How to Run Threat Intelligence Analysis and Malware Research (Without Spending a Dime)
In this post, I will walk you step-by-step through techniques that will enable you to run threat intelligence analysis and research malware without spending a dime.
Chapter Zero – Triggering My Inner Threat Intelligence Analyst and Malware Researcher Ego
I recently saw a blog post by Trend Micro in the Curated Intelligence Discord group. The blog post describes a rather interesting ransomware incident discovered by Trend Micro, in which, yet again, a legitimate driver was utilized to terminate security-related processes from the kernel space. I was curious, so I looked into the IoC index.

I decided to look up the IoCs in VirusTotal, but, unfortunately, the only hash listed in the VT database (at the time of writing) was the driver mhyprot2.sys.
As I am lucky enough to have access to a premium VTI account and was determined to provide the juicy hashes to my community, I started researching.
Quickly, I found more campaigns from the same ransomware actor as well as the tools and ransomware associated with the Trend Micro report. Even as I stroked my bloated ego (after all, I had just found all those missing hashes), I remembered the days when I was starting out with malware research and begging for samples.
And so, I decided to challenge myself to find and download all the missing samples and attempt to attribute the ransomware actor using just OSINT and free tools.
Let’s dive in.

Chapter One – Finding the Malware Samples
I first looked up the driver mhyprot2.sys hash (0466E90BF0E83B776CA8716E01D35A8A2E5F96D3) in a VirusTotal Community account and selected the relations tab (I avoided the community tab as the collections and comments were not at all helpful in this case.)
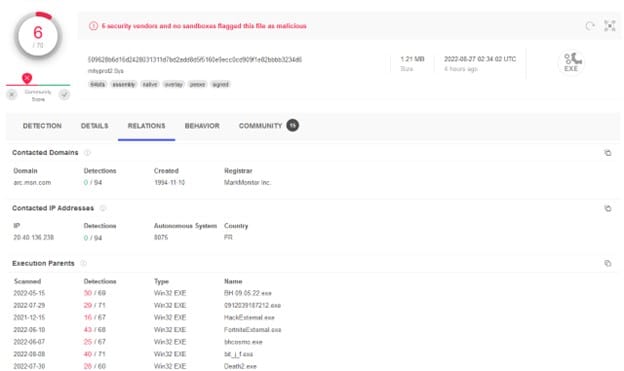
As it is a legitimate gaming driver, it has a lot of execution parents, and the drop-down list of execution parents is crazy long. However, we do have some clues to search for. From the report, we know that avg.msi and avg.exe are responsible for dropping the driver onto the disk:
I decided to keep dropping more files within the execution parents list, and, what do you know ?!
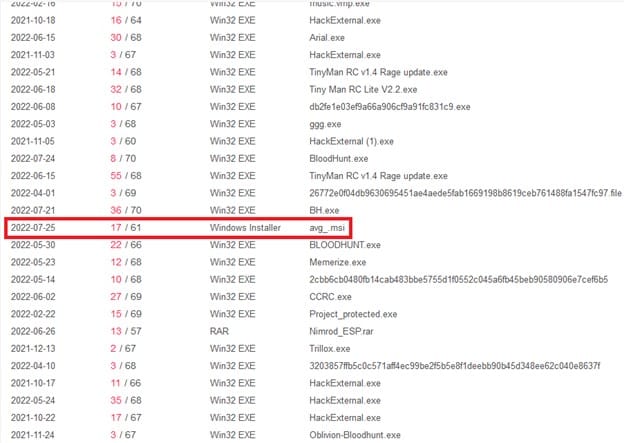
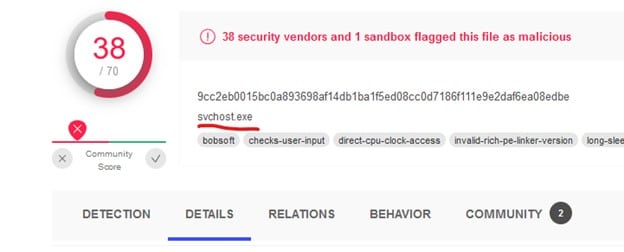
Interesting ... Let's see what this hash is about. I clicked the (MD5: b6373b520a21c2e354b805d85a45a92d ) file name and hit jackpot!
