Cymulate for Vulnerability
Management Teams
Cut through the noise to prioritize validated exposure
and improve threat resilience.
Vulnerability management teams are drowning in patches and exploits.
Vulnerabilities
patched each
month
Source: Bitsite
of breaches involve
unpatched
vulnerabilities
Source: Gartner
Have automated threat
exposure management
Source: Gartner
Modernize Vulnerability Management with CTEM
Traditional vulnerability management isn’t enough. True resilience requires moving beyond scanning and patching to Continuous Threat Exposure Management (CTEM). Legacy tools claim visibility but can’t answer the critical question: Can your defenses withstand real-world threats?
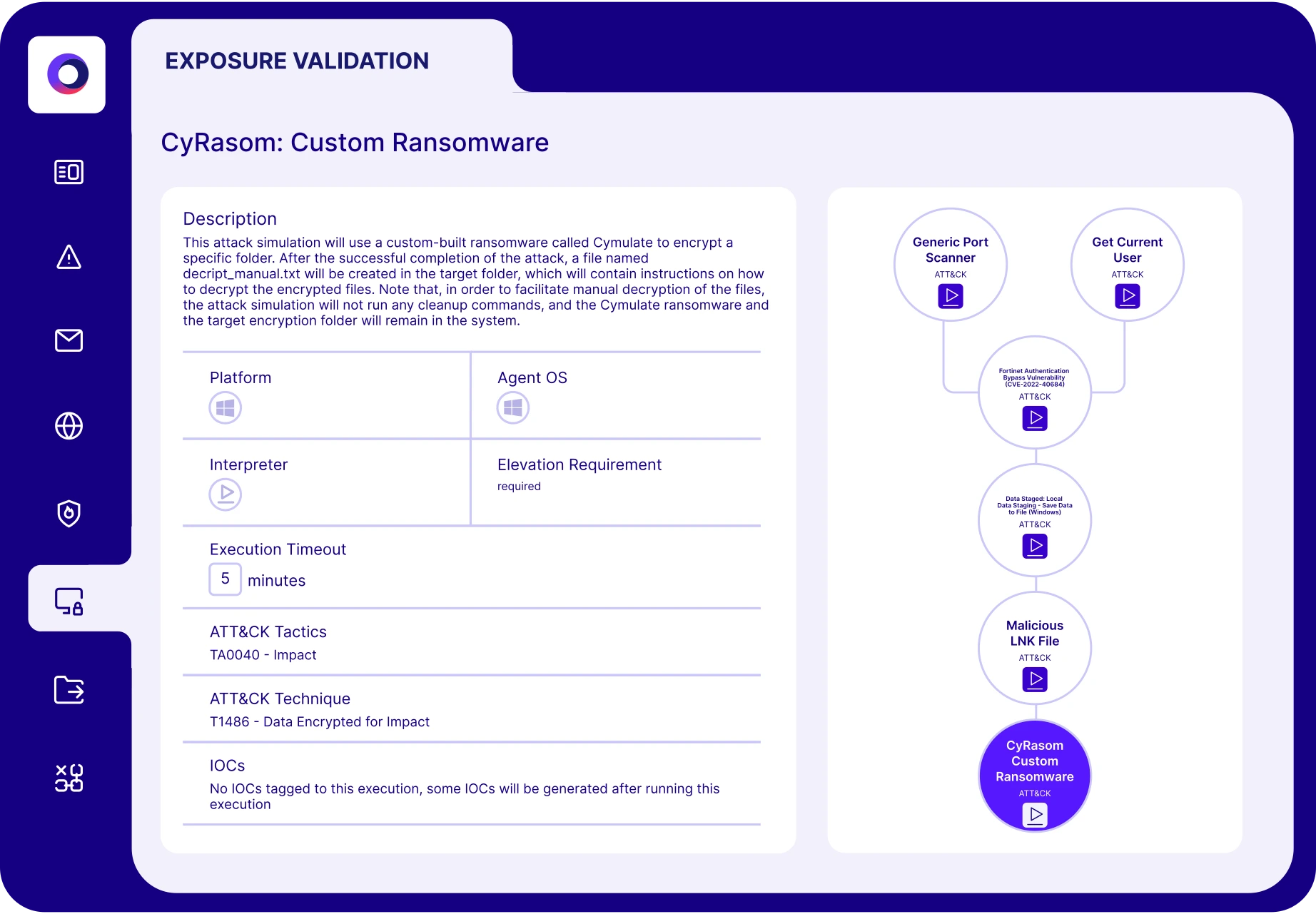
Cymulate closes that gap. With automated exposure validation and integrated discovery, Cymulate prioritizes risks based on what’s truly exploitable—validated through real offensive testing.
