Prove the threat. Improve resilience.
Context is everything.
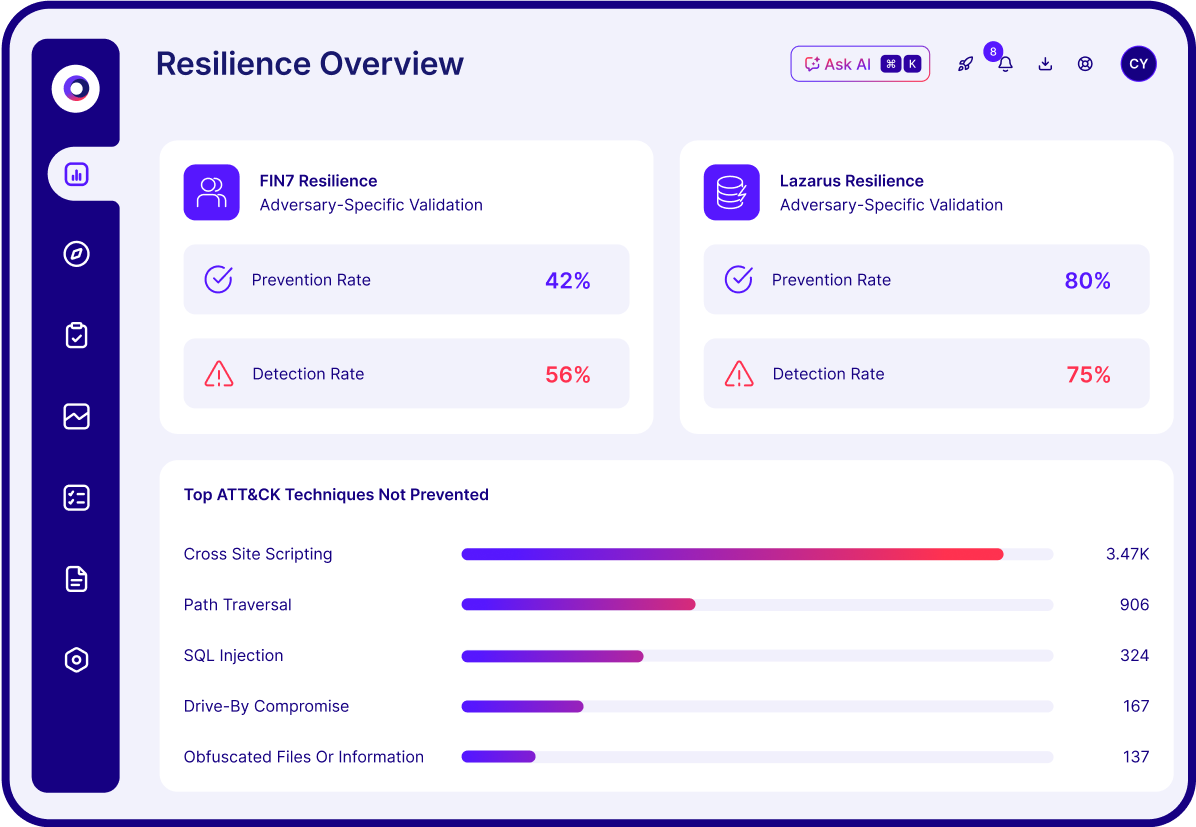
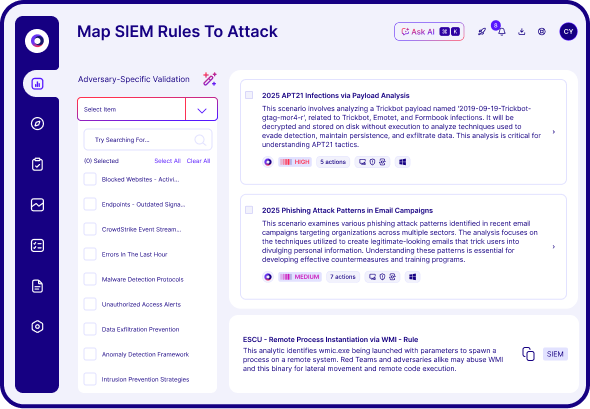
Your business is unique — so why make security decisions based on theoretical risk? With Cymulate, it's easy to cut through the noise. Test and prioritize what can be exploited in your environment, across the entire MITRE ATT&CK framework and thousands of threat scenarios.
