Validating Cloud Threat Detection with Wiz Defend and Cymulate

Cloud environments and attacker techniques are constantly evolving, making it challenging for security teams to determine whether their detection logic remains effective. Without continuous validation, cloud detections can drift, leaving blind spots that only surface during real incidents.
Wiz continuously identifies and prioritizes risk across cloud configurations, identities and runtime activity, with Wiz Defend focusing on detecting malicious behavior across cloud workloads. Cymulate complements this by validating those detections through controlled, automated attack simulations.
The Cymulate–Wiz integration allows security teams to move from assumed coverage to proven detection by safely simulating real-world cloud attack scenarios and verifying how Wiz Defend responds. Detection results are correlated and displayed in Cymulate, making it clear what was detected, what was missed and where detection logic needs improvement.
At the center of this integration are three types of scenarios that reflect how threats actually emerge in cloud environments.
Detection engineering that goes beyond rule reviews
Wiz Defend is built to detect malicious activity. As a result, detection engineering and validation are critical. Most teams rely on hundreds of built-in detection rules. However, manually testing and validating those rules across various cloud providers and environments is just not practical for most security teams.
Cymulate removes this burden by providing ready-made attack scenarios aligned to Wiz Defend detection logic. Instead of reviewing rules one by one, teams can safely simulate live attacks to confirm:
- Detections fire as expected
- Events are logged correctly
- Detections flow into downstream systems such as SIEMs
Cymulate queries Wiz event and alert data through Wiz’s GraphQL API and correlates it with simulated attack activity, delivering direct, evidence-based validation of detection coverage. When gaps are identified, Cymulate provides Wiz-formatted detection rules that teams can apply directly in Wiz Defend, retest immediately and confirm coverage without manual rule development.
