Reducing Attack Surface with Exposure Management and Attack Path Discovery

Key Takeaways
- Reducing your attack surface is essential for limiting opportunities attackers can exploit, but traditional methods alone aren’t enough.
- Static checklists and one-time reductions fail in today’s dynamic, cloud-first environments.
- Exposure management elevates attack surface reduction by continuously validating, prioritizing and remediating exposures.
- Attack Path Discovery from Cymulate reveals how attackers could move laterally and reach critical assets, while Exposure Management with validation ensures defenses actually work.
- Validated reduction of the attack surface aligns security and IT efforts, improves ROI and measurably strengthens resilience.
Every new endpoint, cloud workload and third-party connection expands an organization’s attack surface. In simple terms, this is the collection of potential entry points adversaries can exploit. Reducing attack surface has always been a foundational cybersecurity practice: the fewer paths available to attackers, the fewer opportunities they have to succeed.
Yet in sprawling digital environments, shrinking the attack surface isn’t as simple as patching systems or tightening access controls. Cloud services, hybrid work and supply chain complexity create exposures that shift constantly.
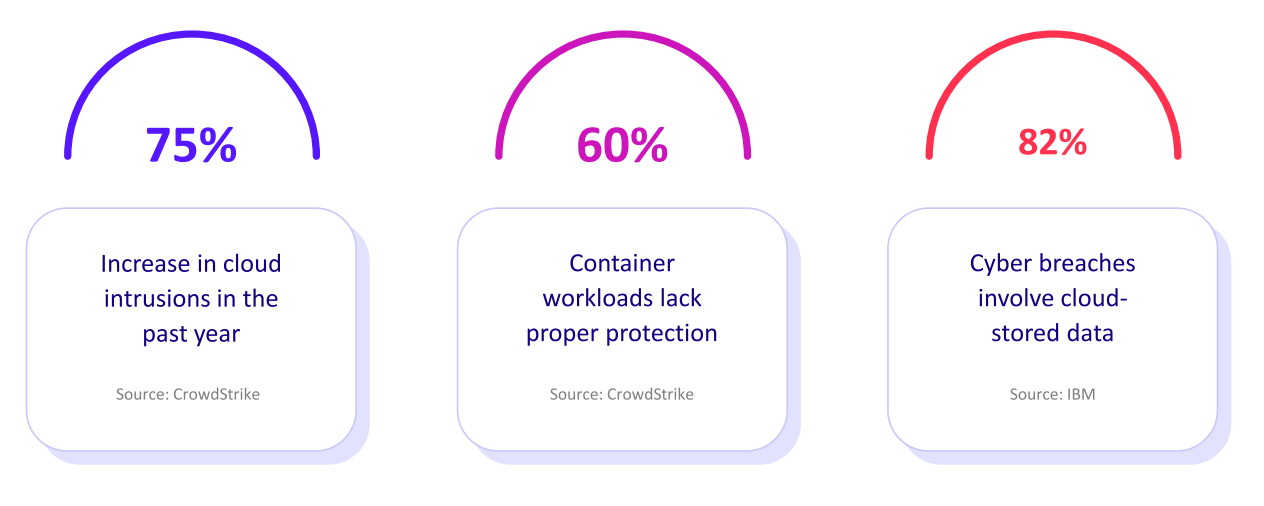
The Cymulate approach reframes the challenge: attack surface reduction is necessary, but its true value comes when it is validated, operationalized and continuously managed with Exposure Management.
What Does Reducing Attack Surface Involve?
At its core, attack surface reduction means eliminating unnecessary opportunities for attackers. Security teams achieve this by:
- Minimizing services and applications through disabling unused protocols, closing unnecessary ports and removing redundant software.
- Patching and updating systems by addressing known vulnerabilities before adversaries can exploit them.
- Strengthening access control by enforcing least privilege, implementing MFA and tightening identity governance.
- Network segmentation through isolating sensitive assets to limit lateral movement.
When done well, these practices:
- Reduce exploitable vulnerabilities and misconfigurations.