Cyber threat resilience is now a business imperative.
of businesses paid ransom last year
DESPITE 'NO PAY' POLICIES
struggled to win customers post-breach
Double the 2023 rate
to restore operations post-attack
6X slower than target
of boards view cyber threats as strategic
DRIVING EXECUTIVE CONCERN
Know what can happen — and get ahead of it
Key benefits to your organization
Real CTEM starts with real validation.
Adding proof of exploitability to your exposure data leads to smarter, faster and more efficient security outcomes.
Accurate Focus
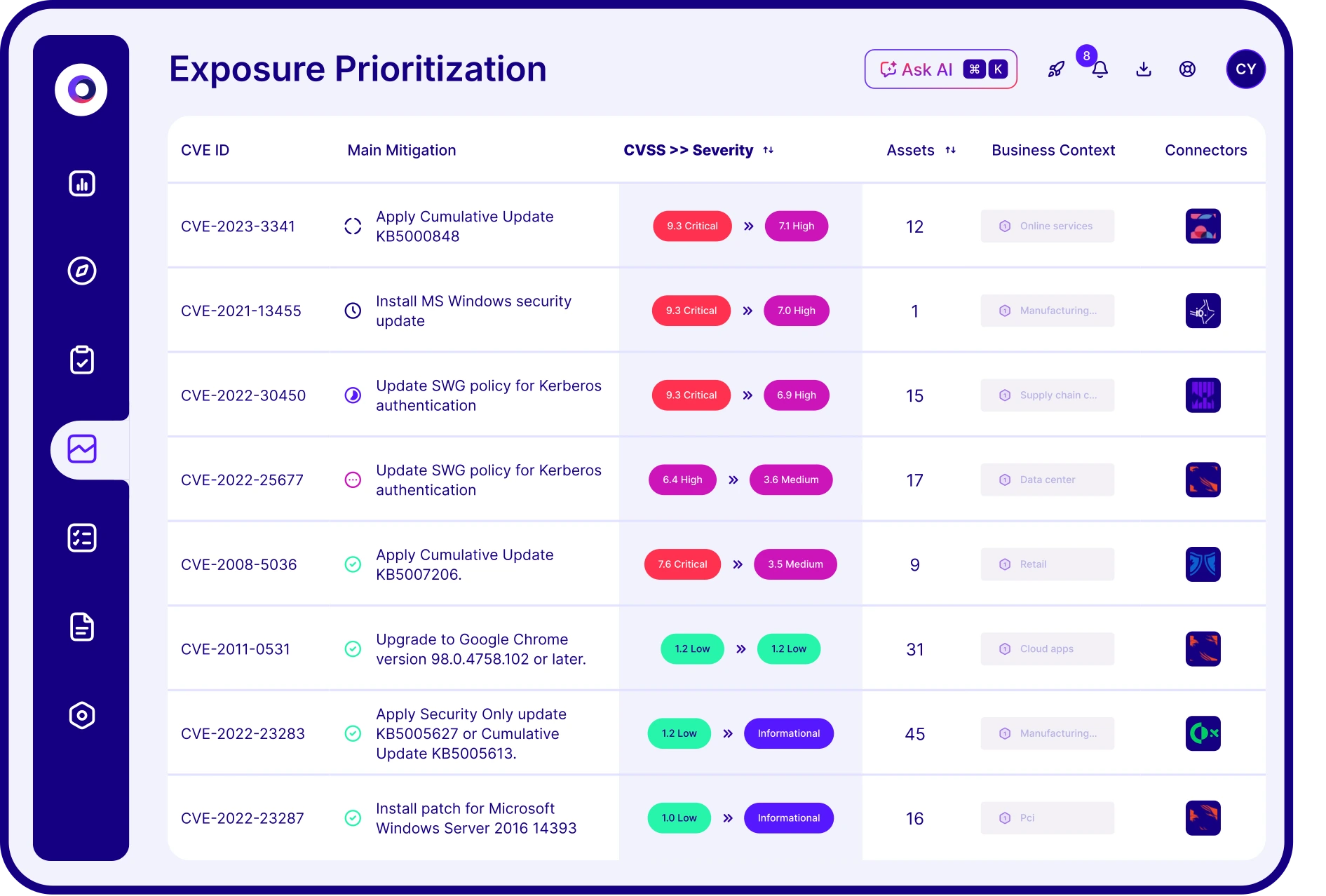
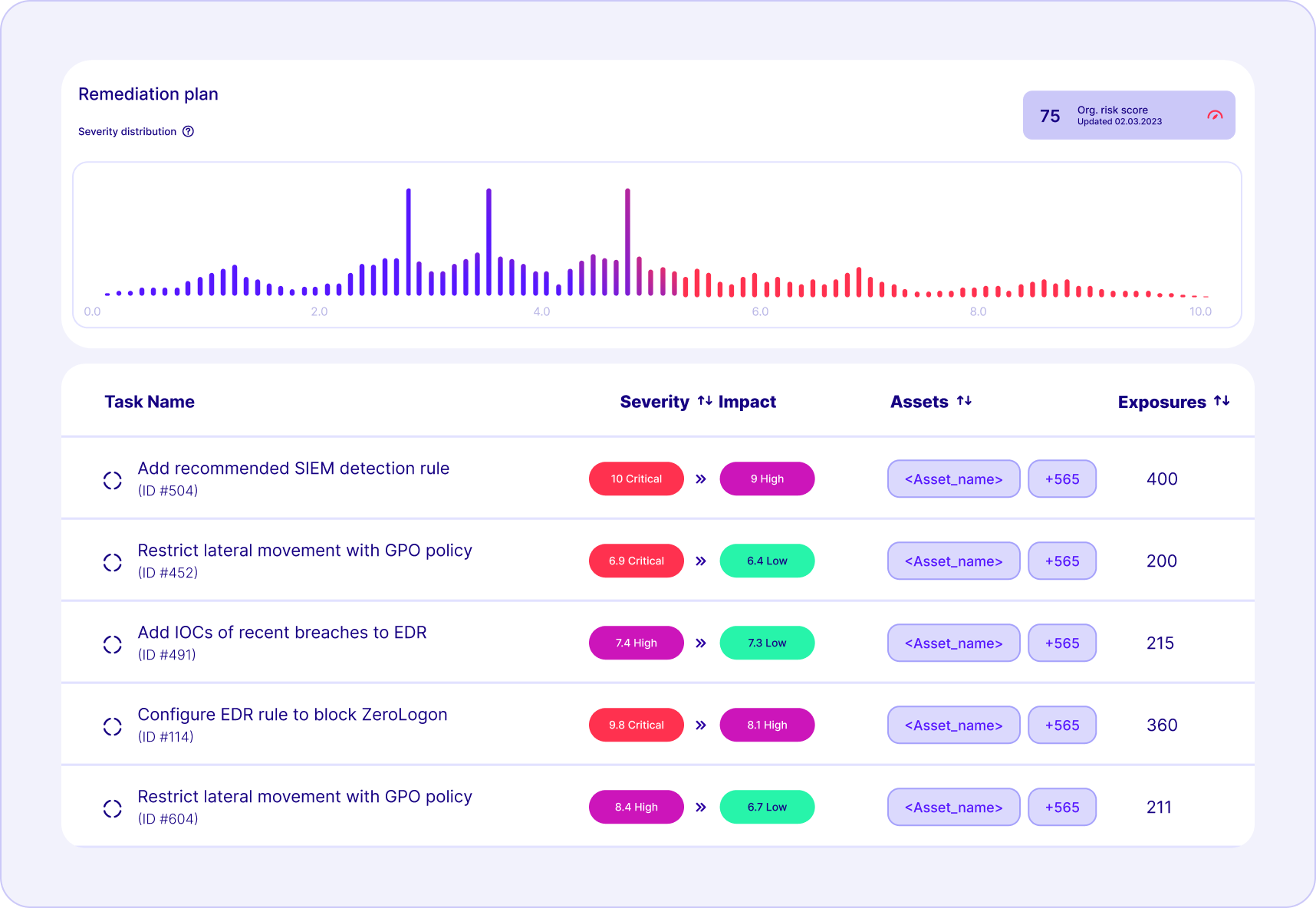
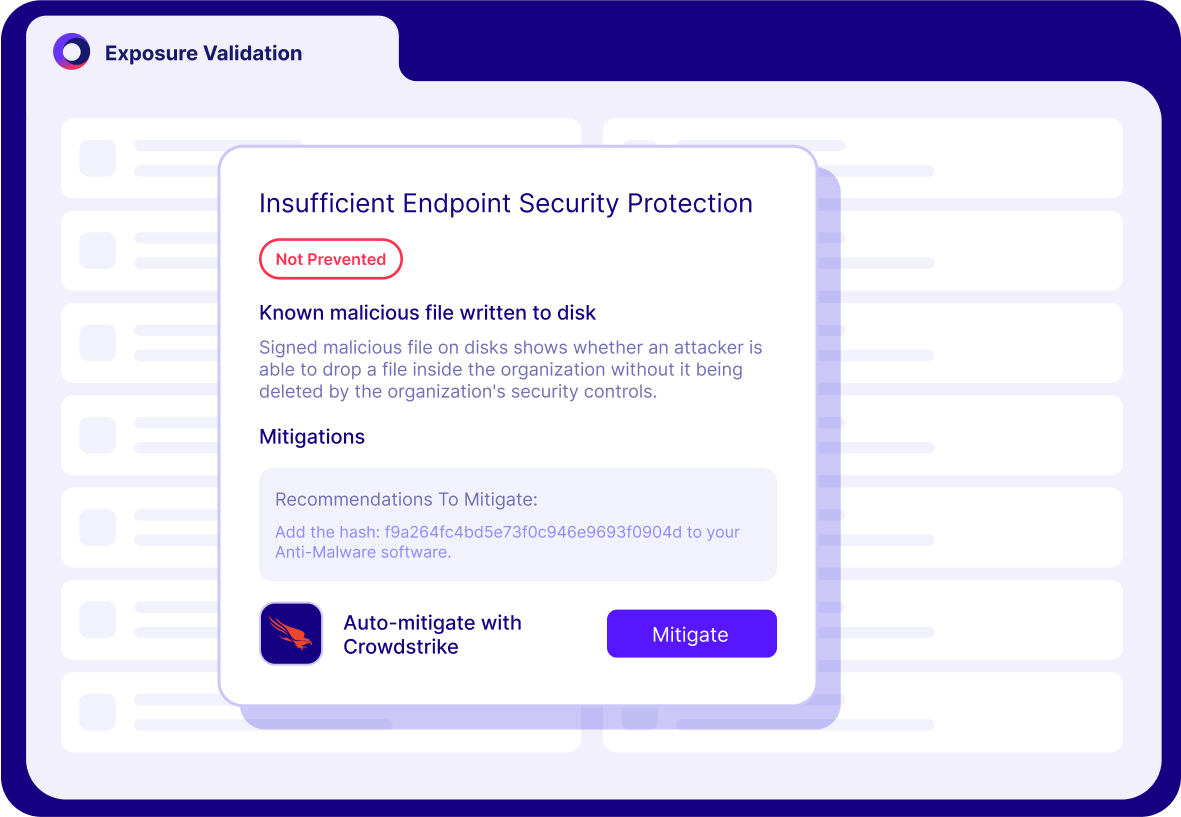
Prioritize remediation on vulnerabilities that are actively targeted and exploitable, ignoring the noise.
Impactful Decisions
Move from asset-centric to impact-centric prioritization, aligning security with business risk.
Accelerated Remediation
Reduce time and costs by fixing fewer, higher-impact issues with product-specific mitigation advice and semi/automatic delivery.