Focus on the exploitable
Streamline security workflows
Prioritize actionable remediation
Measure and improve threat resilience
Vulnerability Management Results
52%
Reduction in critical exposures
AVG. of CYMULATE CUSTOMERS
70%
Fewer vulnerabilities
in next pen test
IT organization
60%
Increase in team
efficiency
healthcare company
What our customers say about us
Organizations across all industries choose Cymulate for exposure management, evolving their vulnerability management programs to proactively and continuously validate threat resilience.
Test like an attacker.
Schedule a call with one of our experts.
Vulnerability Management FAQs
Traditional VM focuses on identifying and ranking vulnerabilities but often lacks context and validation. CTEM expands this by continuously identifying, testing and validating exposures across your environment—enabling you to focus mitigation on what truly poses a risk. It shifts from a patch-all mindset to one rooted in real-world exploitability and business impact.
The critical missing component is threat validation. Cymulate goes beyond static CVEs by automatically testing whether exposures can be exploited in your environment. It validates how your security controls respond to those threats—bridging the gap between detection and real-world risk.
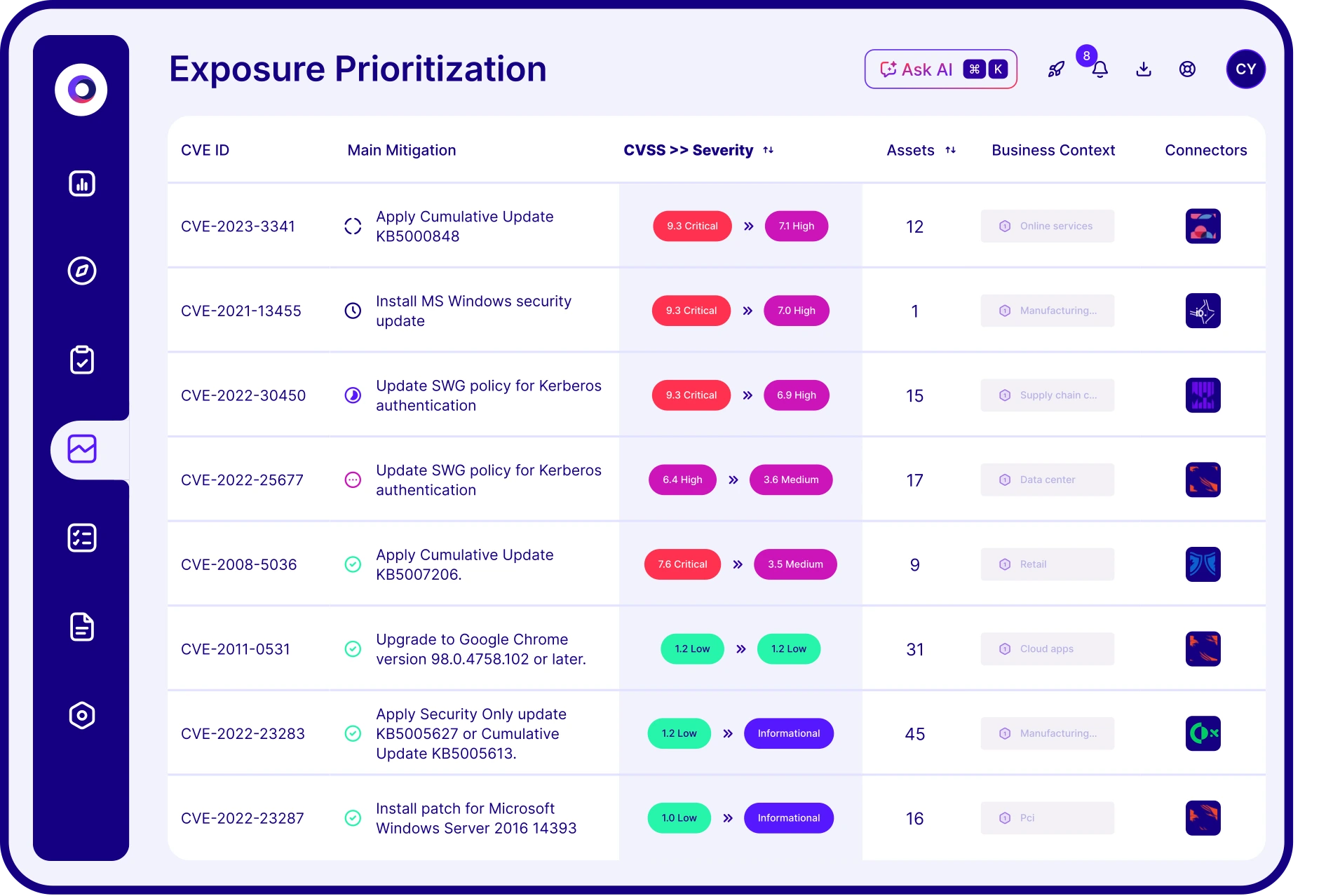
Cymulate contextualizes exposures by aggregating:
- Vulnerability data from scanners
- Asset context including business criticality
- Threat intelligence to understand attacker likelihood
- Automated threat validation to prove exploitability
- Security control effectiveness (prevention/detection outcomes)
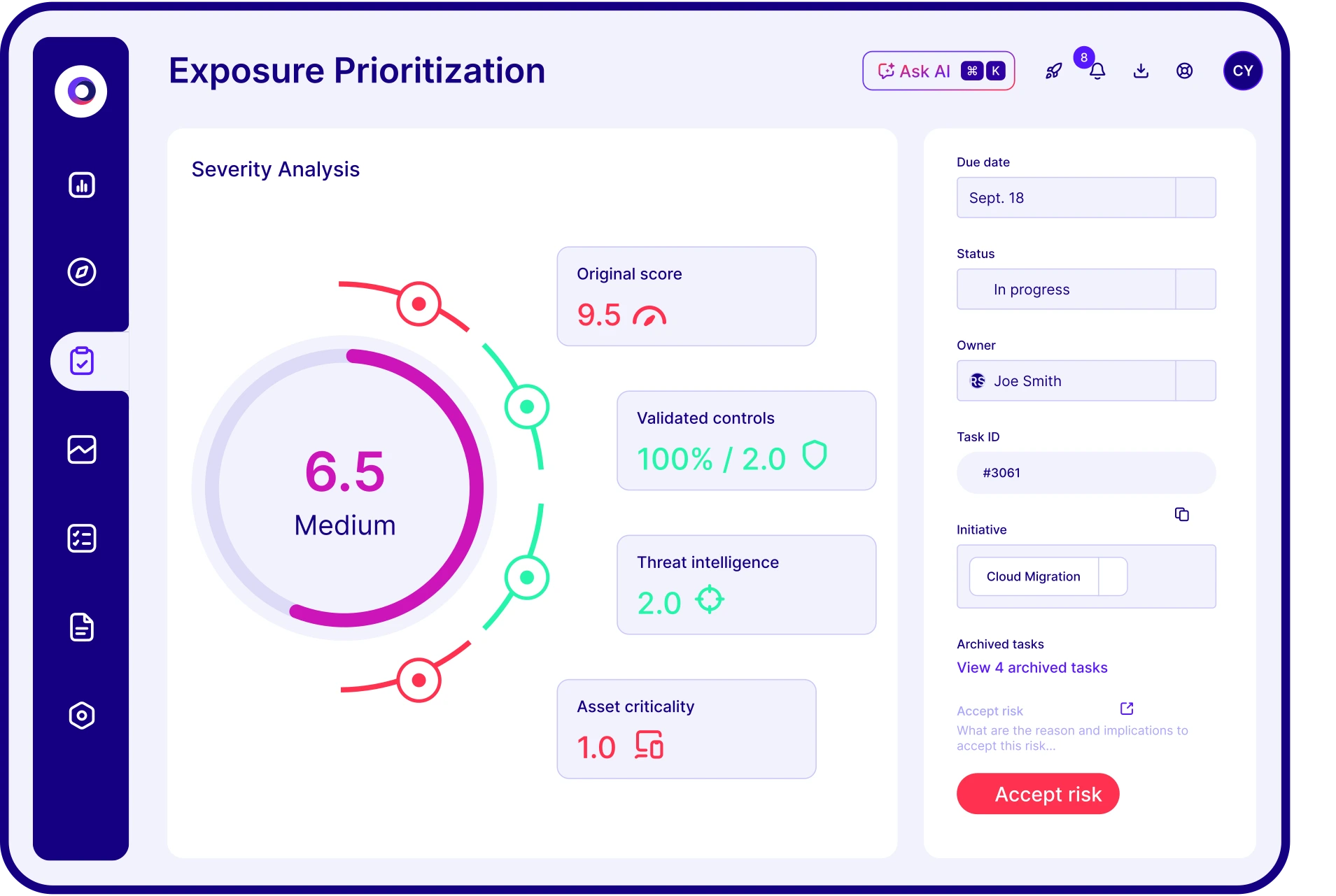
This generates a true exposure risk score—prioritizing based on what’s actually exploitable in your environment to ensure optimal resource allocation.