- Shrink the number of attack vectors adversaries can target.
- Simplify security operations by focusing defenses on fewer more manageable areas.
Here are some different ways an organization can achieve attack surface reduction:
Hardening Configurations and Systems
Through securing operating systems, applications, cloud platforms and user devices, the attack surface is reduced by applying best practices and disabling unsafe defaults. This is done through turning off default passwords, enforcing encryption and removing risky features.
Patch management is also critical, since breaches result from unpatched vulnerabilities. Hardening even applies to user settings, such as by removing local administrator rights. With a hardened system, attackers have fewer chances to gain access.
Eliminating Unnecessary Services, Ports and Assets
Unused or outdated systems often expand the attack surface and leave you vulnerable. Every open port, exposed service or forgotten app could be a potential risk. Security teams must audit and remove these unnecessary elements.
Publicly exposed admin interfaces could also be high-risk and should be removed or restricted. Reducing to only essential services and securing them limits these easy points of entry.
Implementing ASR Rules and Policies
Some platforms offer predefined rules to block high-risk behaviors. Microsoft Defender’s rules can prevent malicious scripts in Office apps or block unauthorized downloads, for instance.
These policies limit how software behaves, making vulnerabilities more difficult to exploit. Organizations can also create custom rules, like disabling macros or enabling allowlisting. While these need to be balanced with usability, they can prevent entire categories of attacks.
Reducing Privilege and Access
Too many high-privilege accounts increase risk. Reducing your attack surface means applying the principle of least privilege: users and systems should only have the access needed to perform their necessary tasks.
Limiting admin rights, reviewing unused accounts and enforcing multi-factor authentication helps reduce identity-related exposures. Just-in-time access and monitoring for unusual behavior further strengthen this layer.
Disabling Lateral Movement Paths
Flat networks make it easy for attackers to move between systems once inside. Network segmentation divides systems into isolated zones. This limits the spread of attacks by requiring extra steps for each move.
Sensitive databases might only be reachable from certain app servers, for instance. Firewalls, access controls and disabling legacy protocols like SMBv1 can all help stop lateral movement. A segmented network reduces the overall surface by creating contained zones of exposure.
Deprecating Legacy and High-Risk Systems
Old systems sometimes lack support and remain unpatched, making them frequent, easy targets. Organizations should identify outdated systems and either retire, upgrade or isolate them. Legacy devices can be restricted to segmented zones with limited access.
When removal isn’t possible, use virtual patching, strict controls and continuous monitoring. Many attacks target known flaws in legacy systems, so minimizing their use is critical in reducing risk.
Challenges with Traditional Reduction
Despite its importance, traditional approaches to reducing attack surface fall short in modern environments.
- Static checklists can’t keep up. Traditional frameworks rely on hardening guides and compliance checklists. These help with baseline hygiene however they fail to capture dynamic exposures that arise with new software deployments, cloud integrations, hybrid work environments or shadow IT.
- Cloud and remote sprawl create blind spots. With workloads shifting between on-premises, SaaS and multi-cloud providers, organizations often don’t have a full view of their attack surface. Missing visibility equals unaddressed exposure.
- Reduction without validation isn’t resilience. Closing a port or applying a patch doesn’t guarantee an attacker can’t still find a way in. Without testing whether controls actually block threats, organizations risk a dangerous gap between theory and practice.
In short, attack surface reduction without continuous validation leaves organizations with a false sense of security.
Exposure Management Elevates Attack Surface Reduction
Exposure management transforms the process of attack surface reduction. Instead of static, one-time reduction efforts, exposure management establishes a continuous cycle:
Identify → Validate → Prioritize → Remediate
- Identify all potential exposures across on-premises, cloud and remote environments.
- Validate whether these exposures are exploitable in real-world attack scenarios, not theoretical ones.
- Prioritize based on business impact, risk context and attacker feasibility.
- Remediate with evidence that changes measurably reduce risk.
The difference is profound. Reduction efforts are no longer guesswork because they are continuously stress-tested against actual attack techniques.
