The Role of Network Segmentation in Mitigating DHCP Spoofing Risks
Networks are the keystone of virtually every business, and the need for secure, reliable communication is a vital component. However, with this interconnectedness comes the constant threat of cyberattacks that can disrupt operations, steal sensitive data, or compromise an entire network without any warning. One such attack that has become increasingly prevalent is Dynamic Host Configuration Protocol (DHCP) spoofing.
What is DHCP Spoofing?
In order to understand what Dynamic Host Configuration Protocol (DHCP) Spoofing is, we first must define DHCP. DHCP is the network protocol responsible for automatically assigning IP addresses to devices on a network, where it then allows devices to connect seamlessly without requiring manual configuration.
In a DHCP spoofing attack, a threat actor impersonates a legitimate DHCP server and responds to requests from devices on the network. The attacker can then assign rogue IP addresses, referred to as Man-in-the-middle (MITM), potentially directing devices to malicious websites, capturing sensitive data in the process. When the threat actor can access and take control of network traffic, they can cause significant damage in the form of business operations disruptions, loss of integrity and confidentiality as well as release highly sensitive data.
While there are different types of IP protocol attacks, such as ARP Poisoning, which is typically easier to detect than a DHCP Spoof attack, because it’s directly modifying ARP caches. DHCP Spoofing are harder to detect because the attacker is often disguised as a legitimate DHCP server.
How does DHCP Spoofing Work?
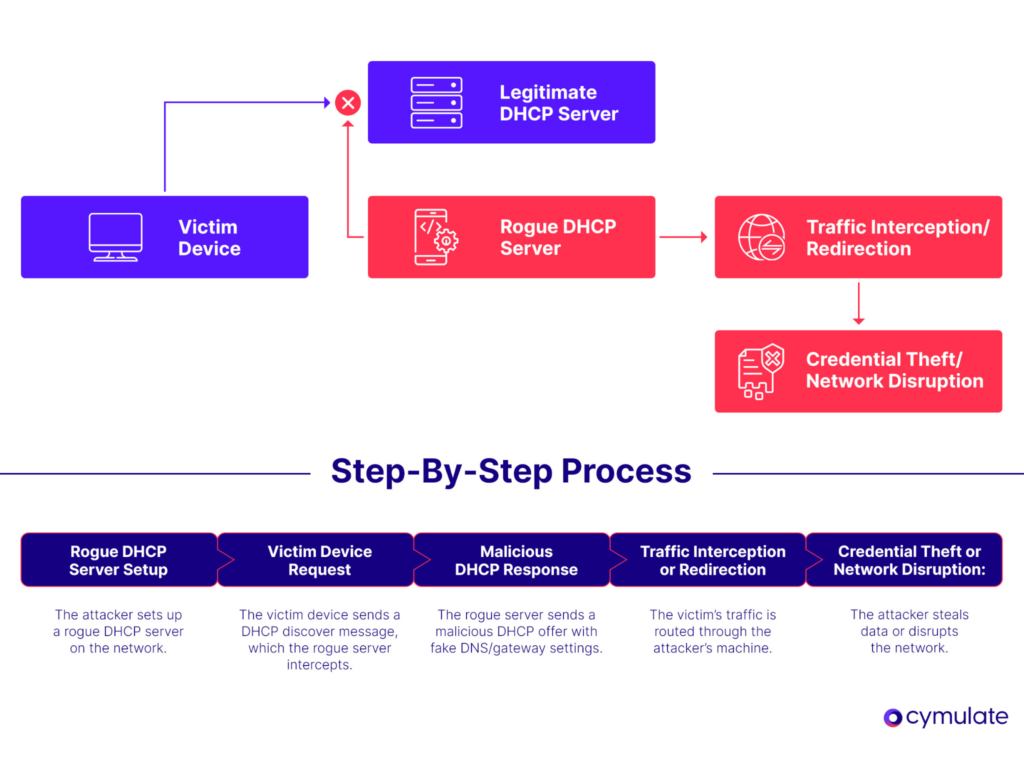
1. Rogue DHCP Server Setup
In this initial step, the attacker sets up a rogue DHCP server on the same network as the legitimate DHCP server. The rogue server then broadcasts DHCP offers and responses to the network devices, pretending to be the real DHCP server. The rogue server might use a tool like dhcpd or specialized spoofing software to achieve this.
2. Victim Device Request
Now that the attacker has set up a rogue DHCP server, the attacker’s server is able to send and respond to a DHCP discover message. The victim will see this message on their own device (e.g., a computer, smartphone, tablet, etc.), where it connects to the local network and broadcasts the discover message, requesting an IP address. The victim device will believe this is a legitimate request from the DHCP server.
3. Malicious DHCP Response
The third step involves how the attacker wants to direct the victim to malicious services, or ensure traffic is sent through their device to facilitate MITM attacks. This happens by the rogue DHCP server mentioned in step one sending a malicious DHCP offer to the victim’s device, offering an IP address and potentially other critical network settings, like DNS and gateway.
The malicious DHCP response contains harmful configurations like fake DNS servers to redirect traffic to an attacker-controlled site or a fake gateway, redirecting all traffic through the attacker’s machine.
4. Traffic Interception or Redirection
In the fourth step the victim’s device accepts the attacker’s malicious DHCP offer, configuring itself with the attacker’s provided IP address, gateway and DNS settings. The device is now ready to send its traffic through the attacker’s machine, or the rogue gateway.
