Threat Exposure Management: Driving Proactive Cybersecurity Outcomes

Organizations are up against a threat landscape that evolves faster than most defenses can adapt. Staying ahead requires more than patching known issues — it demands visibility into how attackers see your environment. That’s where threat exposure management (TEM) comes in.
Unlike traditional vulnerability programs that react after the fact, TEM focuses on visibility and validation. It measures how exposed the organization truly is, how it appears from an attacker’s perspective and how well its existing controls stand up to real-world threats.
This guide explores the intricacies of TEM, breaking down its components, business impacts and best practices for maximizing its effectiveness.
Key highlights:
- Threat exposure management is a proactive approach to identifying, validating and reducing cyber risk across an organization’s entire attack surface.
- It replaces reactive vulnerability management with continuous visibility, testing and measurement of how controls perform against real-world threats.
- By aligning security outcomes with business objectives, exposure management helps CISOs prioritize investments and demonstrate measurable risk reduction.
- Cymulate enables organizations to operationalize risk management through continuous control validation, automated testing and actionable risk insights.
What is threat exposure?
Threat exposure is the sum of every weakness, misconfiguration, or overlooked system that could give an attacker a way into your environment. It spans the entire digital footprint (from networks, endpoints and cloud workloads to identities and third-party integrations), and reflects how the organization appears from an adversary’s point of view.
Knowing where real risk resides, not just where controls are documented, allows an enterprise to create an effective strategy for threat exposure management, turning visibility into action. TEM is an approach that identifies and validates exposures, measures how effectively controls perform and prioritizes what matters most to the business.
Rather than reacting to vulnerability reports in isolation, a strong management strategy links findings to potential impact and attacker behavior, creating a live picture of risk that can be measured and reduced over time.
Why threat and exposure management matters
Cyber threats evolve faster than most organizations can patch, monitor, or even detect them. New vulnerabilities surface daily across cloud services, identities and third-party ecosystems, creating blind spots that attackers exploit long before they appear in a vulnerability report.
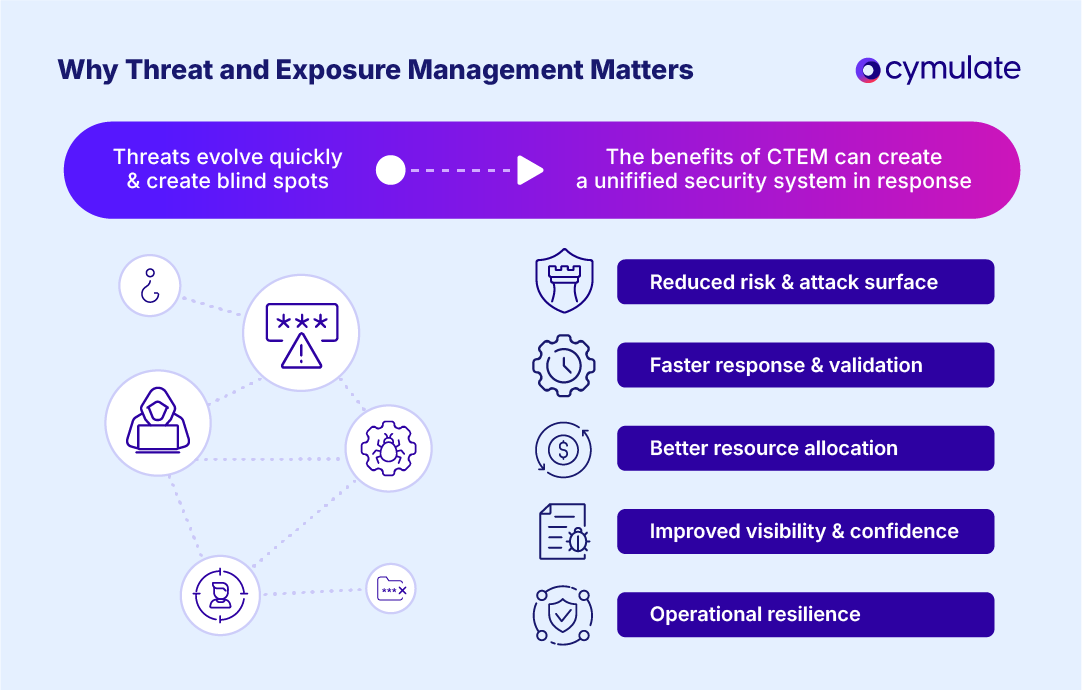
According to our State of Exposure Management & Security Validation Report, average control effectiveness across industries remains between 60 and 70 out of 100, leaving most organizations operating at a medium-risk posture rather than a secure posture. Traditional, reactive approaches to threat and exposure management can’t keep pace — they provide snapshots when what’s needed is a continuous view of risk.