The three scenario types Cymulate validates with Wiz
1. Runtime threat detection (CWPP/EDR-based scenarios)
The first scenario type focuses on active malicious behavior at runtime.
Wiz Defend uses sensors to detect suspicious activity in cloud workloads. Cymulate validates these detections by running EDR-style scenarios against cloud-based systems, including Windows-based workloads protected by Wiz Defend sensors. These workloads run in the cloud and behave like applications, not traditional endpoints. Cymulate accounts for this by triggering behaviors aligned with Wiz Defend’s high- and critical-severity detection logic.
These scenarios validate:
- Wiz Defend sensors detect malicious runtime activity
- Correct detection rules are triggered
- Alerts and logs are generated as expected
This provides teams with confidence that real attacker techniques would be detected in production cloud workloads.
Example EDR/CWPP scenario: Enumerating Registry Passwords
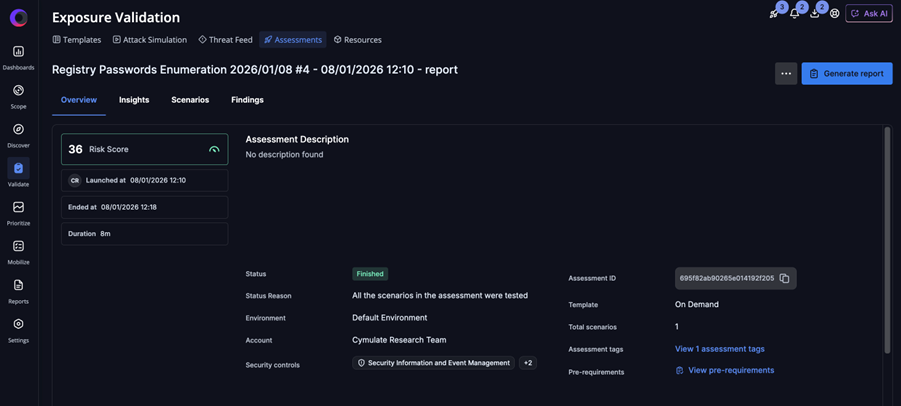
Assessment overview
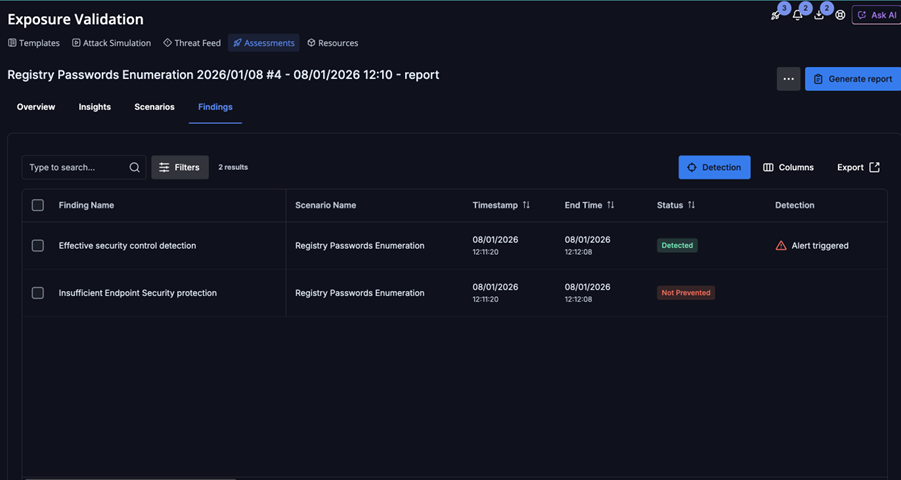
Assessment findings
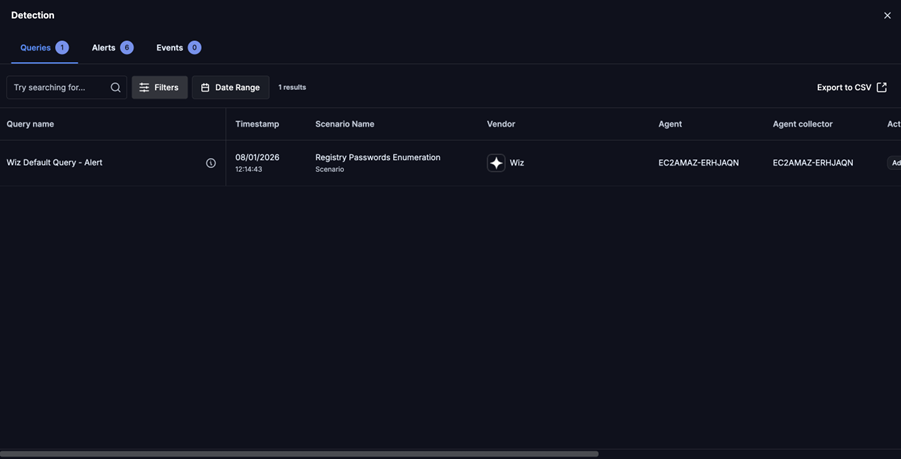
Assessment detection findings
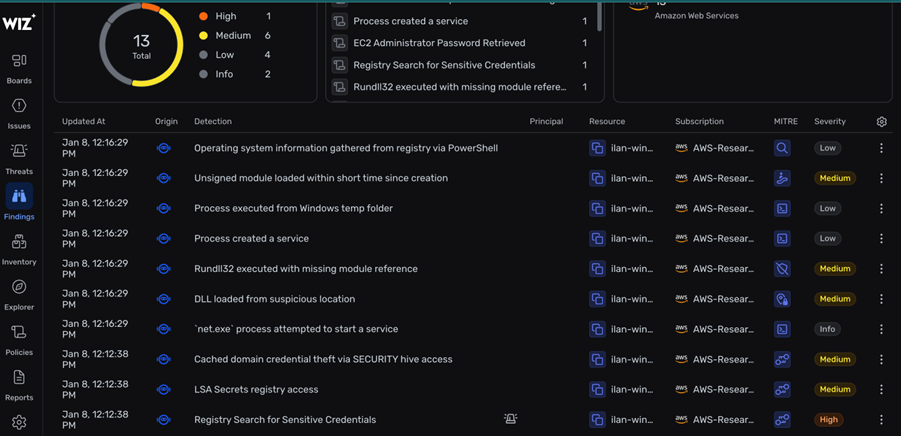
Wiz detection findings
2. Cloud detection and response (CDR) scenarios
The second scenario type focuses on cloud control activity, situations where something risky or malicious has already occurred in cloud services.
Examples include disabling audit logging, modifying security-sensitive cloud services, or changing configurations that weaken monitoring. In these cases, detection depends on cloud logs rather than sensors.
Cymulate simulates these actions and validates:
- Wiz detection of the resulting cloud events
- Logs are ingested and correlated correctly
- Alerts trigger when expected
Because these scenarios are log-driven, there is limited opportunity for prevention. Detection accuracy and timeliness are therefore critical. Cymulate confirms that Wiz Defend provides visibility when cloud activity crosses a security threshold.
