Facts from Cyber Threat Frontlines: Cymulate Threat Research Updates
In a world flooded with cybersecurity podcasts, the Cymulate Threat Research Update webinar series stands apart. It dives into the pulse of cybersecurity, uncovering the most burning trends and threats. Beyond mere reporting, the Threat Research Update offers fresh and insightful perspectives from seasoned experts and provides actionable recommendations.
Last Spotlight: Unmasking MOVEit
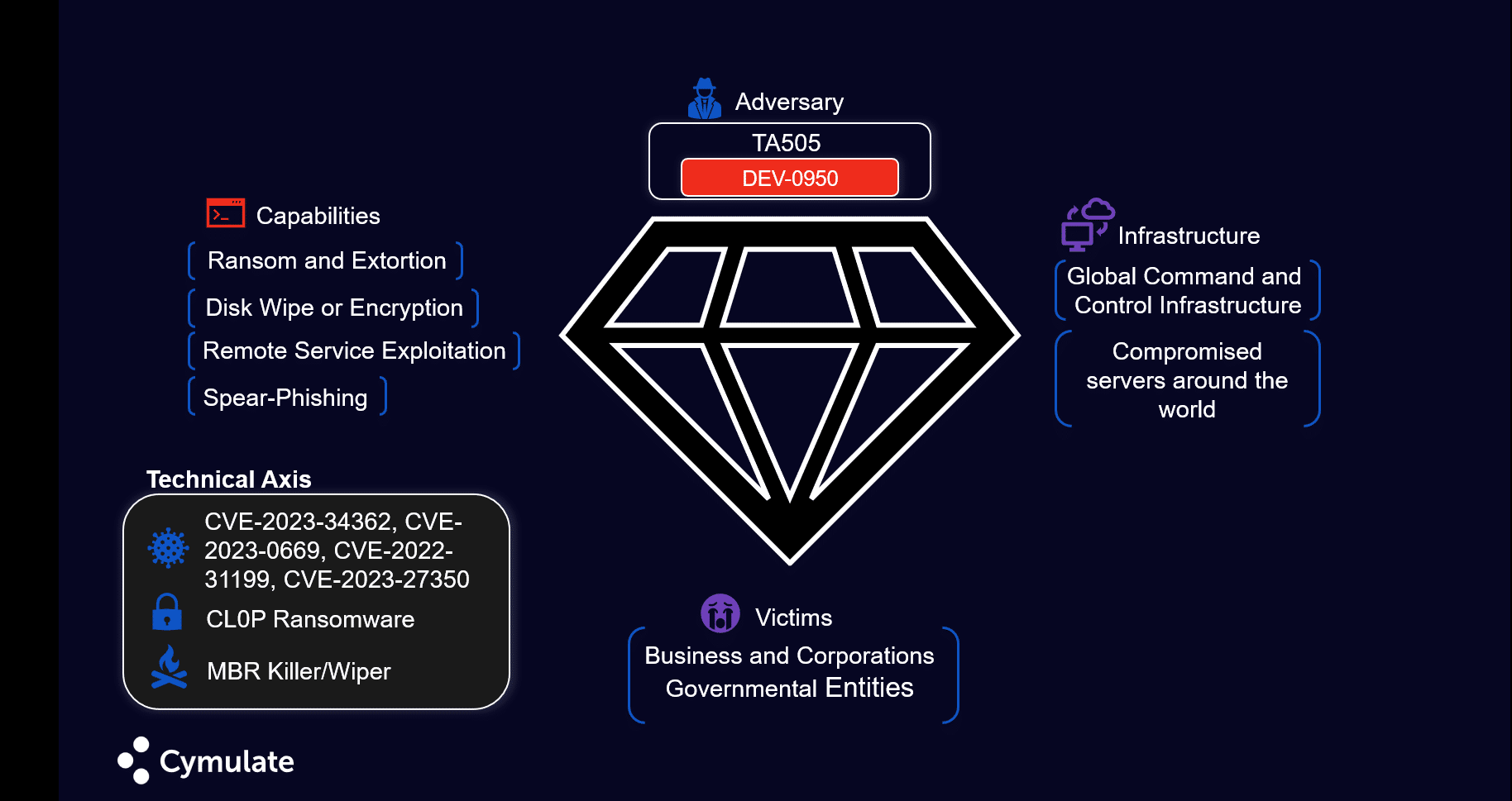
The last Cymulate Threat Research Update episode was a deep dive into the world of ransomware. It focused on MOVEit Transfer 0-day (CVE-2023-34362) and GoAnywhere MFT, unraveling the tactics and motives of the notorious threat actor CIop, linked with Lace Tempest, who unleashed the CL0P ransomware on specific targets.
A Closer Look at the Threat Landscape
- The Intrusion Phases: A dissection of the attack, step by step, to understand how it unfolded.
- Threat Actor Profile: Painting a vivid picture of CIop, exploring the ransomware gang, what drives them, and how they choose their victims.
- Attack Analysis: A meticulous examination of the attack and the cunning techniques used, offering a rare glimpse into the attacker's mind.
- The Cymulate Approach: An inside look at detection methods and Cymulate threat research team replicated the attack to proactively block it.
- Expert Recommendations: Actionable insights and expert recommendations for future action, equipping listeners with tools and techniques to stay ahead of similar threats.
What Set That Latest Threat Research Update Apart?
While many podcasts settle on either defense (blue team) or offense (red team), understanding today's dynamic cybersecurity interactions demands a more comprehensive approach. That webinar blended both perspectives, offering a comprehensive view of emerging threats, APT activity, and overall cybersecurity challenges.
Meet the Experts
- Dan Lisichkin, a threat researcher with daily hands-on interactions with emerging threats, brought the blue team's wisdom.
- Mike DeNapoli, a Cybersecurity Architect and Analyst, offered deep insights from the red team's angle and provided actionable guidance on finding proactive solutions to shore up defenses.

Together, they break down threats and share methods for a robust defense-in-depth strategy, providing a balanced and nuanced view that is rare in the industry. Blending red and blue perspectives into a single podcast presents not only offers a breakdown of the threat discussed but also provides methods and techniques that can be used to defend the organization at multiple levels of a defense-in-depth strategy.
Why It Matters?
Shaping a resilient cybersecurity strategy demands understanding both sides of the coin. This Threat Research Update's unique blend of blue and red team insights offers an extensive depiction, enabling the development and implementation of effective and resilient strategies.
In addition, it equips viewers with the resources to detect and prevent threats effectively.
Bonus Insights
Dan and Mike broached real-world challenges and topics deriving from cybersecurity, such as business disruptions, budget constraints, and legacy systems, expanding the focus from what to do to why doing it is vital.