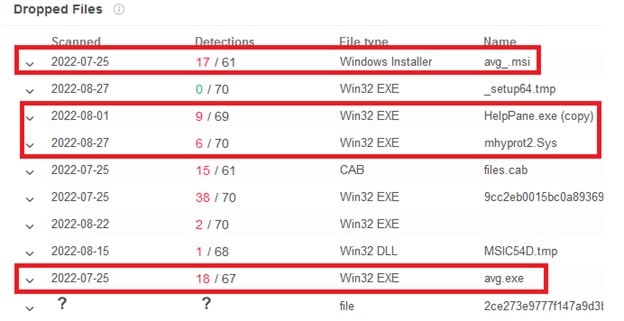
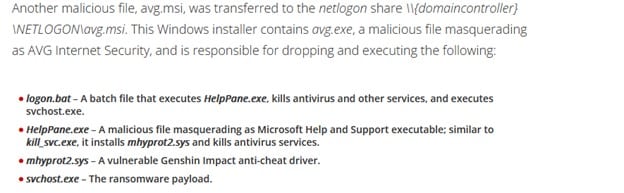
Two files were missing: the ransomware file itself, called svchost.exe, and logon.bat. The first was quite easy to find. Just by clicking the dropped files within the MSI, I found that VirusTotal displayed a misleading name for the ransomware file. Clicking on the 6th file (with the long hash name) got me transferred to the following sample (5143bbdf1f53248c7743f8634c0ddbc ).
Great! Now for the missing batch file and the ransomware note. The only way I could think of is to trigger the MSI installation on a sandbox like AnyRun. In theory, not only would I gain access to all the files, as AnyRun allows anyone who pleases to download files from their reports, but I would also gain access to the logon.bat file and the ransomware note, which could aid in attribution.
Chapter Two – Downloading the Malware Samples
Back in the day, I used open malware repositories or begged my researcher friends to use their VTI access and download samples for me. The latter will obviously hurt our fragile ego, so let's start looking up avg.exe and avg.msi in open malware repositories.
I searched the hashes in AnyRun, Malshare, Malware Bazaar, and Google. Finally, I hit the jackpot with Hybrid Analysis which allows registered users to download samples!

The next step was to download the file and trigger an execution on AnyRun, which should provide easy access to all the samples within this ransomware campaign.
Once I got my hands on the avg.msi sample, I ran it on AnyRun. There's quite a nifty trick in AnyRun that I only discovered when I laid my hands on a premium account. It is possible to increase the machine run time by clicking the button Add Time at the top right. For a free account, it increases the run time from 1 minute to 5 minutes which changes quite a bit.
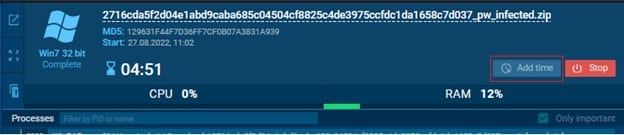
Anyway, I ran the sample, and, what do you know?! I found the entire infection process with all the missing files!
Here is logon.bat, which was missing in Virus Total.
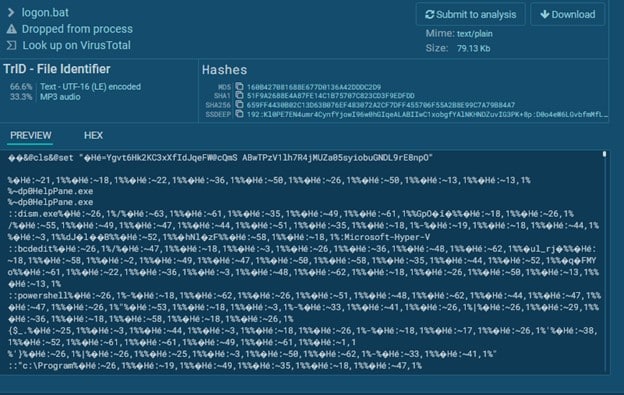
Here is the ransomware note:
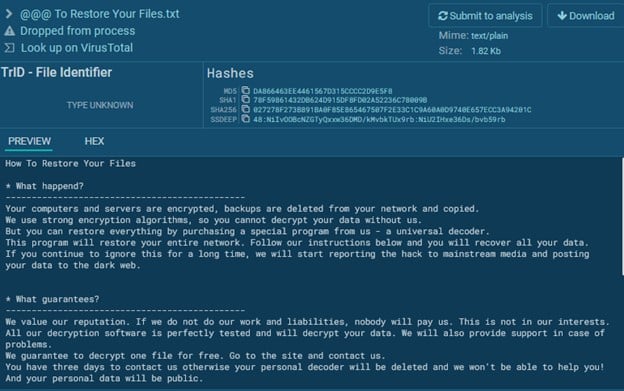
Chapter Three – The Malware Attribution Process
Sadly, this chapter will be quite short.