Example of CDR scenario: Unusual Creation of an IAM Policy Using PassRole
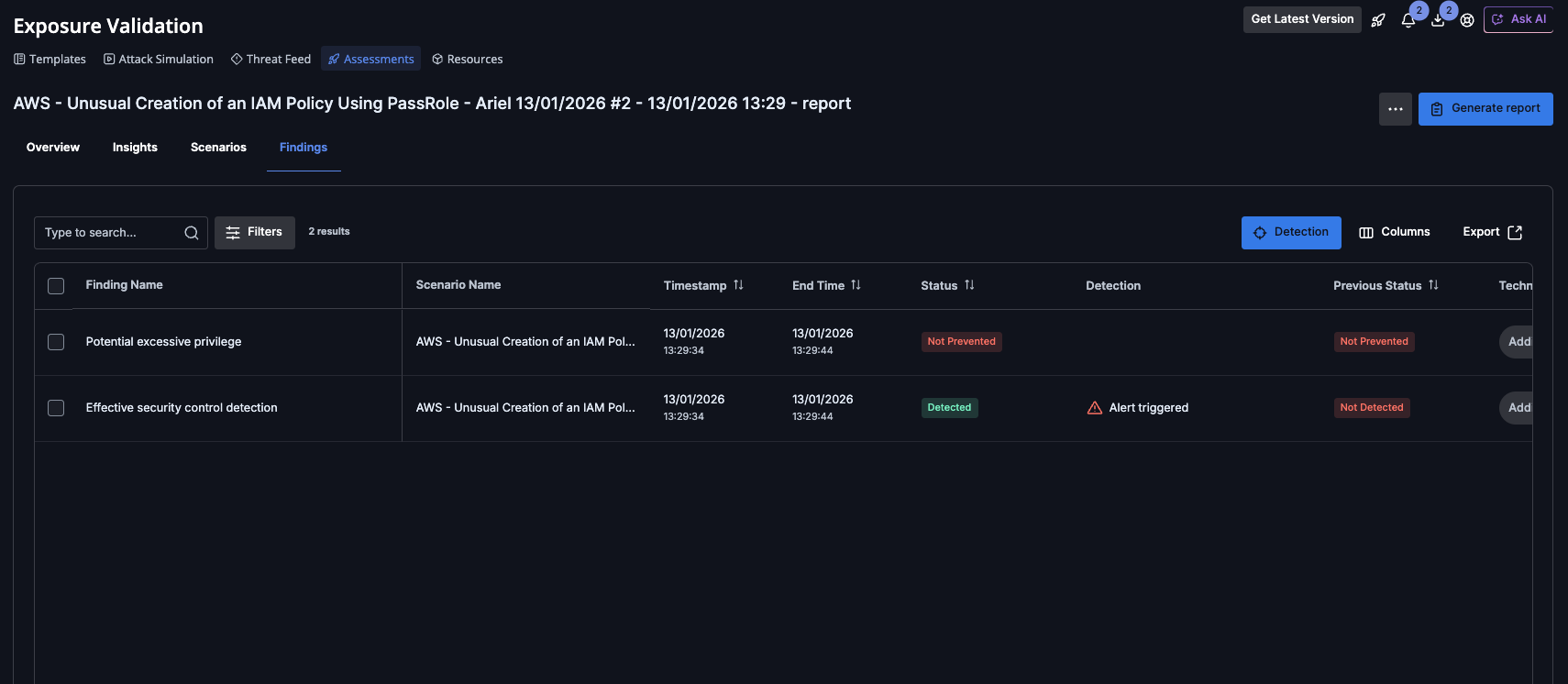
Assessment findings
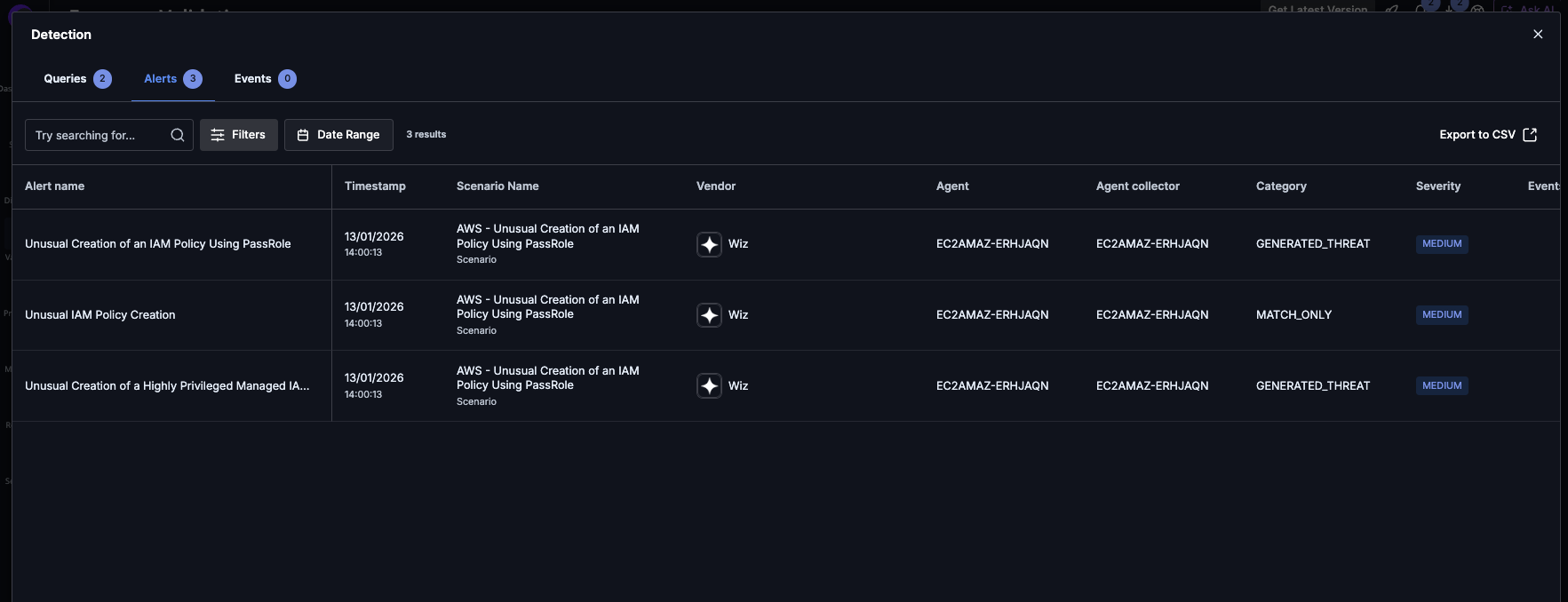
Assessment detection findings
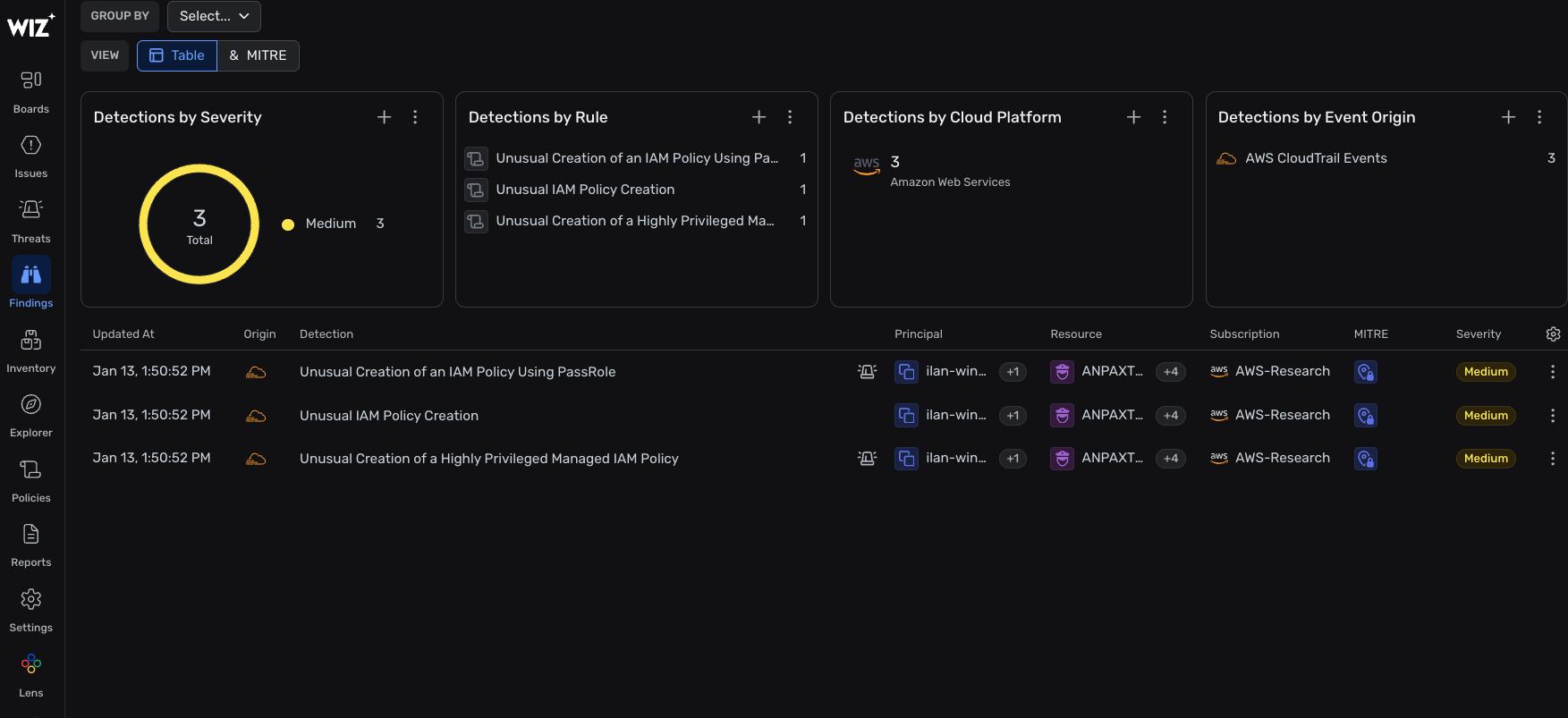
Wiz detection findings
3. Assume breach and posture-based scenarios
The third scenario type operates under an assume breach model and focuses on dangerous cloud posture conditions.
These scenarios simulate situations where:
- An attacker intentionally weakens cloud security
- An internal user creates an exposed or misconfigured resource
While Wiz identifies these risks through posture assessments, posture scans often run on longer intervals. Cymulate validates what happens at the moment risk is introduced, not hours later.
