Exploiting BadSuccessor: Cymulate Launches New Advanced Breach Simulation Scenario
At Cymulate, our mission is to stay ahead of evolving threats by transforming cutting-edge research into real-world security testing tools.
Today, we're excited to unveil a new breach simulation scenario that automates the detection and exploitation of BadSuccessor, a powerful Active Directory (AD) privilege escalation technique discovered by Yuval Gordon, Security Researcher at Akamai.
This simulation enables security teams to proactively test their environment against a threat vector that’s already been found to affect a staggering number of real-world AD deployments.
Check out Gordon’s full original research at the link above for a deeper dive into the technical underpinnings of the exploit.
What Is BadSuccessor?
BadSuccessor is an Active Directory vulnerability tied to Delegated Managed Service Accounts (dMSAs), a feature newly introduced in Windows Server 2025. The flaw stems from how AD processes dMSA migrations, allowing an attacker to simulate a migration process and gain the privileges of virtually any user in the domain, including Domain Admins.
The Attack Mechanism
The exploitation relies on manipulating two key AD attributes:
msDS-ManagedAccountPrecededByLink
msDS-DelegatedMSAState By creating a rogue dMSA and setting these attributes, an attacker tricks the Key Distribution Center (KDC) into generating a Privilege Attribute Certificate (PAC) that includes the SIDs and group memberships of the “superseded” account, which could be the Administrator itself.
This means an attacker with only OU-level permissions can escalate privileges dramatically, without needing access to privileged credentials.
What Cymulate Built
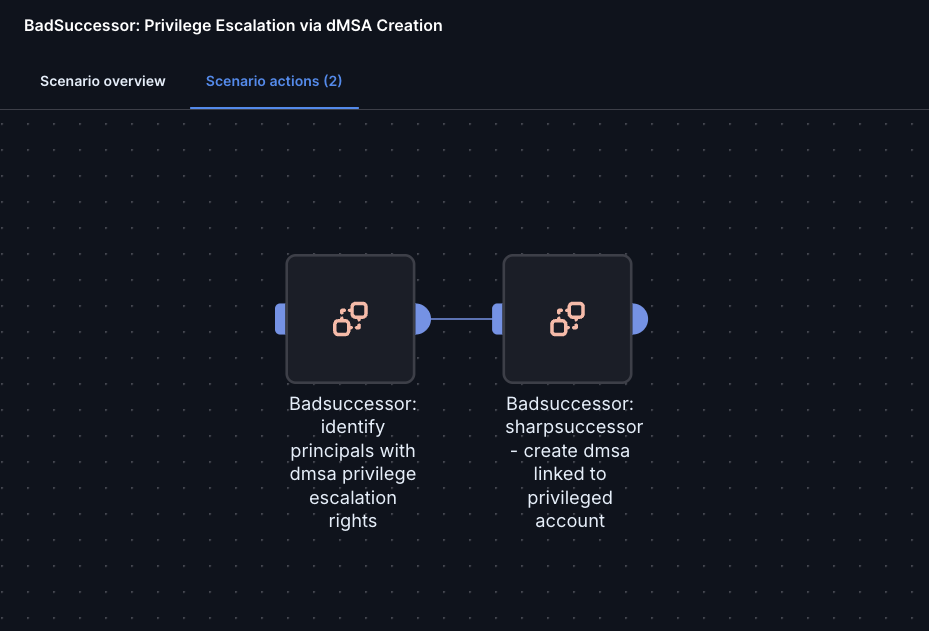
To empower organizations to test their defenses against this novel attack, Cymulate has developed a fully automated BadSuccessor Breach Simulation Scenario. This scenario mimics an attacker’s steps using real-world tactics and tools - all in a safe, controlled environment.
The Scenario Includes:
- Discovery Phase: Scans Active Directory to locate Organizational Units (OUs) where low-privileged users have CreateChild, GenericAll or similar over-permissive rights.
- Enumeration & Validation: Filters potential targets based on known exploitation criteria (as outlined in Akamai’s research).
- Exploitation: Uses SharpSuccessor, a publicly available PoC, to craft a rogue dMSA and perform the privilege escalation chain.
Who’s at Risk of BadSuccessor?
According to Akamai’s data:
“In 91% of the environments we examined, we found users outside the domain admins group that had the required permissions to perform this attack.” - Yuval Gordon, Akamai
You’re likely vulnerable if:
- Your environment includes at least one Windows Server 2025 Domain Controller.
- You’ve delegated OU permissions (e.g., to Helpdesk, DevOps, or Automation accounts).
- You allow unrestricted dMSA creation in AD.
How to Detect and Mitigate BadSuccessor
Detection Strategies
To detect exploitation attempts, enable auditing for the following:
- Event ID 5137 – Creation of msDS-DelegatedManagedServiceAccount objects.
- Event ID 5136 – Modifications to msDS-ManagedAccountPrecededByLink
- Event ID 2946 – Authentication events involving dMSAs (in Directory Service log).
Mitigation Best Practices
Until Microsoft releases an official patch, reduce your exposure with these steps:
- Restrict permissions like CreateChild and GenericAll across all OUs.
- Limit dMSA creation rights to essential service accounts only.
- Use BloodHound, PowerView, or other AD ACL analysis tools to audit and fix overly permissive configurations.
Why BadSuccessor Matters
BadSuccessor is not just theoretical - it's dangerously easy to exploit. With minimal permissions, attackers can:
- Escalate to Domain Admin level access.
- Inherit privileged group memberships and SPNs.
- Steal Kerberos keys from target users, especially if RC4 encryption is enabled.
By integrating this scenario into the Cymulate platform, organizations can simulate the exact kill chain, identify weak points and act before attackers do.
Test Your Defenses Now
Want to know if your environment is vulnerable to BadSuccessor? Simulate the threat safely with Cymulate’s BadSuccessor Breach Simulation Scenario - now available on our platform.