Cyber Risk Remediation Starts with Validation: Controls, Threats and Response

Key Takeaways
- Cyber risk remediation is only effective when risks are validated and prioritized, not treated equally.
- Most organizations waste resources on patching exposures that are not exploitable in their environment.
- Validation bridges the gap between risk identification and meaningful risk reduction.
- Prioritization and automated remediation accelerate response while conserving limited resources.
- The Cymulate Exposure Management Platform delivers continuous validation and automated mitigation to close the loop on cyber risk remediation.
The Cyber Risk Challenge
Attack surfaces are expanding faster than security teams can keep up. Cloud workloads, SaaS, third-party dependencies and distributed workforces create layers of complexity that attackers exploit. At the same time, defenders face limited staff, shrinking budgets and a nonstop stream of vulnerabilities. Traditional patch cycles and manual prioritization approach can’t possibly keep up with the speed of today’s landscape.
Effective cyber risk remediation requires more than identifying exposures. It demands validation of which risks actually matter, followed by fast, precise action to remediate them. Otherwise remediation becomes guesswork. That’s how organizations can become both exposed and resource-constrained.
What is Cyber Risk Remediation?
Cyber risk remediation is the process of closing the loop on identified risks by validating, prioritizing and applying the right corrective actions. It differs from risk management, which defines policies and frameworks at a higher level. Remediation is the operational layer; that’s the work of reducing the attack surface and neutralizing active threats.
Core components include:
Identification: Discovering vulnerabilities, misconfigurations and security control gaps.
Prioritization: Determining which issues pose the highest risk based on exploitability and business impact.
Response: Applying patches, configuration changes or compensating controls to eliminate or reduce exposure.
Where traditional approaches stop at identification, true remediation ensures exposures are validated and resolved, not just logged.
The Challenges of Cyber Risk Remediation
Most organizations struggle to remediate effectively for a number of reasons. This can include:
- Volume of exposures: Modern environments generate thousands of alerts and vulnerabilities daily.
- Lack of context: CVSS scores and scanner outputs rarely indicate whether a vulnerability is exploitable in a given environment.
- Resource constraints: Teams have limited staff and time to triage, patch and test fixes.
- Patch fatigue: Endless cycles of updates and alerts create burnout and lead to missed critical risks.
The challenges mean teams often remediate low-risk vulnerabilities while leaving high-impact ones unaddressed.
Why Validation is the First Step
Validation separates noise from real risk. By testing whether a vulnerability, misconfiguration or control gap is actually exploitable, security teams gain the context needed to prioritize remediation intelligently.
For example, the Cymulate Exposure Management Platform continuously validates security controls against real-world threats and exposures. Only a fraction of identified vulnerabilities are truly exploitable in context, underscoring why validation must precede remediation.
Without validation and exposure prioritization, teams waste effort on exposures that attackers can’t exploit, while true risks remain open and susceptible.
Prioritization and Risk Reduction in Practice
Once validation identifies exploitable risks, the next step is prioritization. Effective cyber risk remediation follows a structured approach:
- Validate exposures: Confirm whether a vulnerability or misconfiguration is exploitable.
- Prioritize by impact: Rank issues based on attack feasibility, business impact and control coverage.
- Remediate efficiently: Apply the least disruptive but most effective fix, whether patching, reconfiguring or applying a compensating control.
Going through this process ensures that scarce resources deliver measurable risk reduction, not just busy work.
Prioritization and remediation from Cymulate helps security teams operationalize this process, aligning technical remediation with business risk.
From Manual to Automated Remediation
Traditional remediation is generally manual, slow and prone to error. Analysts must review scanner outputs, cross-reference threat intelligence, assign priorities and coordinate patches or fixes with IT teams. This delay creates windows of opportunities for attackers.
Automation changes the equation. Automated Mitigation from Cymulate accelerate remediation by:
- Applying temporary compensating controls until patches are available.
- Automating configuration fixes and playbooks.
- Orchestrating prioritized patching with IT operations tools.
This approach compresses response times, ensuring exploitable exposures are closed before attackers can exploit them.