In these scenarios, Cymulate:
- Creates a risky cloud resource or configuration
- Verifies whether Wiz detects the exposure through logs or alerts
- Cleans up the resource after validation
This allows teams to safely test how well internal negligence or attacker-driven posture changes are detected in near real time.
Example of assume breach scenario: Turning off CloudTrail
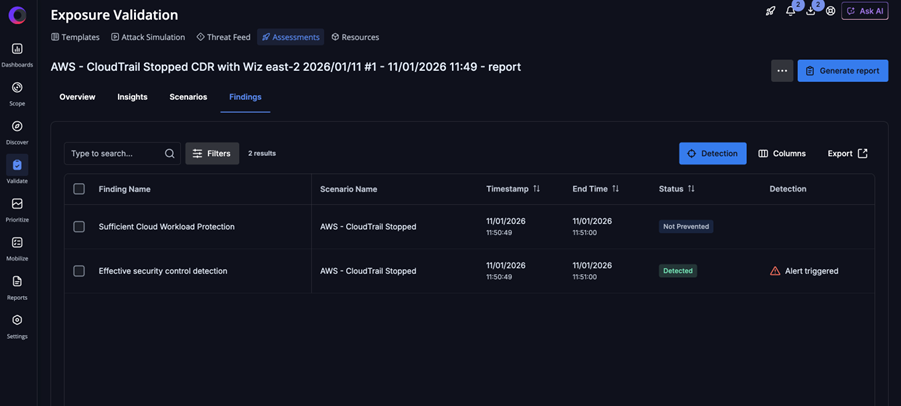
Assessment findings
From visibility to verified detection
Cloud environments are constantly changing, and detection logic must evolve just as quickly. The Cymulate–Wiz integration helps security teams validate that Wiz Defend detections work as intended, across runtime threats, cloud events and posture-driven risks.
Instead of relying on assumptions, teams gain concrete evidence of detection coverage and a clear path to improvement. That is what turns cloud visibility into operational resilience.
Already a Cymulate customer?
If you’re using Wiz, you can get started right away by using the Ask AI feature in the Cymulate Platform for step-by-step guidance on enabling the integration and validating Wiz detections. If you’d like additional support, your account manager is available to answer setup questions, address supported scenarios and share best practices for your environment.
Evaluating Cymulate or Wiz?
If you’d like to see how the Cymulate–Wiz integration works in practice, request a demo to explore how automated attack simulations validate Wiz Defend detections and accelerate cloud detection engineering.