The longer these exposures persist, the greater the chance of disruption, data loss, or reputational damage. Exposure management solutions change that equation by identifying and validating risks, allowing teams to proactively act on what matters most. The benefits extend beyond security operations:
- Reduced risk and attack surface: Proactively finding and addressing exposures lowers the likelihood of breaches and costly incidents.
- Faster response and validation: Continuous testing and feedback loops shorten the time between discovery, threat exposure remediation and verification.
- Better resource allocation: Prioritizing exposures based on business impact ensures that you direct time and budgets toward the security risks that truly matter.
- Improved visibility and confidence: Gaining a real-time view of exposures provides leadership and boards with measurable, defensible insight into the organization’s risk posture.
- Operational resilience: Aligning threat exposure with incident response, vulnerability management and compliance strengthens the organization’s ability to anticipate and recover from threats.
Components of the exposure management process
Exposure management leverages technologies such as exposure validation, breach and attack simulation (BAS) and security control validation to identify and validate exposure risks. Consolidating these cybersecurity capabilities, along with third-party data sources like vulnerability scans, cloud security posture management (CSPM) and continuous control monitoring, plays a crucial role in enhancing the effectiveness of continuous threat exposure management (CTEM).
Here are the main components of the risk validation process:
Integration and holistic view
Integrating cyber attack surface management (CAASM), BAS and third-party data provides a comprehensive view of the organization’s cybersecurity posture. CAASM delivers visibility into all assets and focuses on identifying vulnerabilities, while BAS simulates attacks to validate these vulnerabilities.
When combined with third-party data, such as vulnerability scans and CSPM, this integration offers a detailed and nuanced understanding of the organization’s security vulnerabilities.
Prioritization based on validated risk
A consolidated approach enables organizations to validate and quantify the risks associated with different vulnerabilities and threats. By using BAS to simulate real-world attack scenarios, organizations can understand which vulnerabilities are more likely to be exploited by attackers.
This information and insights from CAASM and third-party data enable more informed decision-making about which vulnerabilities to prioritize for remediation.
Risk assessment and remediation
The data gathered through TEM tools can be analyzed to assess the level of risk each vulnerability poses to the organization. This assessment considers the severity of the vulnerability and the importance of the affected asset to business operations. The organization can then prioritize remediation efforts, focusing first on vulnerabilities that pose the most significant risk.
Continuous monitoring and improvement
Continuous monitoring allows for the detection of new vulnerabilities and changes in the organization’s attack surface. This ongoing process ensures that the organization can quickly respond to new threats and continuously improve its security posture.
Understanding the threat exposure management framework
An effective program for managing threat exposure follows a continuous, repeatable cycle. It connects asset discovery, validation and remediation into a framework that keeps pace with the organization’s changing attack surface. While tools and processes may differ, these four core stages remain consistent:
1. Scoping and discovery
Threat exposure management begins with defining the scope of what will be monitored — across on-prem, cloud, remote and third-party environments — and identifying all assets within it. This step establishes visibility into the whole attack surface and highlights where unknown or unmanaged assets may exist.
How to scope and discover threats:
- Map all known assets, data flows and integrations
- Use CAASM or ASM tools to uncover unknown or shadow IT assets
- Establish an initial baseline of the organization’s attack surface
2. Prioritization and validation
Once exposures are discovered, they’re validated through testing and analysis. Breach and attack simulation tools, along with control validation, help determine whether vulnerabilities can be exploited by bad actors and what the impact would be. Exposures are then ranked based on risk, asset value and business impact.