On the attacker’s side, they can either MITM and intercept and potentially alter the victim’s traffic as it passes through the attacker’s device or redirect the victim to malicious websites or block access to certain services. Either way, the attacker gains the ability to monitor, alter or block network traffic, allowing them to further exploit their victim’s information.
5. Credential Theft or Network Disruption
In the fifth and final step, if the attacker has setup malicious services, such as fake websites, then they can capture user credentials, credit card details and sensitive data as the victim interacts with the fake website. In some instances, the attacker may cause network disruptions by sending incorrect IP configurations, denying network access or causing denial of service (DoS) by interfering with the DHCP process.
Is a Network Vulnerable to DHCP Spoofing?
Most any network is susceptible to being attacked in some way and DHCP Spoofing presents its key risk factors that increase that likelihood:
- Flat networks (without segmentation or VLANs): In flat networks where all devices are on the same broadcast domain, there are no barriers to prevent rogue DHCP servers from responding to DHCP requests. Without segmentation or VLANs to isolate sensitive devices or network areas, an attacker can easily introduce a rogue server into a network.
- Lack of DHCP snooping configurations: DHCP snooping is a security feature that helps prevent unauthorized DHCP servers from operating on networks and without it enabled, network switches have no way to differentiate between legitimate and rogue DHCP servers.
- Weak access control to network infrastructure: If an attacker can physically or remotely access a network device, then they can likely configure a rogue DHCP server or manipulate network settings. Weak access control policies on network devices increase the chances of an attacker gaining unauthorized access to devices.
- No monitoring for rogue DHCP servers: Without regular monitoring, unauthorized DHCP servers can operate undetected. Implementing tools that detect suspicious DHCP traffic or rogue servers is critical in order to mitigate any threat quickly.
5 Ways to Protect Against DHCP Server Attacks
Mitigating DHCP spoofing requires a combination of proactive security measures to ensure the integrity and reliability of network services.
- Network segmentation: Implementing network segmentation by isolating DHCP services into different VLANs helps contain the impact of any potential attack and prevents attackers from easily affecting the entire network, allowing for tighter control over where the DHCP services are available.
- DHCP Snooping: This method is a security feature that configures network switches to monitor DHCP traffic and restrict which ports can send DHCP responses, while blocking rogue DHCP servers from issuing IP addresses, preventing attackers from manipulating network setting or launching MITM attacks.
- Access control: Access control should be enforced by restricting physical and network access to authorized users and devices only. This method prevents attackers from physically connecting unauthorized devices to the network and impersonating a legitimate DHCP server.
- MAC address filtering: Can be used to ensure that only known and authorized devices can request DHCP leases. This method helps avoid unauthorized devices attempting to access DHCP services, making it harder for attackers to spoof legitimate clients.
- Intrusion detection: The intrusion detection system (IDS) helps to monitor DHCP traffic and identify unusual or malicious behavior; while setting up alerts allow administrators to quickly detect and respond to any spoofing attempts. This provides real-time monitoring and early detection of potential attacks.
How Cymulate Can Help Combat DHCP Spoofing
Cymulate offers a powerful, AI-driven security validation platform that assists organizations in continuously assessing and strengthening their defenses against various cyber threats, including DHCP spoofing and other network-based attacks. With our capabilities, we enable security teams to proactively test the effectiveness of their network defenses through simulation-based attack scenarios that replicate real-world threats, offering valuable insights into potential vulnerabilities.
Through the Cymulate Exposure Validation Platform, organization’s security teams can:
- Simulate DHCP Spoofing Attacks: Cymulate can test how vulnerable the network is to rogue DHCP servers by simulating various attack scenarios. This helps identify gaps in DHCP protection mechanisms, such as lack of DHCP snooping or network segmentation.
- Test Network Segmentation: Through simulations, Cymulate can assess whether network segmentation (using VLANs) is effectively isolating critical infrastructure and preventing unauthorized access from rogue devices.
- Evaluate Access Controls: Cymulate can simulate how attackers might exploit weak access control policies, such as unrestricted physical access or weak MAC address filtering, providing insight into potential security gaps.
- Detection of Weak Configurations: Cymulate provides continuous, automated testing to identify weak configurations, misconfigurations, or overlooked security gaps that might otherwise be missed during routine audits. This includes testing for misconfigured network segments, improperly configured DHCP snooping, or missing access controls that attackers could exploit.
- Proactive Defense Improvement: Continuous validation ensures that security measures remain aligned with the latest threat landscape, offering ongoing opportunities for improvement. With each simulation, organizations can refine their defenses to make them more resilient to both known and emerging cyber threats.
Book a demo today to learn more about how Cymulate can help your organization prevent a DHCP Spoofing attack.
Key Takeaways
As cyberattacks grow more sophisticated, protecting your network from threats like DHCP spoofing becomes critical. Network segmentation is a powerful and practical strategy that not only limits the impact of such attacks but also provides a structured framework for managing and securing your network.
By dividing your network into smaller, more manageable segments, you reduce the chances of an attacker gaining full control and ensure that, in the event of an attack, the damage remains contained.
When combined with other security measures such as DHCP snooping, ACLs, and regular monitoring, network segmentation is a strong pillar in your defense against DHCP spoofing. It's time to consider how segmentation could elevate your network's security and shield your organization from one of the most common yet dangerous threats in today’s digital world.


