The Future of Exposure Validation is Here

Advanced product innovation from the new Cymulate platform
The recent update of the Cymulate Exposure Validation Platform introduces new features and functionality that enable organizations and their security leaders to test and optimize security controls to maximize threat prevention and detection. This allows them to reduce the likelihood of a successful cyber attack and significantly lower the risk of a material cyber breach. Organizations can now improve their security posture and optimize their existing security technology investments to reach and maintain an acceptable level of risk based on their business context.
This update includes new features as well as workflow changes that make it simpler and more efficient to create the assessments you need to test and validate the threats that concern you the most. Whether it’s how well your security controls prevent and detect ransomware threats or how your security team responds to a specific threat actor or APT group targeting your industry, you can quickly and easily run automated, scheduled attack simulations and red team exercises that provide frequent (weekly) insights and mitigations to reduce your threat exposure.
Delivering a streamlined assessment experience
As cyber threats grow in complexity, organizations are under pressure to strengthen their defenses and stay ahead of potential attacks. This next release of the Cymulate platform is designed to meet that need, offering a more streamlined approach that delivers consistency, flexibility and efficiency to create and execute the assessments you need to evaluate your security posture and optimize your security defenses.
Cymulate has transformed how you conduct security assessments, providing a unified platform that validates the security controls across your security technology stack. Now, you can evaluate threats and campaigns with a single, streamlined assessment that runs across all relevant controls. This approach enables you to simulate both security control best practices and complex full kill-chain cyberattacks across your entire security infrastructure. Together, this gives you a holistic view of your security posture with robust coverage across an expanded range of security controls.
Contextual Assessments
The new platform provides the flexibility to create highly contextual assessments across your security controls for the attack vectors that concern you the most. For example, a single assessment can determine how well you are protected from new (last 6 weeks), high-risk, ransomware variants on your Windows platforms. This latest release removes the previous module dependency meaning you can now run a single assessment across multiple modules and receive a unified report of the findings for all controls. This enables full kill-chain attack scenarios across multiple security controls with a more consistent, streamlined and flexible assessment experience for users of the Cymulate platform.
Attack Scenario Workbench
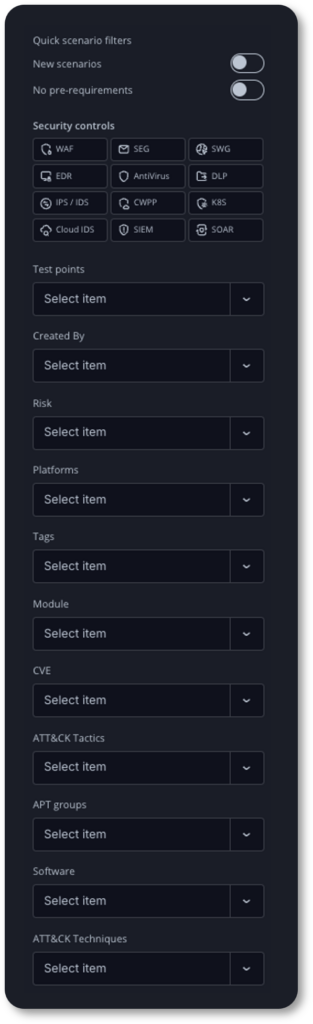
Contextual assessments are created using the new attack scenario workbench. The workbench provides a simple interface to filter and select attack scenarios to create an assessment from more than 100,000 real-world attack simulations and malicious actions from the threat actor's playbook.
Security teams can easily create fully automated assessments that test and validate security controls and operational responses to the latest emergent threats. This flexible user interface allows security teams to create new assessments and custom attack actions (scenarios) across multiple security control vectors to validate things like:
- Ransomware and malware variants
- APT group campaigns
- MITRE ATT&CK tactics and techniques
- Known vulnerabilities (CVEs)
- Risk level (Critical, High, Medium, Low, Info)
- Platform (Windows, Mac, Linux, Cloud, plus 40 more)
Cymulate customers can use the workbench to run multiple searches against the attack simulation library, selecting the scenarios they want to include in an assessment or as a template.