The Role of Exposure Management in Cyber Risk Remediation
Traditional vulnerability management identifies risks but leaves remediation slow and incomplete. Exposure management goes further, combining continuous validation, business-context prioritization and automated remediation.
With the Cymulate Exposure Management Platform, organizations can:
- Continuously validate whether controls block current threats.
- Prioritize remediation based on exploitability and impact.
- Automate mitigation to shrink response times
- Measure and demonstrate risk reduction to stakeholders.
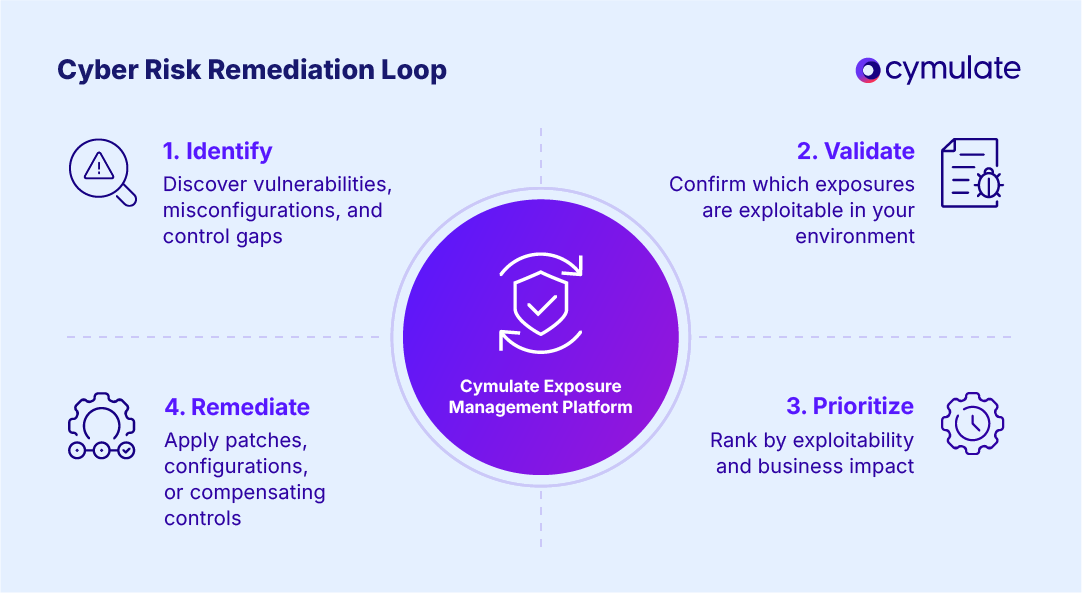
The result is a closed-loop remediation process that reduces the attack surface, accelerates security outcomes and makes the best use of limited resources.
Cymulate performs automated attack simulations that test real-world exploitability of identified exposures. It correlates data from vulnerability scanners with threat prevention and detection outcomes to provide proof of resilience against specific threats.
While CVSS scores indicate severity, they do not exploitability. Cymulate helps security teams move beyond static scoring by validating which exposures are actively exploitable — enabling more effective and efficient remediation.
The platform integrates with vulnerability scanners, IT asset management and other security tools to aggregate exposures, validate them through simulation and provide a unified risk-based prioritization view.
Cymulate customers have seen a 52% reduction in critical exposures by focusing remediation on exposures with proof of exploitability and effective mitigation strategies.
Here’s what one customer had to say recently:
"Cymulate stands out in cybersecurity with its comprehensive exposure management and intuitive user interface for security posture assessments. On the detection engineering side, it helps improve operational efficiency by minimizing analysis time, making it ideal for organizations pursuing proactive, robust and adaptive cybersecurity frameworks."
- Markus Flatscher, Junior Manager, Security, Raiffeisen Bank International AG
Closing the Loop with Cymulate
Cyber risk remediation built on identification alone leads to wasted time and incomplete protection. Validation, prioritization and automation transform remediation into a strategic advantage, eliminating noise, focusing resources and reducing risk further.
The Cymulate Exposure Management platform operationalizes this approach, enabling teams to remediate based on validated exposures, automate mitigation steps and deliver measurable security outcomes.