The Threat Exposure Validation Impact Report 2025 from Cymulate highlights the benefits of this approach:
- Organizations using exposure validation saw a 47% improvement in mean time to detection across critical attack vectors.
- 97% of respondents who use automated security control validation and measure cyber program effectiveness have seen a positive impact since implementation
By tying reduction directly to measurable resilience outcomes, exposure management moves organizations from theory to operational confidence.
Cymulate Attack Path Discovery & Exposure Management
The Cymulate Exposure Management Platform is designed to operationalize attack surface reduction by combining Attack Path Discovery and Exposure Validation capabilities.
Attack Path Discovery
Attackers rarely stop at the first foothold. They pivot laterally and escalate privileges until they reach critical assets. Within the Cymulate Exposure Management Platform, Attack Path Discovery:
- Maps how attackers could move through networks and systems.
- Reveals privilege escalation opportunities and chained exposures.
- Identifies “crown jewel” pathways that represent the highest business risk.
Cymulate Attack Path Discovery applies an assumed-breach approach to test and validate how effective security policies are limiting and/or preventing privilege escalation and lateral movement. Illustrated attack paths visually show the chain of exploitable steps an adversary could take to reach critical assets and act maliciously.
With Attack Path Discovery, the Cymulate Exposure Management Platform delivers:
- Attack Path Mapping – Automatically generates attack path maps starting from initial agent to every asset successfully reached
- Lateral Movement Insights – Shows how adversaries can use compromised credentials to move deeper in the network without being detected or impacting operations
- Security Control Exposure Analysis – Validates the effectiveness of your security policies across segmentation, firewall rules, endpoint protection and access controls
Learn more about Cymulate Attack Path Discovery.
Exposure Validation
Not every potential exposure is exploitable. Cymulate Exposure Validation proves which exposures matter by:
- Testing whether existing controls block real-world attack techniques.
- Providing out-of-the-box, automated attack templates such as SMB Pass-the-Hash and LLMNR Poisoning.
- Showing evidence that remediations and patches have the intended effect.
Validation ensures security teams spend time on exposures that attackers can truly exploit instead of theoretical risks.
Recognition and Customer Proof
The Cymulate approach to exposure validation and attack surface reduction has earned recognition in the industry:
- Named a Leader in the Frost Radar™ for Automated Security Validation.
- Named a Customers' Choice by Gartner® Peer Insights™ 2024 Voice of the Customer for Breach and Attack Simulation Tools
- Rated highly on Gartner® Peer Insights™, where customers emphasize how Cymulate helps them “reduce the blast radius” of potential incidents.
By combining attack path visualization with validated exposure testing, Cymulate delivers a level of clarity through and confidence exposure management traditional reduction efforts can’t match.
Business Impact of Validated Attack Surface Reduction
For CISOs and security leaders, validated reduction goes beyond just a technical win. It’s a business enabler. Reducing your attack surface allows you to:
- Prioritize critical mitigations. Instead of spreading resources thin across thousands of theoretical vulnerabilities, teams can focus on exposures that matter most to attackers and the business.
- Align IT and security with evidence. Validation results provide common ground for IT operations and security teams to agree on what needs fixing first.
- Maximize ROI. By targeting high-risk assets and attack paths, organizations reduce wasted effort on low-impact fixes and improve return on security investments.
- Build cyber resilience. Continuous validation ensures the attack surface stays reduced, even as environments evolve.
These outcomes provide measurable resilience that executives and boards can see and trust, and that will help your organization meet compliance and regulatory requirements.
Try Cymulate Exposure Management Today
Reducing attack surface is foundational but is only the beginning. Resilience requires more today than removing vulnerabilities and closing ports. It requires validating that defenses hold up against real-world threats, continuously managing exposures and prioritizing efforts based on business impact.
The Cymulate Exposure Management Platform, with Attack Path Discovery and Exposure Validation, enables organizations to move beyond theory. By operationalizing attack surface reduction, you’ll deliver continuous, measurable resilience that keeps pace with evolving threats.