DRIVE REAL ROI
Results You Can Expect
40X
Faster threat validation, from days to hours
85%
Improvement in threat detection accuracy
24/7
Continuous security posture monitoring
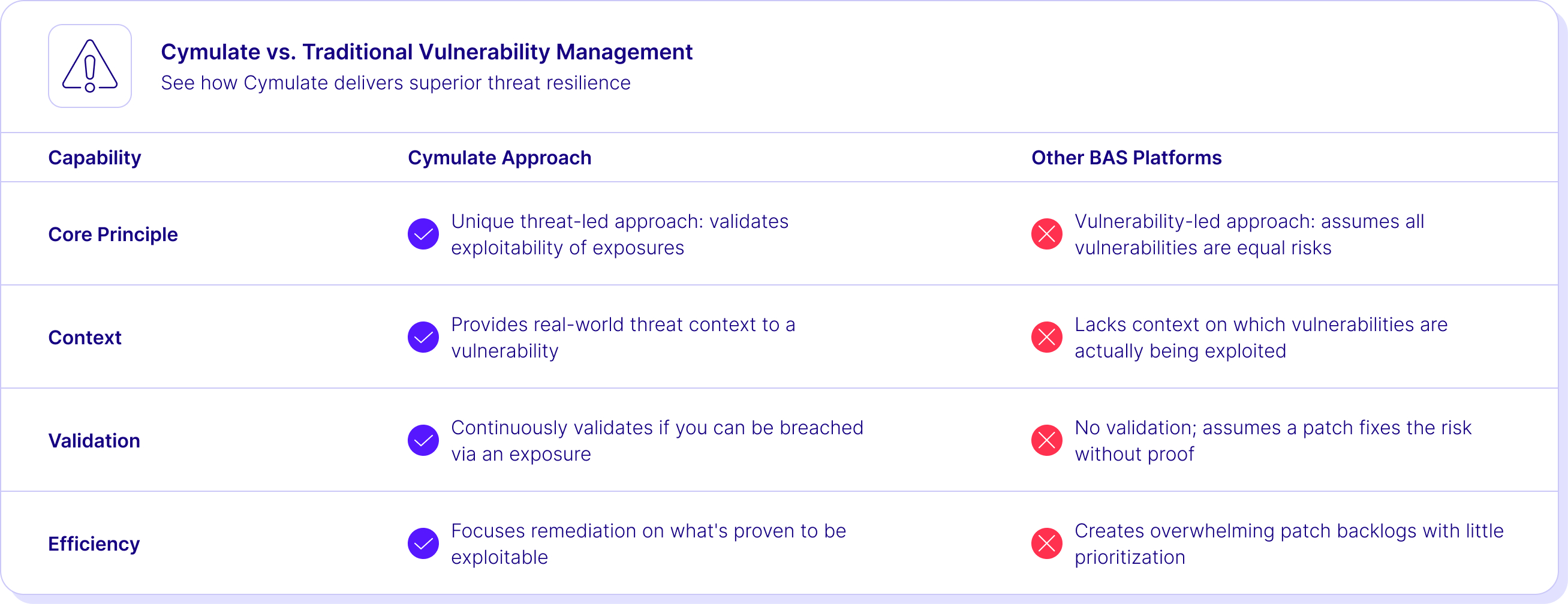
HOW WE'RE DIFFERENT
The Cymulate Advantage
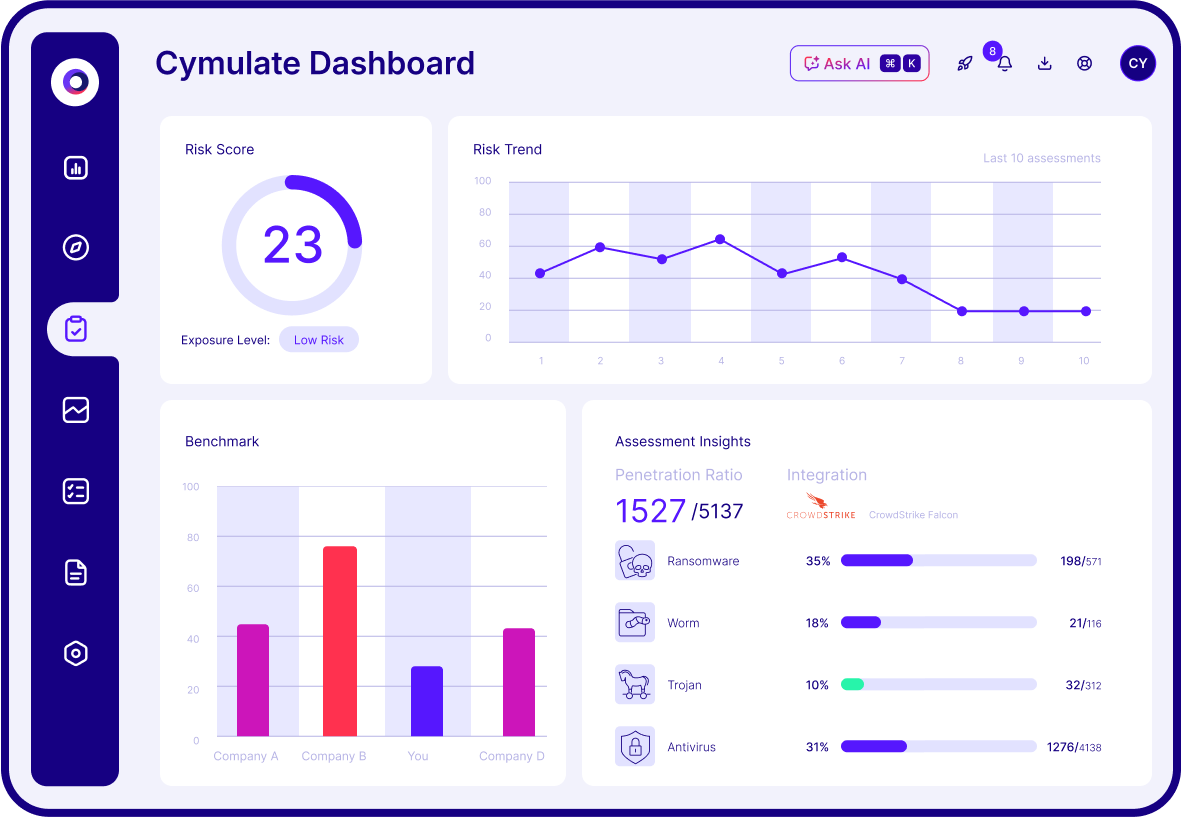
Continuous Threat Validation