How to prioritize and validate risks:
- Validate exploitability using BAS or penetration testing
- Correlate vulnerabilities with threat intelligence and asset criticality
- Rank findings by potential impact and likelihood of exploitation
3. Remediation and response
Validated risks are addressed through remediation or compensating controls. The focus is on tackling what matters most — exposures that intersect with critical systems or known threat activity. Coordinated workflows between security and IT operations accelerate closure.
How to remediate and respond to threats in your environment:
- Assign ownership and remediation timelines to relevant teams
- Implement patches, configuration changes, or policy updates
- Validate fixes through retesting and control assurance
4. Measurement and reporting
The final stage of the cyber TEM framework turns the cycle into a loop. Continuous monitoring ensures that new assets and vulnerabilities are added to the inventory, previous fixes are verified and tracking of performance metrics stays consistent over time. As a result, teams create a measurable, always-current picture of organizational risk.
How to measure and report on the effectiveness of your TEM framework:
- Measure metrics such as exposure reduction and the mean time to detect (MTTD) and remediate. According to our Threat Exposure Validation Impact Report 2025, enterprises that leverage exposure validation improved their MTTD by 47%.
- Reassess previously remediated assets to ensure resilience
- Feed results back into the discovery phase for ongoing optimization
How to align threat exposure management strategy with business goals
Threat exposure management is a way to connect cybersecurity performance with business priorities. Every exposure represents a potential disruption to operations, customer trust, or compliance. By quantifying risk in business terms, this security validation strategy empowers CISOs and security leaders to make decisions that drive measurable value, not just technical wins.
This alignment helps security teams:
- Understand and measure exposure risks: By adopting the perspective of an attacker, CISOs can gain a deeper understanding of their organization’s exposure risks. This insight is crucial in measuring the security posture accurately and making informed decisions.
- Prioritize projects based on exposure risk: Exposure management aids in identifying and prioritizing security projects and initiatives based on their potential to reduce exposure risk, helping allocate resources efficiently and effectively, addressing the most critical vulnerabilities first.
- Unify SecOps towards a common goal: Managing exposure provides a framework for unifying security operations around the common goal of reducing cyber risk. By fostering collaboration and a shared understanding of security priorities, teams can work more cohesively towards mitigating threats.
Aligning the cybersecurity program with the overall business strategy is another critical aspect of CTEM. This alignment involves:
- Using standard, non-technical language: To define and communicate acceptable risk levels in terms that are understandable to non-technical stakeholders, fostering better decision-making and support across the organization.
- Agreement on handling unacceptable risks: Establishing a clear understanding and agreement on handling risks exceeding acceptable thresholds, including the potential for business operation disruptions during mitigation efforts.
- Justifying budgets and projects: Proper exposure handling enables CISOs to justify cybersecurity budgets and projects by demonstrating how they contribute to achieving business goals and reducing risks, thereby securing necessary resources and support.
- Measuring outcomes with tangible results: Management provides a way to measure the outcomes of cybersecurity efforts with tangible results, such as reduced incidence of successful attacks and improved compliance with regulatory standards. These metrics are vital in demonstrating cybersecurity investments’ value to stakeholders and in continuously improving security practices.
Managing the threat of exposure: key challenges
Even the most well-planned risk management frameworks face obstacles that limit their effectiveness. These challenges often arise from organizational complexity, competing priorities and legacy processes that can’t keep up with modern hybrid environments.
Recognizing and addressing these five exposure management barriers is key to building a sustainable, measurable TEM strategy.

1. Visibility gaps across environments
Many organizations struggle to maintain a complete view of their digital footprint. Cloud workloads, remote devices and third-party connections expand faster than traditional asset inventories can track. These blind spots create opportunities for potential attackers to exploit forgotten or misconfigured systems, often outside the reach of existing controls.
