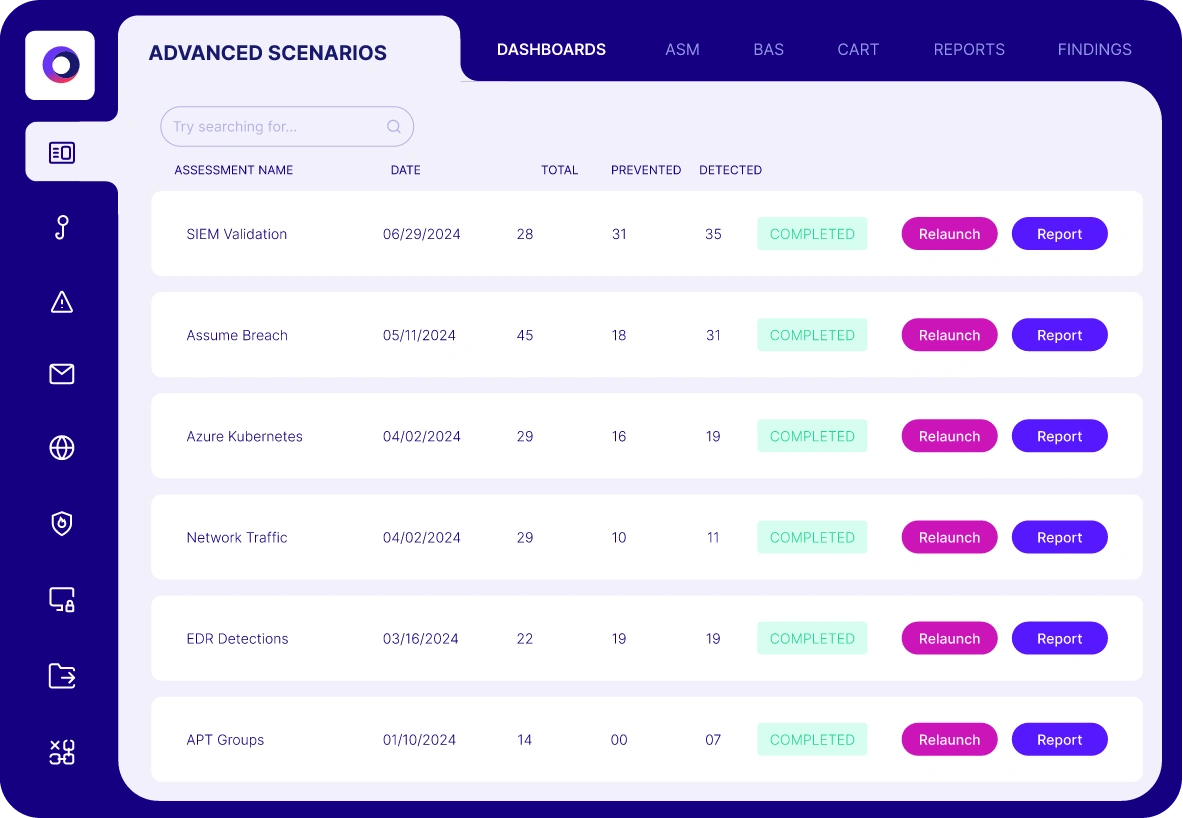
Solution Results
91%
Improvement in malicious file detection post mitigation
50%
Improvement in the prevention of known exploit techniques
168
Exploits prevented from a single policy change
Solution Benefits
Automated security validation
Identify gaps and weaknesses
Optimize security controls
Reduce exposure risk
What our customers say about us
Organizations across all industries choose Cymulate for automated cybersecurity validation, proactively confirming that defenses are robust and reliable-before an attack occurs.