Unified Risk-based Scoring
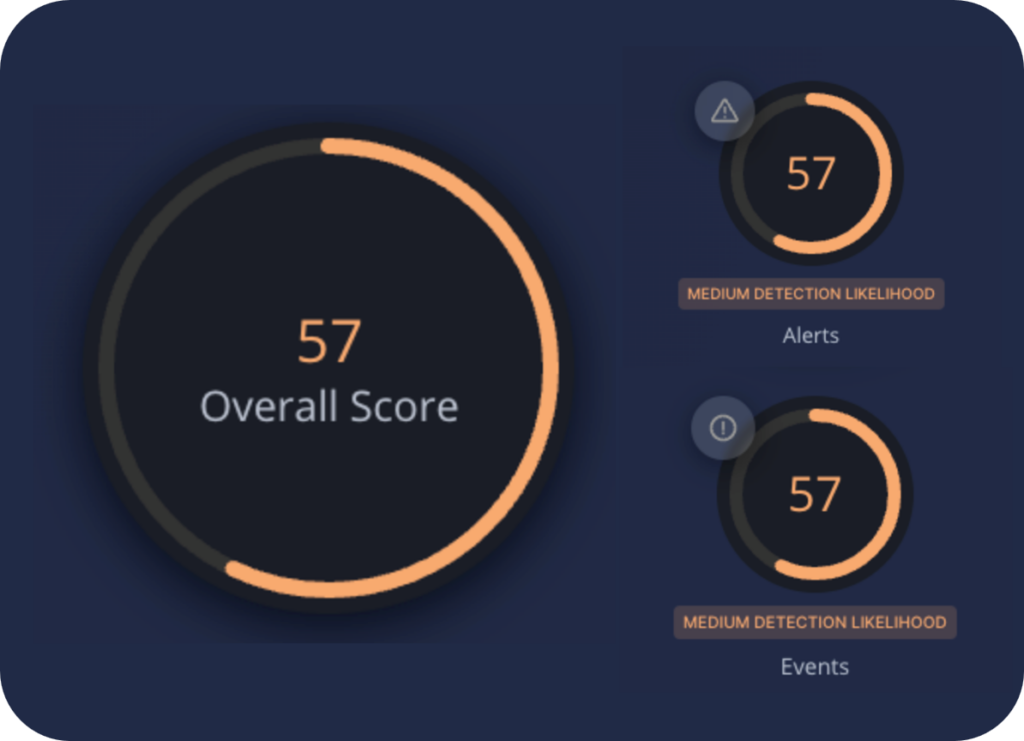
The Cymulate platform operates off a consistent scoring approach based on the weighted average of risk and findings. The lower the score, the lower the risk using the following scale:
- 0 – 10 = Minimal Risk
- 11 – 33 = Low Risk
- 34 – 67 = Medium Risk
- 68 – 100 = High Risk
The risk score represents the likelihood of a successful attack with a score of 33 or lower, generally considered an “acceptable level of risk” by Cymulate. Every organization can establish their own baseline for what they consider an acceptable level of risk based on their business context.
Security Posture Dashboard
The main Cymulate dashboard provides high-level insight into your risk level and prevention ratio across each phase of the attack life cycle. In addition, you have an overall risk score for the detection ratio of alerts and events captured in your SIEM environment.
This dashboard enables security teams to answer questions about their security posture and cyber-risk level against active threats with confidence.
