Exposure Management Demands Validation
Focus on the exploitable with exposure management that builds threat resilience.
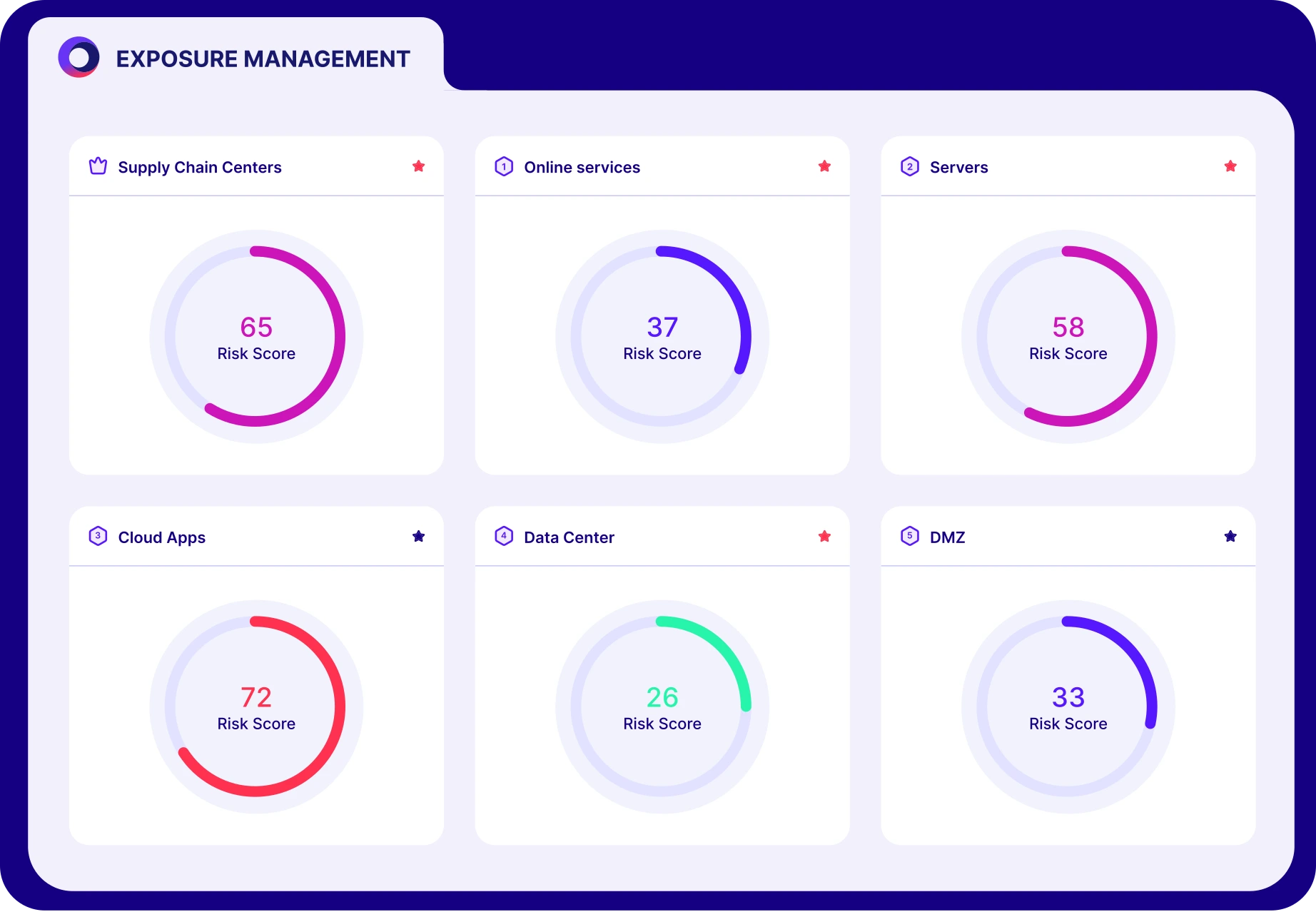
Proactive security requires a complete approach to continuous threat exposure management (CTEM).