Spoilers! I couldn't find the actor responsible for this ransomware.
I first tried to upload the ransomware note to ID Ransomware, which can attribute ransomware notes to ransomware actors by just uploading the ransomware note. ID Ransomware claimed that this ransomware note belonged to Nemucod.
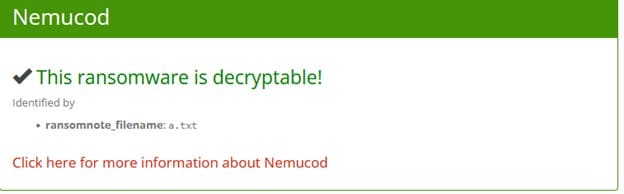
Yet, I was doubtful. So I uploaded the ransomware file svchost.exe (since, by then, it was on Anyrun, I could download it for free) to Intezer, which offers a community account version. Intezer attempts to attribute files to malware and malicious actors by code "genes."
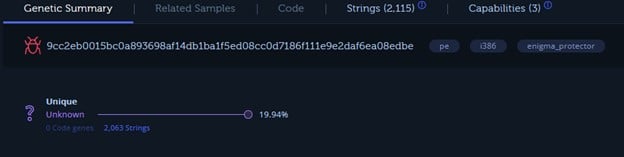
That also wasn't very helpful. Well...I did my best right?
See you guys next time!
Thanks to @1ZRR4H, who took a good look at the ransomware note and saw that the TOX-ID in the ransom note is the same one found in Rever Ransomware notes. A simple google search of the TOX-ID confirms it:
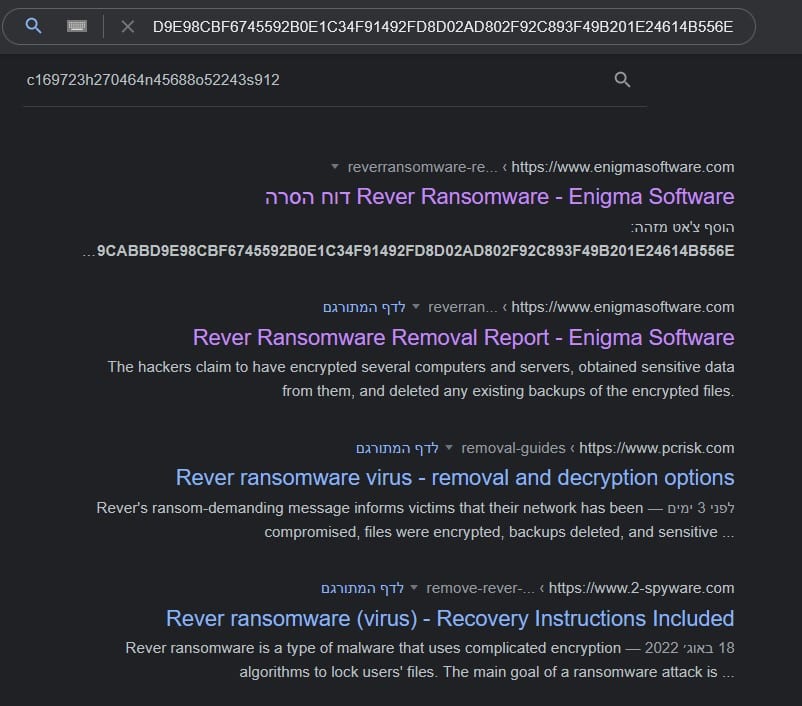
@Amigo_A_ has written about Rever ransomware. Read more about Rever Ransomware here.
Chapter Four – IoC appendix
AVG.MSI - b6373b520a21c2e354b805d85a45a92d
AVG.exe - 44961feb7fd9eeabdb67e5eeb15b9c8a
HelpPane.exe - d33dac29513dcc1027f29d5e9e901369
Svchost.exe - 5143bbdf1f53248c7743f8634c0ddbc1
Logon.bat - 160b427081688e677d0136a42dddc2d9
Mhyprot2.sys - 4b817d0e7714b9d43db43ae4a22a161e
-------
To see how Cymulate can help your organization stay protected against the latest malware attacks, book a demo today.