24/7 automated attack simulation to validate your security posture in real-time
AI-Powered Optimization
Machine learning algorithms provide actionable insights for security improvement
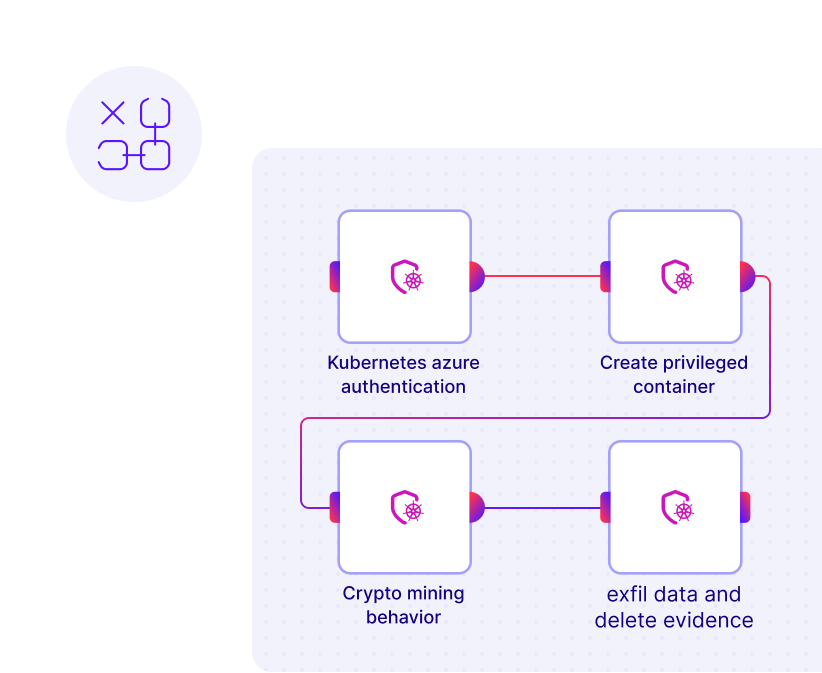
Complete Kill Chain Coverage
Full attack lifecycle simulation from initial access to data exfiltration
WHY CYMULATE?