SecOps have too many exposures to prioritize
Less likely to suffer a breach with CTEM
Source: Gartner
CTEM tasks automated today, leaving gaps
Source: Gartner
Elevate CTEM with Validation to Prove the Threat & Improve Resilience.
Cymulate puts the “T” in CTEM by continuously validating threats and integrating with vulnerability management and exposure discovery. Security operations, red teams and vulnerability management teams use Cymulate to collaborate and drive CTEM with a focus on proven, validated threats that measurably improves threat resilience.
Prove threat resilience
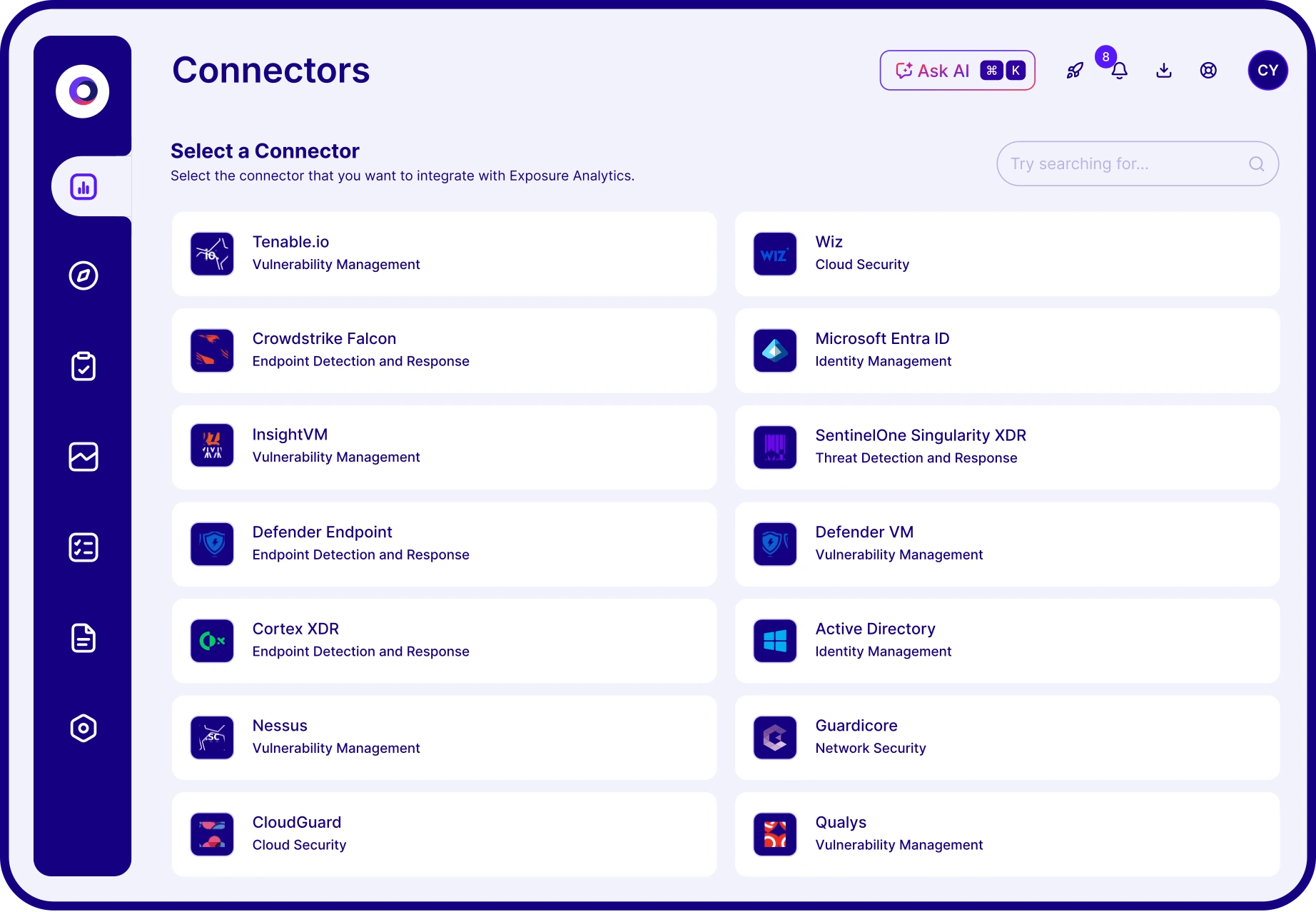
Integrate exposure discovery
Focus on the exploitable
Build threat resilience
CTEM Benefits & Outcomes
52%
Reduction in critical exposures
AVG. of CYMULATE CUSTOMERS
30%
Increase in threat prevention
AVG. of CYMULATE CUSTOMERS
60%
Increase in team
efficiency
FINANCE COMPANY
What our customers say about us
Organizations across all industries choose Cymulate to drive their exposure management programs with exposure validation.
