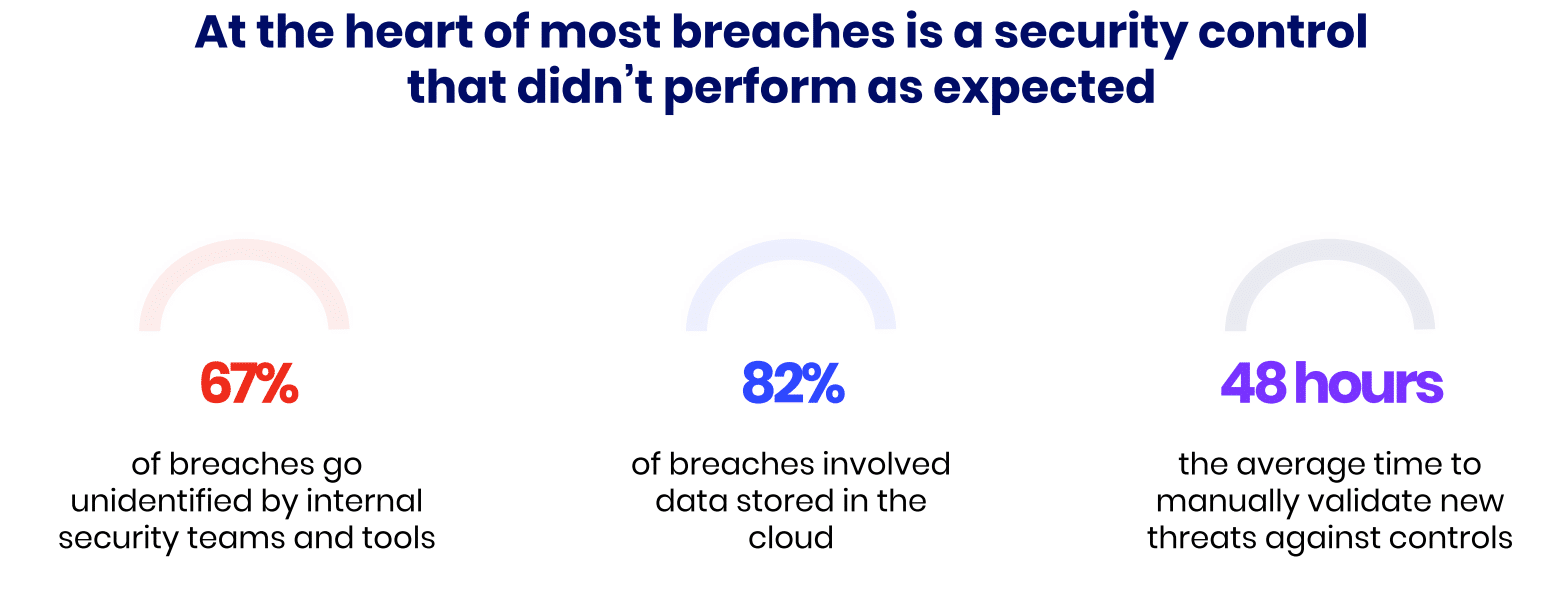
Security Control Validation
Global spending on cybersecurity is nearly $200 billion annually, with software and security controls accounting for about half. However, investing in security controls does not automatically mean your security is under control. Security control validation empowers organizations to maximize the effectiveness of their existing security tools while continuously improving by implementing new detection rules to counter the latest threats.
What is security control validation?
Security control validation is not a tool or a framework, but rather the process of making sure that security controls such as firewalls, email gateways, data exfiltration, endpoint and cloud security etc., are correctly implemented, configured, and able to mitigate risks as expected. It’s a way for organizations to identify potential problems with their security posture and mitigate potential vulnerabilities detected in the validation process.
How are security controls tested and validated?
There are two main ways to find out if your security controls are working as they should: you can suffer an attack, or you can simulate one.
Manual methods, including penetration testing and red teaming, involve ethical hackers and security professionals simulating attacks to identify weaknesses and evaluate the effectiveness of defense mechanisms.
Security validation platforms such as breach and attack simulation (BAS) tools provide ongoing assessments by simulating attack scenarios in controlled environments.
With a breach and attack simulation, you’re testing whether the controls are set up and working properly in an environment that is dynamic and constantly changing, as the threat landscape ebbs and flows, and as threat actors become more sophisticated with new techniques.
What controls are validated?
All security controls an organization has in place should be continuously validated and tested to ensure their effectiveness and to identify potential problems. These controls include:
- Email controls: Are your email servers capable of detecting a phishing, malware or social engineering attack?
- Web controls: Are your web gateways and proxies up to the task of preventing or detecting malicious links and payloads?
- Network controls: Can you confirm that your firewalls are optimally designed to guard against a malicious actor? This might include validating that detection systems are robust enough to guard against intrusive activity.
- Endpoint controls: Will your endpoints survive a targeted attack from a sophisticated threat actor?
- Cloud controls: Does your cloud architecture contain security gaps and redundancies that could provide a portal for malicious actors to steal or exploit your vital assets?
- SIEM observability: Can your security operations team detect and respond to malicious activity in your environment?
- Data exfiltration: Are you confident that your critical and sensitive data is protected from unauthorized access?
Security control validation vs pen-testing and red teaming
Manual cyber security testing methods such as pen-testing and red teaming are often resource-intensive and expensive. The results of pen-testing and red teaming tend to only reflect threats discovered at a set point in time or related to a specific security control or vulnerability.
While ticking through the list of misconfigurations, malicious payloads and links from the last report, new ones will likely emerge – and could go undetected for months. All of this means that you may not be as secure today as you were six months ago.
Security Control Validation, on the other hand, is automated and ensures key security controls in your environment are tested and validated on a continuous basis while optimizing the controls for better protection. Some of the key benefits are:
- Real-Time Insights: Automated security control validation provides real-time insights into the effectiveness of security measures, allowing for prompt identification and remediation of vulnerabilities.
- Cost Efficiency: By automating the validation process, organizations can reduce the need for frequent, costly manual testing, thus optimizing their security budgets.
- Consistency and Reliability: Automated validation ensures that security controls are consistently and reliably tested, minimizing the risk of human error and oversight.
- Adaptability: As new threats emerge, automated systems can quickly adapt by updating detection rules and validation procedures, ensuring that security measures are always current and effective.
- Improved Compliance: Continuous validation helps organizations maintain compliance with regulatory standards by providing ongoing evidence of security control effectiveness.

Key Takeaways
Even if the most expensive endpoint and cloud solutions have been deployed, without continuous testing and validation of security controls and running breach-and-attack simulations, there is still susceptibility to risks such as financial loss, operational impact and downtime, brand erosion, data leakage and exploitation, and more.
Security Control Validation is the answer to manual, point-in-time pen-testing. It’s automated and ensures key security controls are tested and validated on a continuous basis while optimizing the controls for better protection. It allows organizations to:
- Optimize what you have. Security Control Validation enables making the most of the tools already in place while continuing to make improvements on a consistent basis by implementing new detection rules for the latest threats. This also applies to MSPs.
- Measure continuous improvements. Understand the current security posture and identify areas needing improvement. Set a baseline of how secure the organization is today and measure changes and improvements over time. This can be impacted by factors like the efficacy of tools and the changing threat landscape.
- Manage Drift. The IT environment, including controls, doesn’t remain static, especially in the cloud. With the constantly changing threat landscape, it’s crucial to maintain visibility to detect and manage any unknown changes to policies, controls, and applications, preventing potential ripple effects if left undetected.