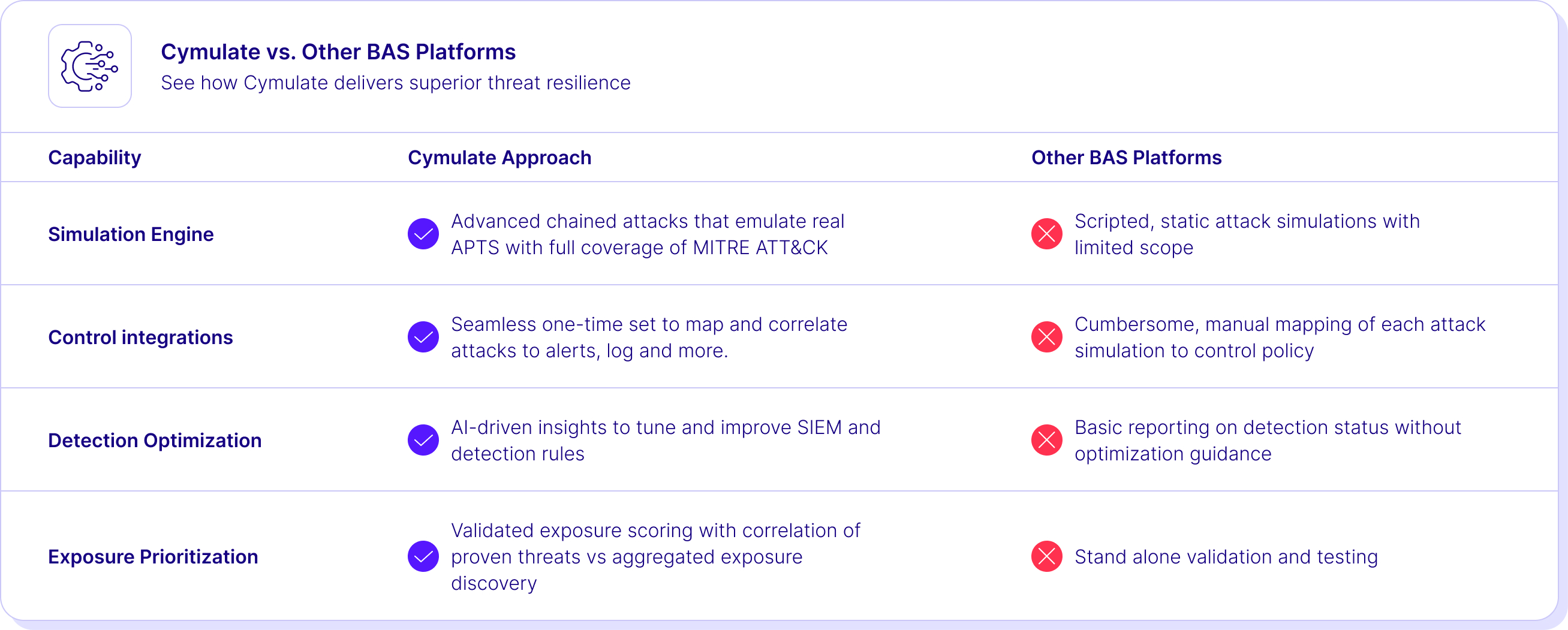
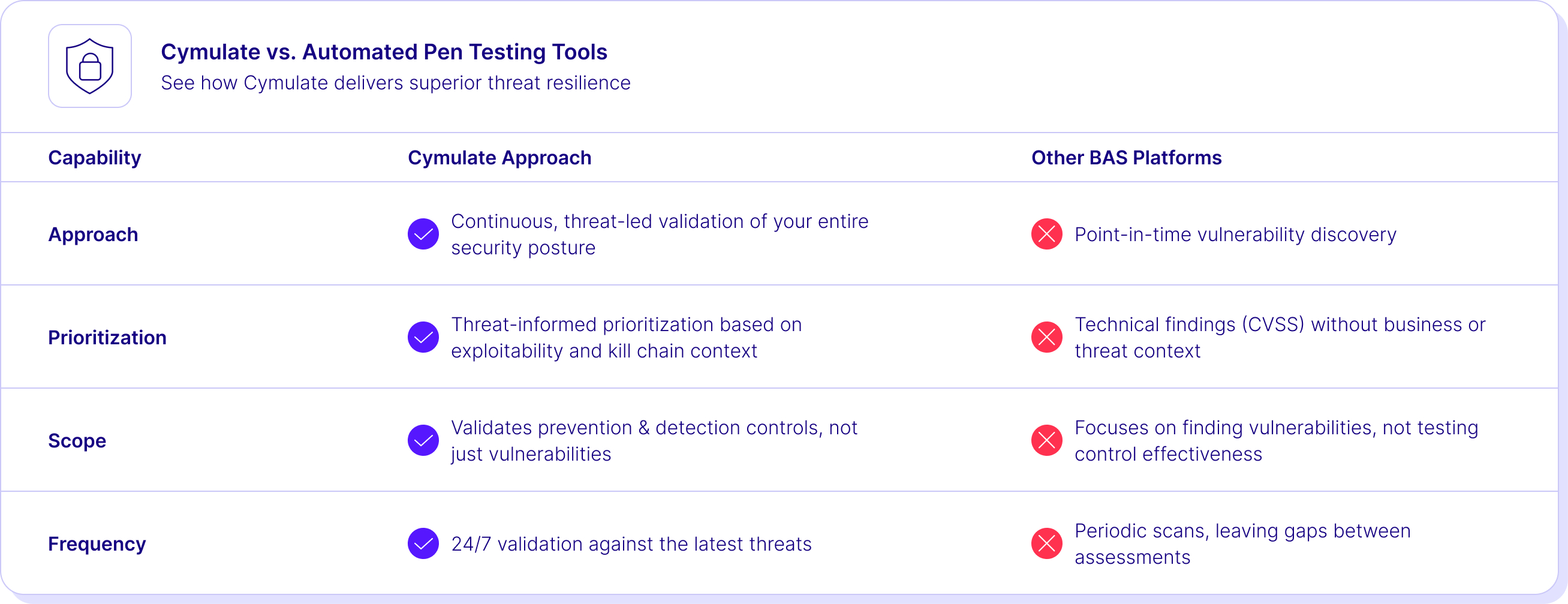