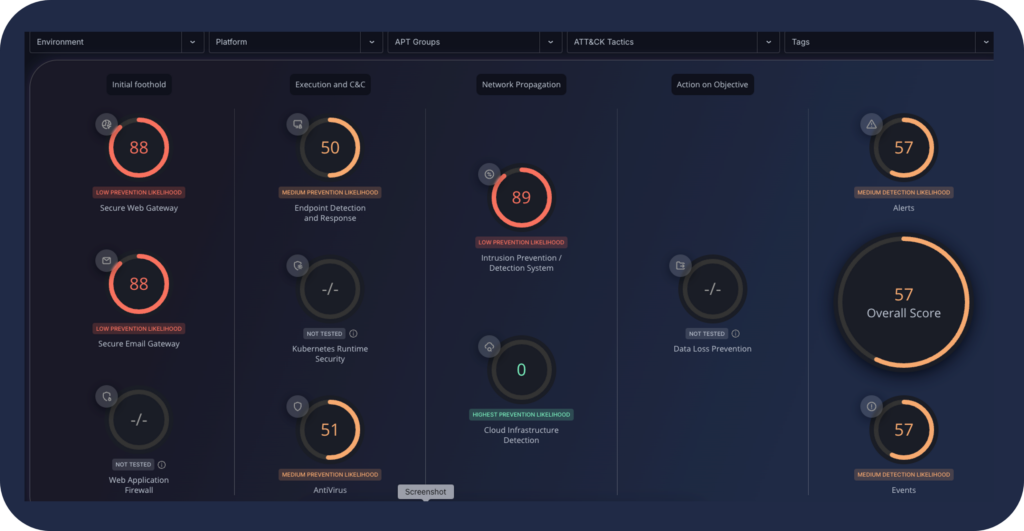
From this dashboard, you can quickly apply filters to look at specific environments and attack vectors including:
- Environment
- Platform
- APT Groups
- ATT&CK Types
- Tags (e.g. Ransomware)
The overall score provides strong support for detection engineering to capture the alerts and events that indicate potential malicious activity is occurring in your IT environment. The absence of detections does not mean the absence of a threat actor, so validating your SIEM detection ratio is a critical step in identifying and stopping threat activity before it can lead to a material cyber breach.
For organizations looking to understand their cyber risk, the dashboard gives a true indication of the likelihood of a successful attack.
AI-guided Validation Strategy
The new platform release offers AI-guided scoping to streamline the generation of assessments aligned to your validation strategy. AI-powered insights guide and customize your validation assessments that are tailored to your business needs and the security resources you have available.
The AI interface allows for natural language prompts to customize exposure validation templates and schedule assessments based on your desired frequency. You can tailor your validation strategy by industry, geography, compliance framework, security controls, team size (resources) and more. The output delivers simulation-ready exposure validation templates, testing schedules and more, giving you a guided experience to go from specific business requirements to a focused assessment configuration in minutes.
Focused execution for the threats and environments that matter most
The Cymulate Exposure Validation Platform enables security teams to focus the execution of assessments to test and validate how well protected they are against specific threats and APT groups targeting their region / industry and to evaluate the risks to the environments that matter most to their business. The following new and expanded features in this release
Expanded Security Controls
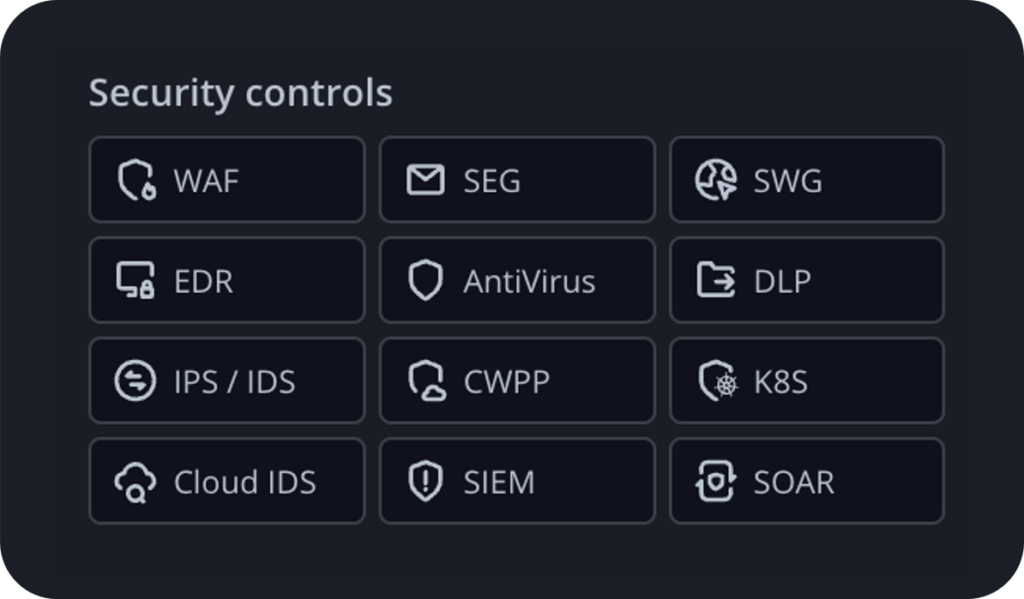
The latest platform release offers an expanded list of security controls that can be selected and used to filter attack scenarios for one or more controls in the scenario workbench.