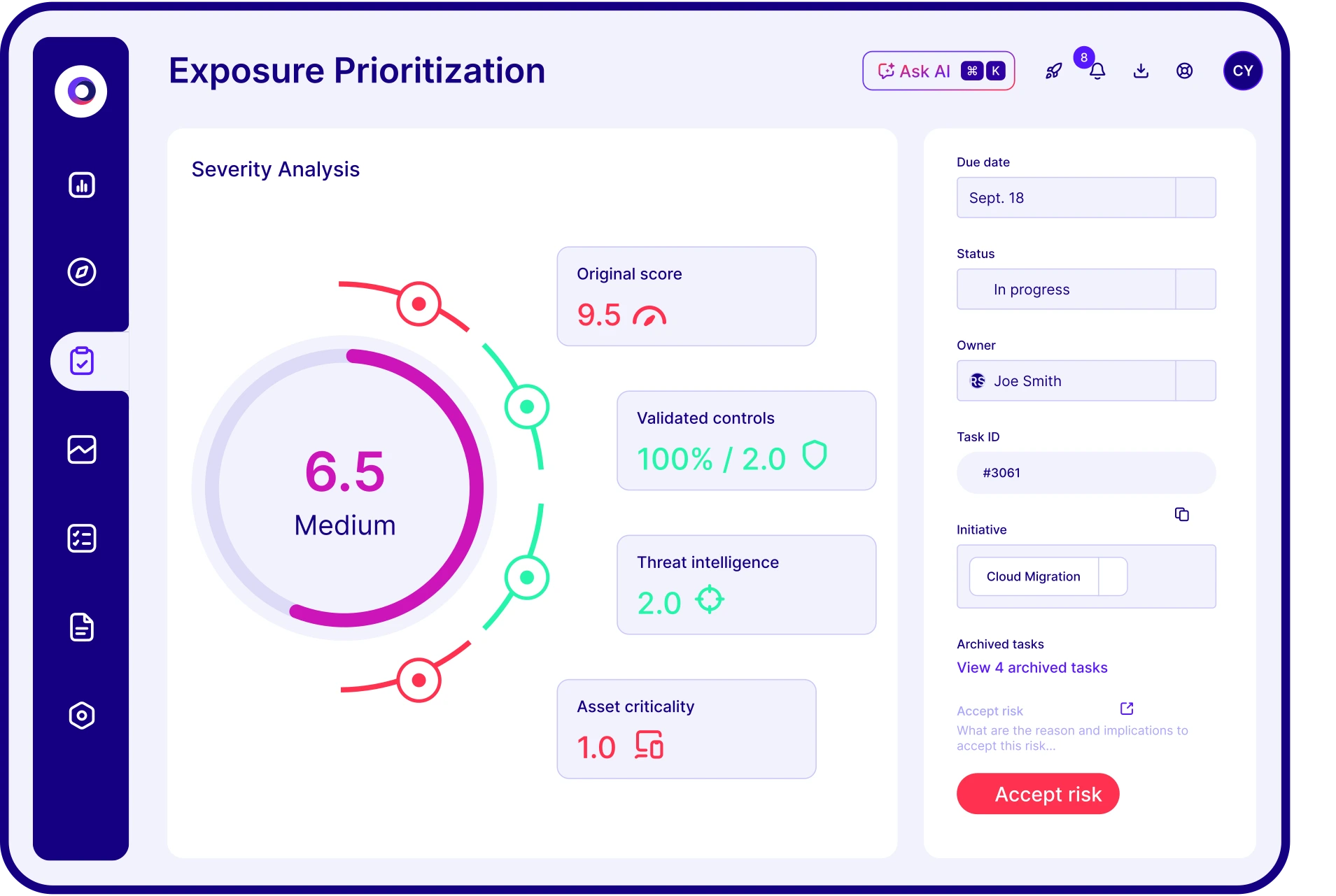
Download the Threat Exposure Validation Impact Report 2025 to see how organizations are handling threat exposures in today’s environment.
Request a personalized demo to experience how Cymulate can help your team minimize risk and strengthen security.