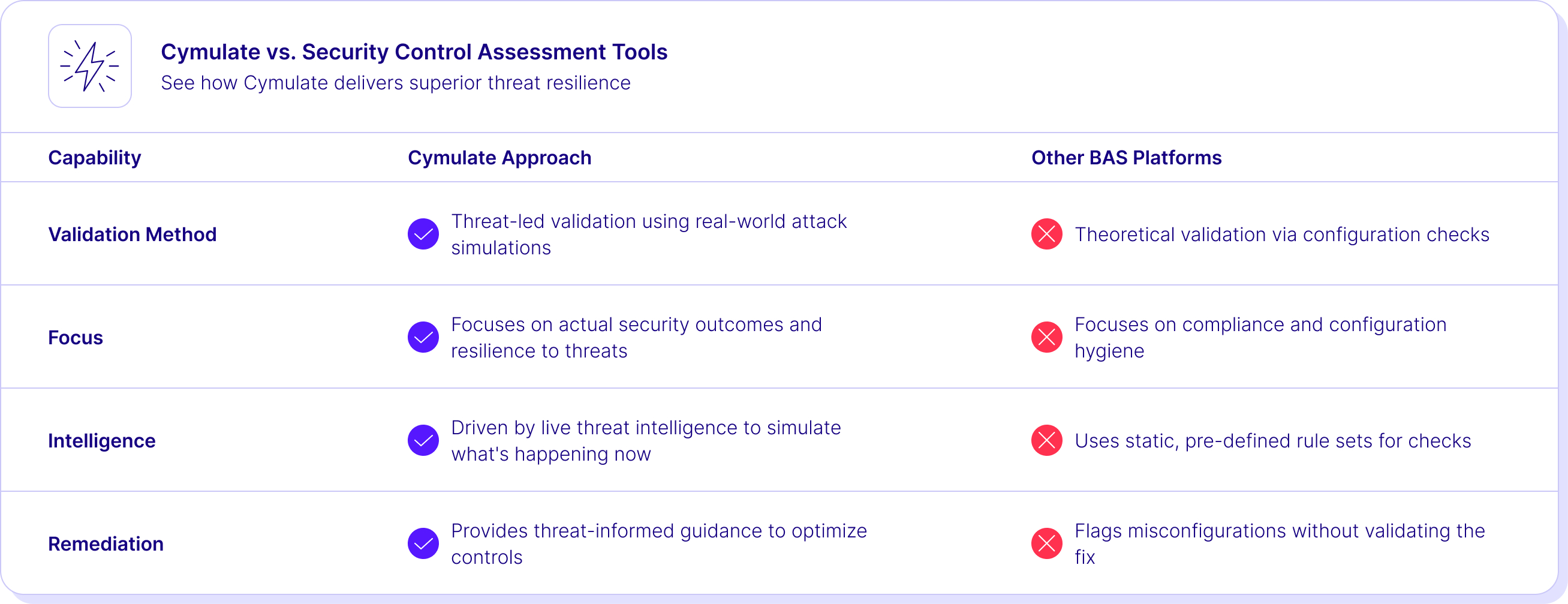
Compare Us to the Alternative
SEE WHAT THE BUZZ IS ABOUT