This flexibility removes the module dependencies that existed in prior platform versions, enabling a more streamlined approach to assess specific threats across multiple security controls.
New control selections have been added to the platform making it easier to select attack scenarios that validate network security controls, cloud security controls and SIEM / SOAR alerts and events.
- IPS / IDS scenarios validate network intrusion prevention / detection
- CWPP scenarios validate cloud workload protection platforms
- K8S scenarios validate high privilege threat activity in containers running Kubernetes
- Cloud IDS scenarios validate threats in cloud infrastructure is detected by your SIEM
Using the SIEM / SOAR attack scenarios, security teams can gain deep insight into the detection ratio of alerts and events within their SIEM / SOAR environment. Security teams can enhance their threat detection and threat hunting capabilities while security engineers can accelerate the process of detection engineering using the Sigma rules that are generated by the Cymulate platform to improve their detection ratio.
Custom Attack Scenarios
This valuable new feature enables security teams to upload their own attack resources to the resource library to create custom scenarios and assessments specific to their business context.
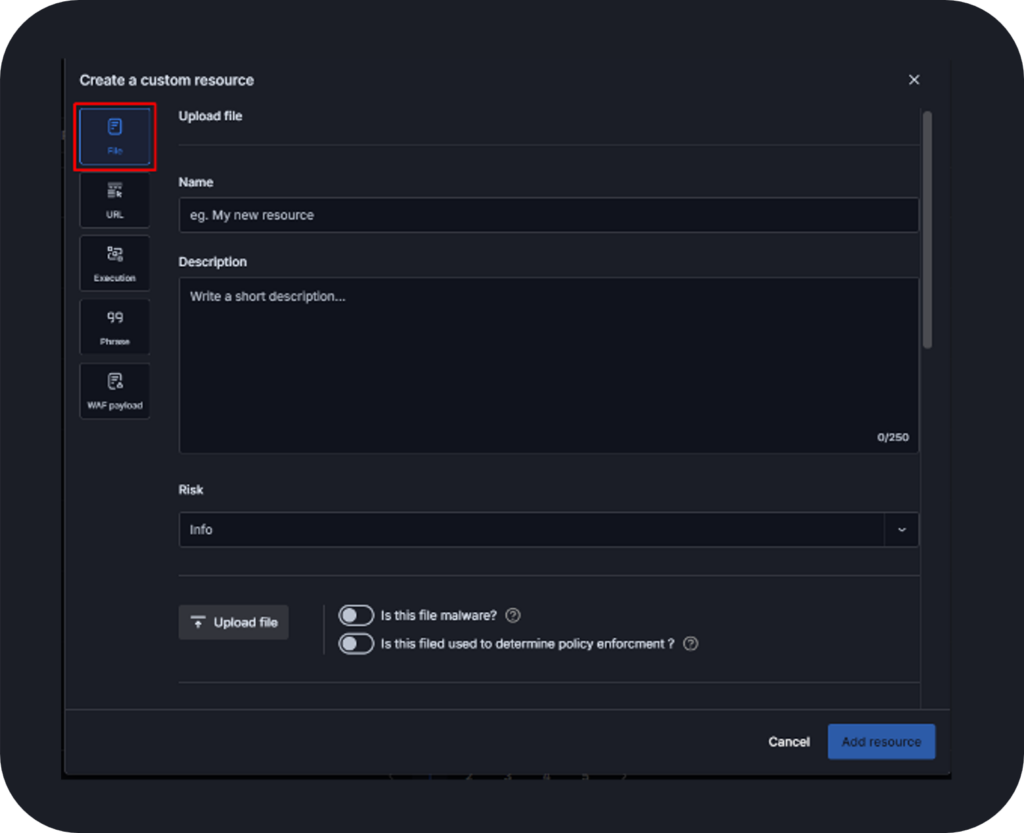
The resources section is a central hub for managing essential components used in scenario creation, offering both predefined and custom resources to tailor simulations to specific needs. Resources are categorized into multiple key types:
- Files used for testing email and web gateways, EDR, AV and DLP controls
- URLs for assessing phishing, malicious links and web security policies
- Executions enabling advanced attack simulations through scripts or YAML imports
- Phrases applicable in exfiltration and DLP testing to detect sensitive data leaks
- WAF Payloads designed to evaluate web application firewall (WAF) defenses
Each resource can be tagged for easy categorization, improving organization and alignment with various security assessments.