Exposure Management FAQs
Exposure management is the continuous process of identifying, assessing and addressing security exposures across your digital ecosystem. It encompasses all endpoints, systems, applications and data. The goal is to provide security teams with the visibility and context they need to understand which exposures are truly exploitable—and therefore pose a real threat to the organization.
Cymulate drives exposure management by aggregating exposures from vulnerability scanners and discovery tools, correlating them with business context and validated threats. This ensures teams can focus on what truly matters, significantly improving threat resilience and operational efficiency.
Cymulate drives CTEM by offering a complete and continuous approach to threat exposure management. It aligns with Gartner’s CTEM framework and enhances every phase:
- Scoping: Defines the baseline security posture across your assets.
- Discovery: Seamlessly integrates with your existing tools to consolidate exposures.
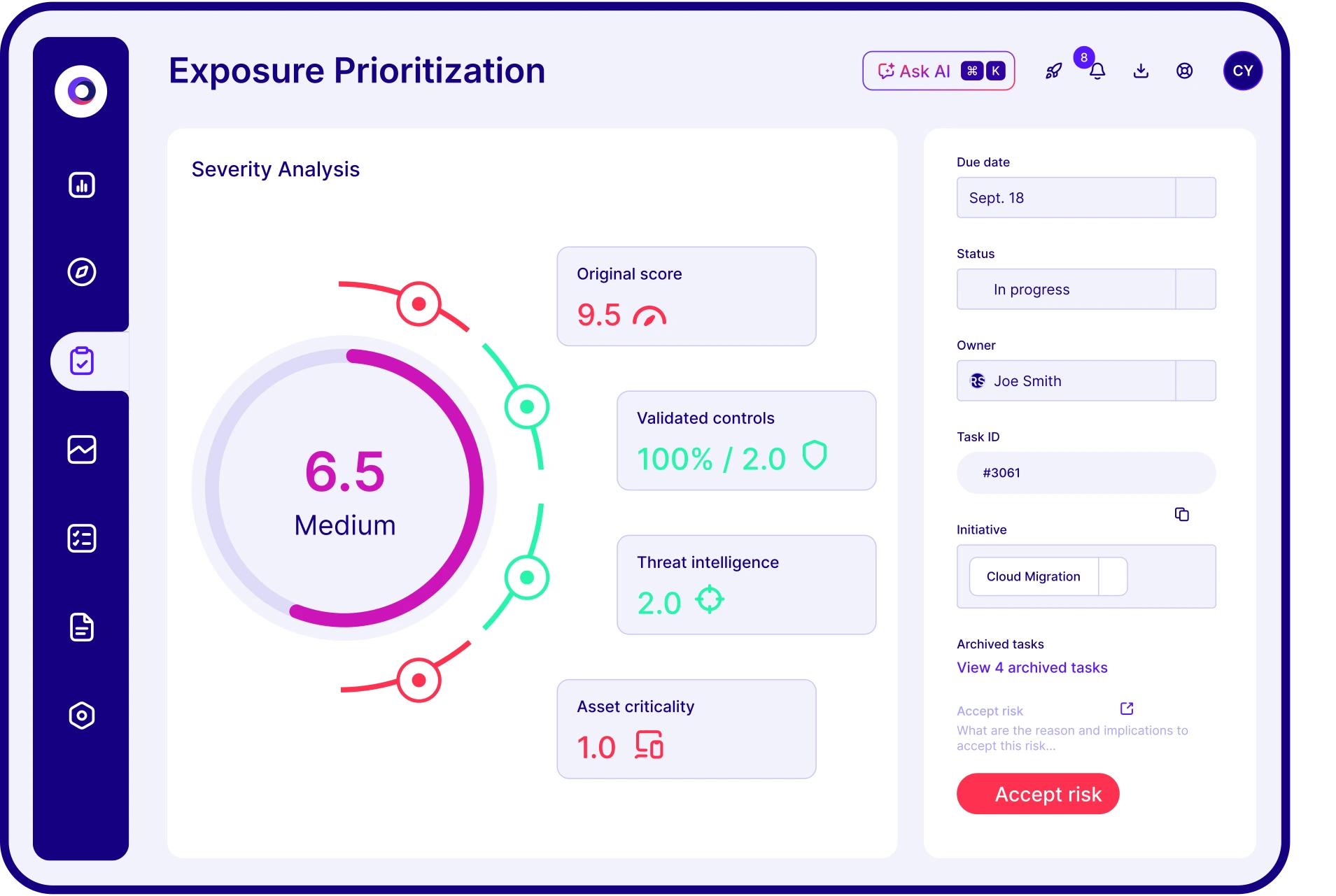
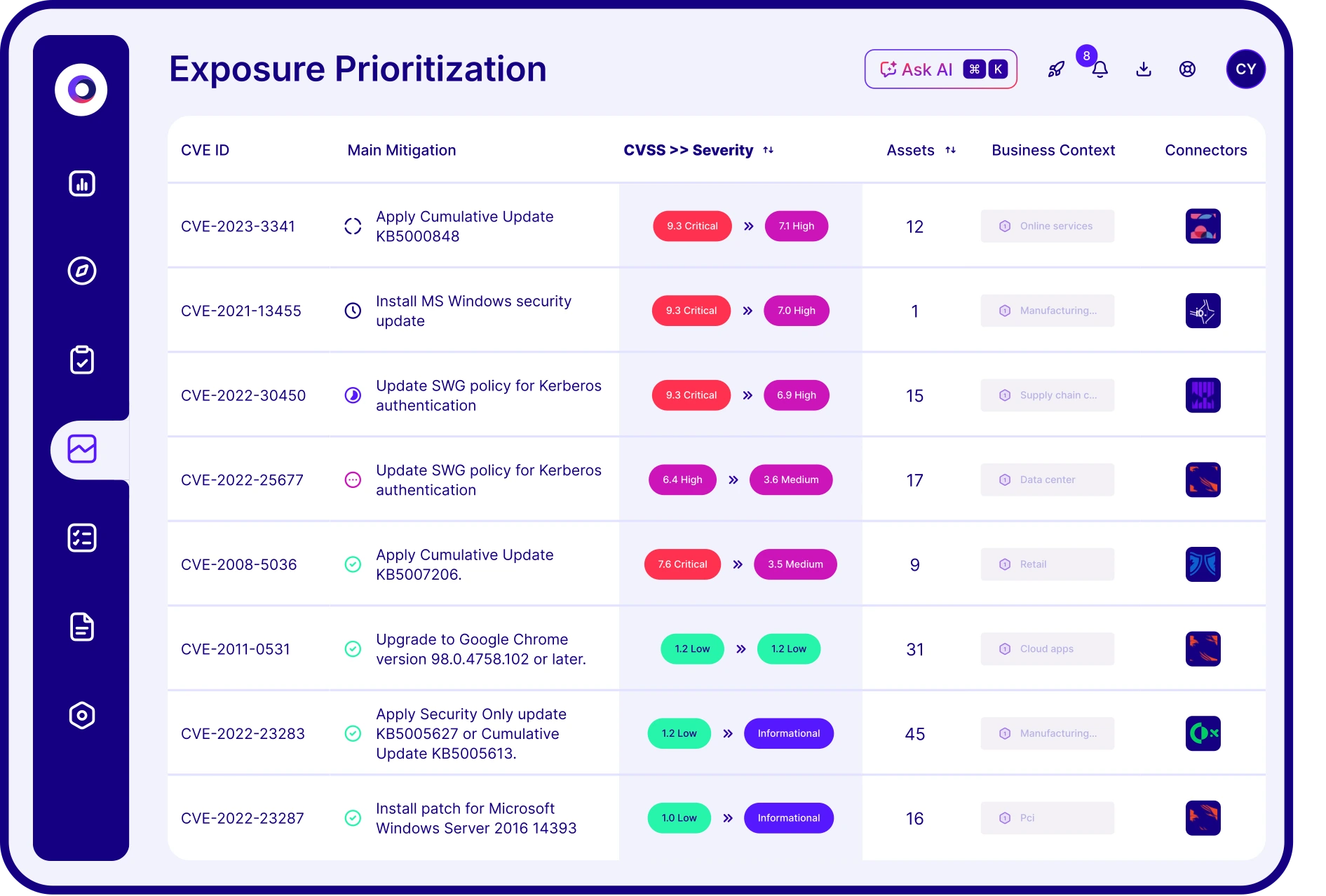
- Prioritization: Correlates assets and threats based on real exploitability and business risk.
- Validation: Uses advanced, continuous testing to prove threats.