How to overcome this threat exposure challenge:
- Build a single, continuously updated asset inventory that spans on-prem, cloud and shadow IT
- Use CAASM tools to discover and classify assets as they appear automatically
- Ownership should extend across the entire exposure lifecycle, ensuring accountability doesn’t stop at discovery
2. Alert fatigue and data overload
Vulnerability scanners, threat feeds and monitoring tools generate enormous volumes of alerts — most of which lack context. Without clear prioritization, analysts waste valuable time sorting through noise while critical exposures remain unresolved. This overload can erode confidence in the program and increase the likelihood of missing high-impact risks.
How to overcome this threat exposure challenge:
- Correlate vulnerability data with threat intelligence and business-critical assets
- Use breach and attack simulation (BAS) to validate which vulnerabilities are actually exploitable
- Automate correlation and filtering to reduce false positives and duplicate alerts
3. Resource and ownership constraints
Coordinating exposure response often spans multiple teams — security, IT, compliance and risk — but without clear accountability, issues can linger unaddressed. Limited staffing and competing priorities further slow remediation, creating frustration and fatigue within security operations.
How to overcome this threat exposure challenge:
- Define explicit ownership for remediation tasks across teams and business units
Set clear SLAs and escalation paths for exposure resolution - Automate repetitive validation and reporting processes to maximize efficiency
4. Tool and process fragmentation
When vulnerability management, testing and reporting tools operate in isolation, critical data remains siloed. This fragmentation leads to duplicate efforts, inconsistent results and delayed remediation. A lack of integration also makes it challenging to maintain a single source of truth for leadership reporting and trend analysis.
How to overcome this threat exposure challenge:
- Integrate vulnerability management, BAS and ticketing tools into unified workflows
- Use dashboards or orchestration platforms to consolidate exposure and risk data
- Standardize data formats and reporting structures for consistent visibility across teams
5. Lack of measurable outcomes
Even well-executed security programs can lose executive support if they fail to demonstrate measurable progress. Without clear metrics, it’s difficult to justify continued investment or validate the value of remediation efforts. The program must translate technical success into business results that resonate with leadership and stakeholders.
How to overcome this threat exposure challenge:
- Track metrics such as exposure reduction and mean time to detect and remediate
- Compare performance over time to demonstrate tangible risk reduction
- Link metrics to business outcomes like uptime, compliance and cost avoidance
Best practices for cyber threat exposure management
Effective cyber threat exposure management requires consistency, context and collaboration. The best programs combine continuous visibility with actionable insights, ensuring that teams aren’t just identifying risk, but actively reducing it.
These five TEM best practices help organizations operationalize a continuous threat exposure management strategy and turn it into a measurable driver of business resilience:
- Maintain continuous visibility: Automate asset discovery and monitoring to ensure every environment — cloud, on-prem and third-party — remains accounted for and secure. According to our recent Impact Report, this is currently a blind spot for many, with only 9% of surveyed enterprises running exposure validation in their cloud environments daily.
- Validate defenses continuously: Use breach and attack vector simulation in addition to other testing methods to confirm that existing security controls perform as expected against real-world threats.
- Prioritize based on business impact: Rank exposures using exploitability, asset value and threat activity to focus resources on the vulnerabilities that pose the most significant operational or financial risk.
- Integrate TEM across functions: Connect vulnerability management, threat intelligence and incident response workflows to eliminate silos and accelerate remediation.
- Communicate outcomes: Track metrics such as exposure reduction and mean time to detect and remediate, translating progress into business language that resonates with leadership.
Get advanced threat exposure remediation with Cymulate
Continuous risk validation software is vital to modern cybersecurity. For organizations aiming to adopt a comprehensive and proactive approach to securing their environments, the Cymulate platform is an excellent choice.
With advanced capabilities in continuous monitoring, breach and attack simulation, exposure and control validation, Cymulate empowers security teams to:
- Identify and mitigate critical exposures
- Reduce the likelihood of successful attacks
- Strengthen both their security posture and business resilience
Book a demo today and see how Cymulate can help you enhance your organization’s existing threat exposure management program.