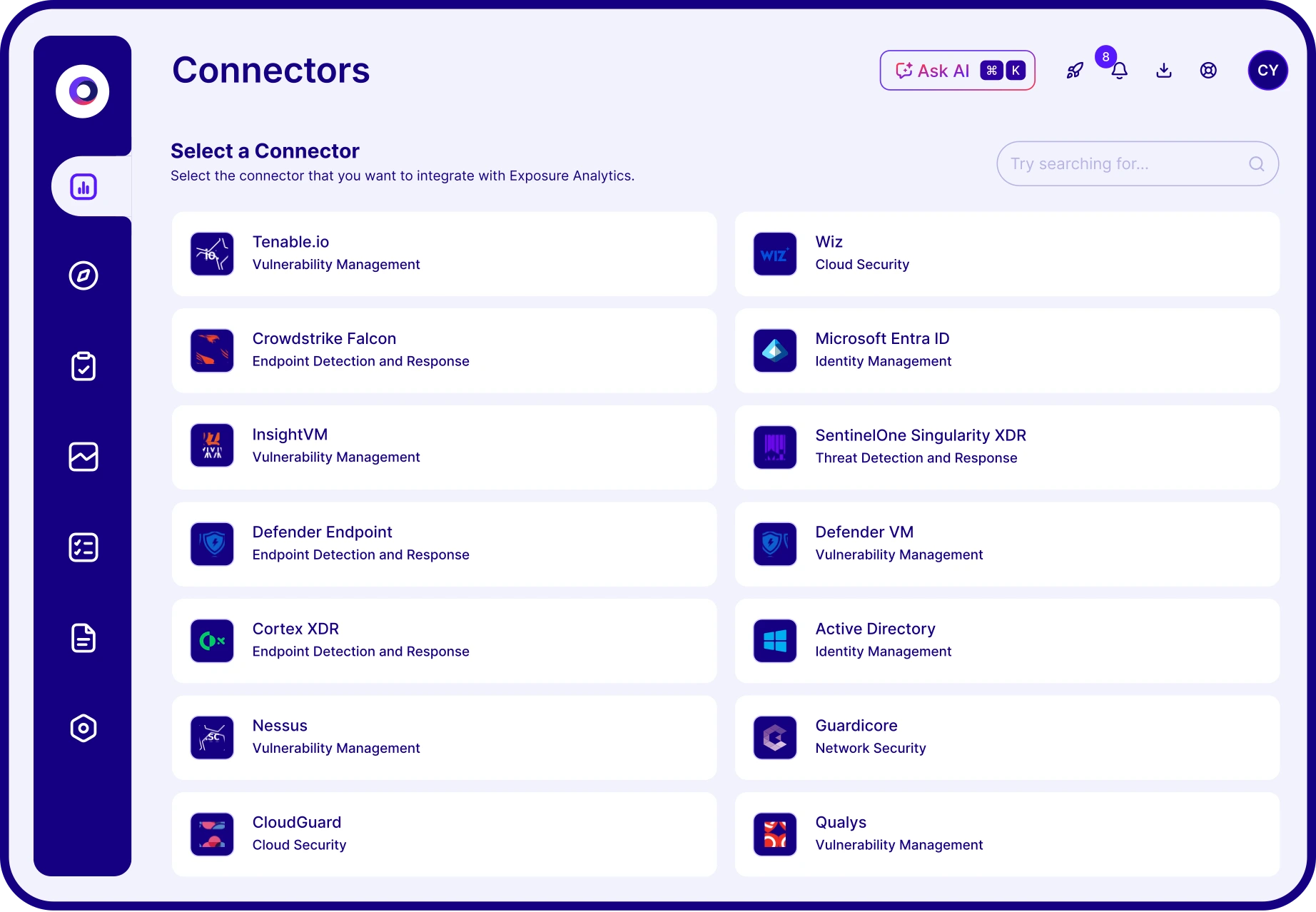
No. Cymulate complements your existing tools by aggregating and enhancing the data they provide. It integrates with vulnerability scanners, SIEMs, EDR/XDR and other asset discovery tools to deliver a complete exposure management view—centered on actionable, validated risk.