- Mobilization: Generates guided remediation and automates control updates.
With Cymulate, CTEM becomes more than a strategy—it becomes an operational reality powered by validation and proof.
Automated and continuous threat validation is a cornerstone of Continuous Threat Exposure Management (CTEM) because it enables organizations to proactively understand, prioritize and mitigate real-world risks across their attack surface. It delivers:
- Real-time risk visibility on threat landscape and insights into exploitable vulnerabilities in terms of real-world attacker behavior.
- Continual validation of attack surface changes with deployment of new assets, configuration changes and new vulnerabilities.
- Prioritized recommendations accounting for which exposures are truly exploitable to reduce remediation fatigue.
- Threat intelligence alignment by ensuring threat validation mirrors the relevant threats.
Cymulate leverages AI and automation to make advanced testing fast and easy:
- AI simplifies threat exposure validation by running intelligent breach and attack simulations that map to the threats and detection rules
- Automation ensures continuous testing and integrates smoothly into existing workflows.
- Automated control updates and remediation guidance accelerate the response to threats.
This means teams spend less time on manual testing and guesswork—and more time improving their resilience and response strategies.
Yes, Cymulate offers seamless integrations with existing security tools, including vulnerability management solutions, SIEMs, and other security technologies. These integrations allow you to:
- Automatically import asset and exposure data.
- Enrich prioritization with business and threat context.
- Streamline validation and remediation workflows.
This interoperability helps unify your security stack and ensures CTEM processes are data-rich and automated.
Absolutely. Cymulate supports automated mitigation and guided remediation:
- The platform generates actionable plans based on validated threats.
- It pushes custom detection rules and control updates directly to your security tools.
- Teams can use the evidence and insights from Cymulate to immediately apply and verify remediations.
As one customer put it: “We launch assessments to see if our tools detect them. If they don’t, Cymulate provides mitigation guidance and Sigma rules, and we easily rerun the assessments to validate remediation.” – Karl Ward, Head of Cybersecurity at LV=.