Daily Threat Feeds
The daily threat feed extends the functionality of immediate threat assessments based on the latest threat actor campaigns. The Cymulate threat research team loads attack simulations into the platform on a daily basis with feeds from the cyber community including CISA. These assessments can be configured for auto-run, with notifications to security leaders whenever they are exposed to one of these immediate threats. The platform provides mitigation guidance and detection rules to help organizations protect against these new threats.
Smart Templates
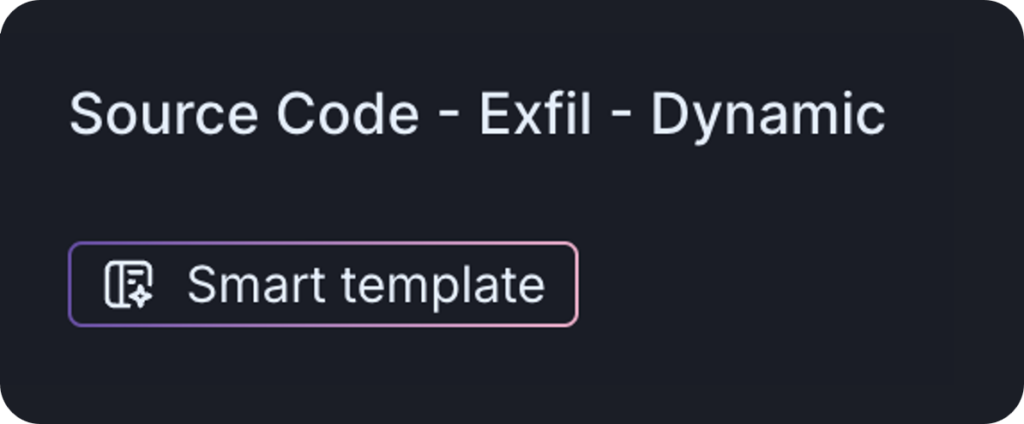
Smart templates are a new feature added to this latest release. The new smart templates are dynamic, meaning any new attack scenarios added to the workbench that match the criteria used to create the assessment template will be automatically included the next time the assessment gets launched.
This feature makes it more efficient to run frequently scheduled assessments that dynamically include new attack scenarios at launch.
Simplified delivery that saves time and effort
In addition to creating a more streamlined experience with focused execution, we have also introduced new features that simplify delivery to save security teams time and effort.
- Ad-hoc assessment and replay: Quickly launch an existing assessment on an ad-hoc basis when you need to recheck the effectiveness of any mitigation actions you have implemented.
- Preview templates and scenarios: View detailed scenario information prior to the launch of an assessment.
- Pause and resume assessments: Pause and resume assessments for better control of assessment execution.
- Assessment tags and comments: Add tags and comments to your assessments and templates.
Defending against the threat actor’s playbook
The attack scenario workbench provides access to the industry’s richest library of threat actor tactics and techniques so you can validate how your defenses will stand up against the threat actors playbook. The Cymulate Exposure Validation Platform is a best-in-class solution that delivers key outcomes for:
- Security control validation
- True threat exposure awareness
- Automated offensive testing at scale
The new platform release provides a more streamlined user experience that makes our customers more efficient when validating security controls and operational responses to the latest emerging threats. We empower users to mitigate security control weaknesses using the recommendations from the Cymulate platform.
For more information on how Cymulate can help you focus on true threat exposures and reduce your cyber risk, download our platform data sheet and schedule a demo of the Cymulate Exposure Validation Platform.



